
Researchers from BlackBerry report about a new identified ransomware family. LokiLocker RaaS has recently come out on the scene and as cybersecurity experts say it doesn’t hold the Norse god’s name for nothing. In an extensive article researchers gave the detailed dig up into LokiLocker`s code, explained how the ransomware works and also wrote a short advice on how users can avoid the malware.
So, who`s the guy?
To speak about Norse mythology from all the gods out there, Loki, the god-trickster, may be the most interesting one. According to Brittanica, this deity could shapeshift and change its sex having the chaos as the aim. In Norse mythology Loki is portrayed to always have some trick up its sleeves. The same you can say about the namesake ransomware family.

First time researchers detected the malware in mid-August 2021. The team warned not to confuse this ransomware family with LokiBot (an infostealer) and with an older ransomware family Locky, which was mostly known in 2016. Though researchers add that LokiLock shares some similarities with the LockBit ransomware (like ransom note filename, registry values) but still one cannot say for sure the former is the direct descendant of the latter.
What`s there up the sleeves of the trickster- ransomware?
New ransomware family targets English-speaking users who work on Windows OS. Threat actors wrote the malware in .NET and protected it with NETGuard (modified ConfuserEX) additionally using a virtualization plugin called KoiVM. The plugin was once a licensed commercial protector for .NET applications but in 2018 its code became open-sourced ( the possibility says it was leaked) and now it is available on GitHub. Koi seems to be popular enough with cracks and hacking tools but researchers admit they have`t seen that much malware using it.
In the earliest samples observed, Trojanized brute-checker hacking tools such as PayPal BruteChecker, FPSN Checker by Angeal (Cracked by MR_Liosion) were used as ransomware distributors. For those who don’t know, brute-checkers are tools that threat actors employ when they need to validate stolen accounts and gain access to other accounts. The technique is called credentials stuffing. Researchers assume that the reason why in the beginning it were these hacking tools distributing the malware it’s maybe because threat actors conducted some kind of a beta testing before going to the wide market.
Now the malware works as a limited-access Ransomware-as-a-Service scheme engaging a rather small number of meticulously checked affiliates. For each affiliate is a designated username and a unique chat-ID number. Blackberry`s team for now counted about 30 different LokiLocker affiliates.
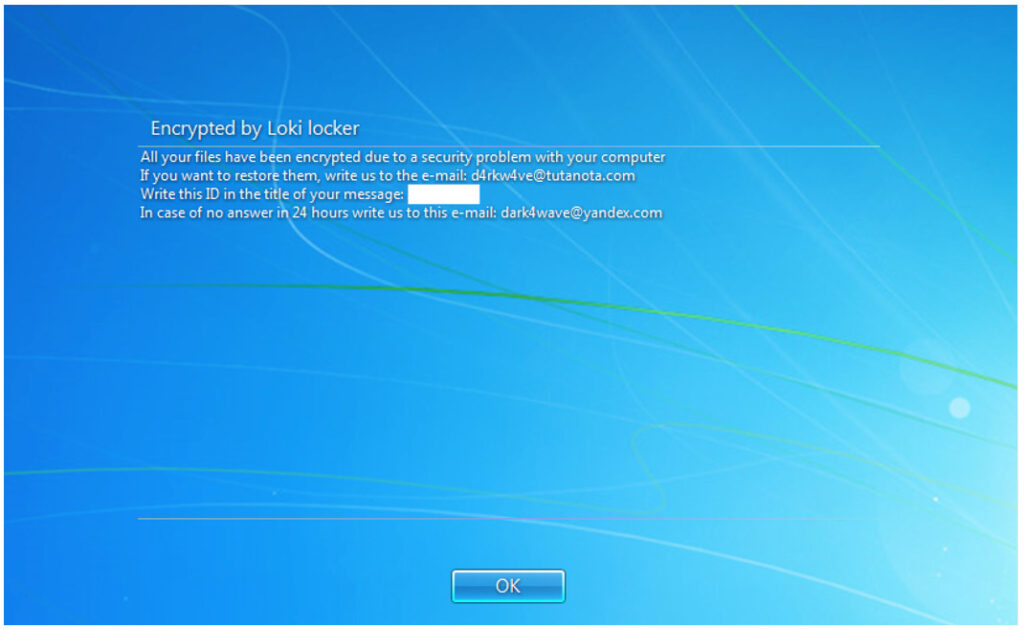
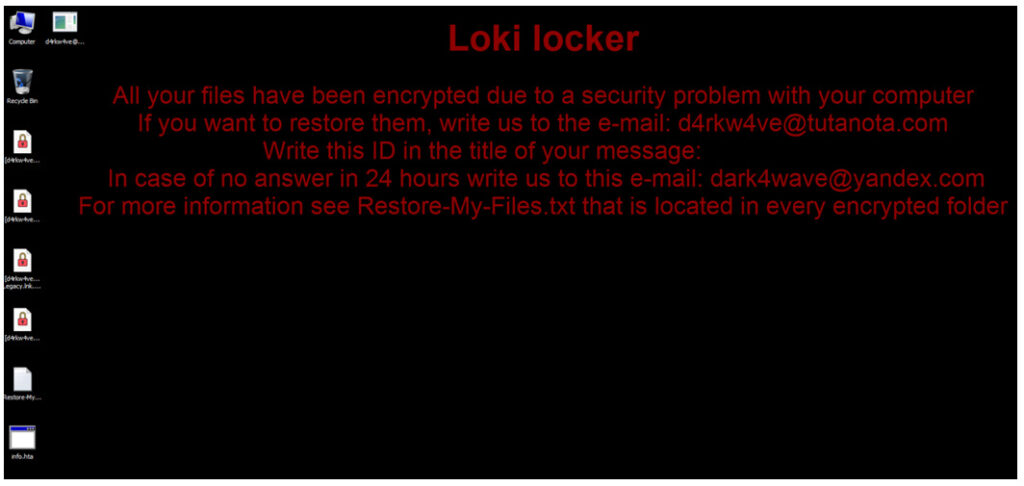
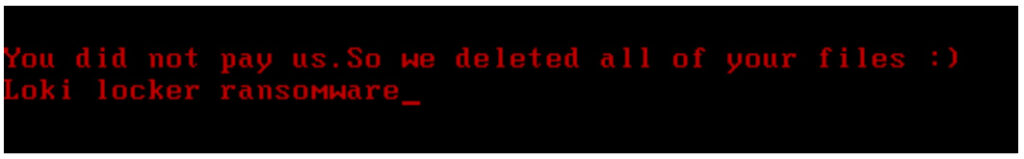
LokiLocker works the usual way for ransomware. It encrypts victim’s files on local drives and network shares and then asks the victim to pay the ransom. In case of getting a refusal to pay the demanded money, malware destroys encrypted files and renders the system to the completely unusable state.
