
It became known that users of the major messaging apps can be in danger of the potential phishing attacks masqueraded as the legitimate looking links. Several leading messaging and email platforms including Facebook messenger, Signal, Whatsapp, Instagram and iMessage now present it’s users with a possibility of getting phished via URL changing trick.
Where does the trick hide?
Cybersecurity specialists confirm that the vulnerability has been potentially exploited for the past three years and it’s still present in some of the mentioned apps.
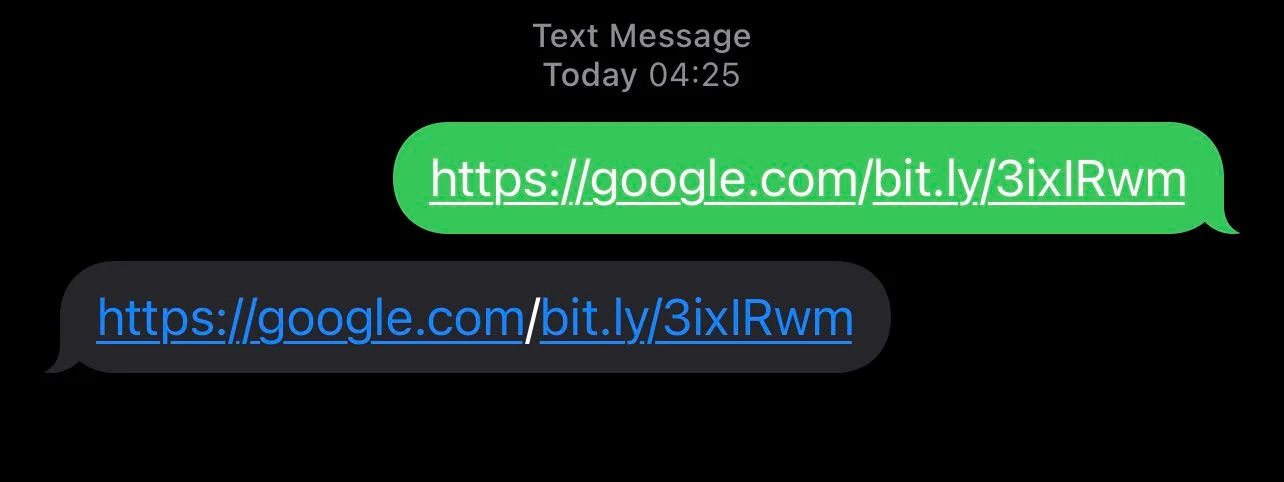
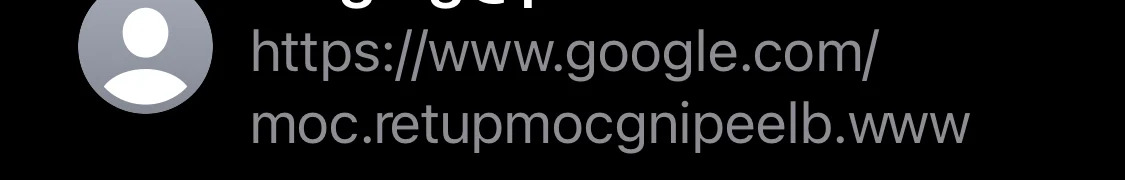
As a result of the app’s interface incorrectly displaying URLs with injected RTLO (right to left override) Unicode control characters it makes the user vulnerable to potential URI spoofing attacks.
Predominantly used for the display of Hebrew or Arabic messages the injection of an RTLO character in a string causes a messaging app or a browser to display it from right-to-left not as its normal left-to-right orientation.
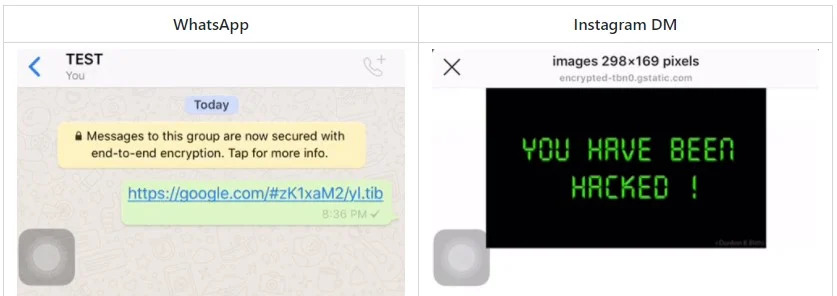
The exploit, a one liner, abuses Android and iOS trust of gTLDs and their support for the display of bi-directional text. So the principal is as simple as a copy and paste you just have to insert a single control character ‘\u202E’ between two URLs.