Threat actors use a standard combination of AES for file encryption and RSA for key protection. The communication will take place via an email where criminals give the instructions on how to pay the ransom. When the terms of payment don’t meet, ransomware deletes all non system files and overwrites MBR.
Who’s behind LokiLocker?
It doesn’t seem that LokiLocker targets particular geography but researchers note that the biggest number of victims was from Eastern Europe and Asia. When analyzing the code they found out that of all the countries Iran was excluded from the targets. But the trick is that this part of the code doesn’t work.
When threat actors put such a non-target list in a code it’s usually the countries they personally don’t want to include or those that are loyal to their unlawful activities.
Iran might have been put in such an unfunctional non-target code list for the actual coverage of the ransomware origin, researchers think. But the waters could not get more muddy.
Researchers counted at least three unique usernames that LokiLocker affiliates used and those that can be found on Iranian hacking channels. Though the possibility also says it may have been done so just to put the blame on Iranian hackers instead of actual threat actors.
But the case might be that it is actually Iranian hackers who are behind the ransomware as some of the cracking tools used to distribute the very first samples of it seems to be developed by an Iranian cracking team called AccountCrack.
You could say it may be the Chinese or Russian hackers who are playing the cards but what has also been noticed is that all the embedded debugging strings are in English and largely free of language mistakes and misspellings. The research team says it’s not the usual norm for the programs originating from mentioned countries.
What to say in conclusion?
Newly appeared ransomware received its quite extensive analysis and the team made their conclusions.
First of all Blackberrie’s researchers make assumptions that the usage of KoiVM as a virtualizing protector for .NET applications can be a growing trend in the creation of malware. Although it’s quite an unusual method for complicating analysis.
The second, to be sure about the origins of the ransomware you can’t be. Some details hint at the Iranian authorship of LokiLocker but still we have the non-target list with Iran included though that part of the code doesn’t work.
And third, with a new cyber threat on the scene it’s better to write down some advice from people who know. Blackberry researchers kindly provided us with them. Although this days and age, these advices people should know like the “When it’s cold you should keep your body warm” thing. Obviously backup and once again back up. Backup your important info. Even more, keep the thing unplugged (preferably) and offline.
And don’t forget about general rules of cyber hygiene. It’s often we get our health problems from simply unwashed hands before dinner.
There’s no free tool to decrypt files encrypted by LokiLocker. If your files got encrypted by the ransomware, report the case to your local police authorities.
Don’t pay ransom. Not only you reimburse the criminal ecosystem but there’s no guarantee you get your files back or the ransomware won’t come back again because the possibility is that the criminals may have planted a backdoor in your device for easy access in the future.