After you’ve injected RTLO control character the URL will get reversed because now the text is treated as “right-to-left” language (Arabic, Hebrew, etc.)
So, for example, threat actor can create”‘gepj.xyz” link but with our trick it turns into innocent looking “zyx.jpeg”, the same “kpa.li” would become “li.apk” pretending to be a legitimate APK file. In such a case a link can direct the user to whatever destination it can be.
On the first look, such a phishing URL will look like a legitimate subdomain of google.com. or apple.com.
What researchers say on the vulnerability?
The vulnerability received it’s assigned CVEs in the following versions of IM apps:
- CVE-2020-20096 – WhatsApp 2.19.80 or prior for iOS and 2.19.222 or prior on Android;
- CVE-2020-20095 – iMessage 14.3 or older for iOS;
- CVE-2020-20094 – Instagram 106.0 or prior for iOS and 107.0.0.11 or prior on Android;
- CVE-2020-20093 – Facebook Messenger 227.0 or prior for iOS and 228.1.0.10.116 or prior on Android.
Signal doesn’t have it’s assigned CVE ID because the company was informed not so long ago.
“Turn off link previews in everything, especially mail apps and anything related to notifications. Don’t visit weird websites with popups. Don’t click random prize giveaways,” researchers from Sick.Code advise to users of the mentioned apps where the fixes has not been applied yet
So, how did this happen that such a nuance of a vulnerability had been missed by the cybersecurity community? The reason might be that because of its being a nuance it was missed in all the more complex and dangerous vulnerabilities out there. Who knows?
In August 2019 a researcher named “zadewg” made the initial discovery of the vulnerability. Later a freelance security researcher from Sick.Code turned the attention on the vulnerabilities when they were published in CVE Program on Twitter.
Sick.Codes researcher contacted “zadewg” to ask if they made the repository public or not. The researcher only responded with a surprise that the CVEs has been released only now and didn’t show any wish to share more information about the method of exploiting vulnerabilities.
But two researchers agreed on sharing PoC ( proof of concept) on GitHub. The one-liner PoC is publicly available and anyone even with little technical knowledge can try to test it.
For those interested, there are a whole bunch of other RTLO based exploitation techniques involving even more complex technical concepts.
For the users of the affected apps, researchers advise to be exceptionally cautious when receiving messages that contain URLs, always click on the left side of any URL received and keep a watch on the upcoming updates that should address the issue.
Cybersecurity specialists assume that this phishing kind of an attack could possibly affect many other IM and email apps but once more — only those mentioned in the article have been confirmed to have the problem.
Telegram was also reported to have this kind of vulnerability but its developers were the first to address the issue.
The one interesting thing that is left to mention is how developers will exactly address the issue as the RTLO Unicode characters have a legitimate use because any fix potentially can mess with its legitimate functionality.
What to say more on the phishing issue?
And here will be presented to your little bit of knowledge base concerning phishing. Everyone knows or has the general understanding of what phishing is.
According to Wikipedia, phishing is a type of social engineering attack in which an attacker sends a fraudulent deceptive message with intentions to trick a person into revealing sensitive or confidential information to the attacker. Sometimes it is also done to deploy malicious software on the victim’s machine.
In the article on the same site it reads that in 2020 phishing was the most common type of cyber attacks having double the incidents than any other type of cybercrime.
Phishing falls into different but with the same purpose types: voice phishing, social media phish, whaling, business email compromise (BEC), Microsoft 365 phishing and spear phishing.
To explain some of the mentioned types. Whaling means attackers’ intentions to target “big fish”, usually the CEO of some company to get via this person the much sensitive information that this particular target usually has access to.
And the spear phishing means attackers targeting specific person’s other than doing randomization of their attack. In this type of phishing cybercriminals can create more trustworthy looking phishing messages as they often do a little research on their future victims. According to the SANS institute, 95 percent of all attacks on enterprise networks comes from spear phishing.
Talking about tips on how to avoid phishing, although there could be written a long list in detail or without them, I personally think that the best rule, as with every scammer or related, would be to always listen to common sense.
Think if that email was really intended for you or could it be possible to receive such a type of message from your bank as an example? Be cautious, don’t go instantly after receiving a message with a first click.
