
Recently researchers from cybersecurity company Lumu Technologies published quite an informative flashcard on ransomware. In 2021 they collected 21,820,764 indicators of compromise that were related to one of the crucial steps of ransomware attack — ransomware precursor.
What is the ransomware precursor?
Specialists from Lumu Technologies note that ransomware attacks don’t come from nowhere. On the contrary these are often carefully and meticulously orchestrated. And the ransomware precursor being the important part of the whole ensemble.
Attack groups rely on these malware strains to collect the needed info on the targeted network and prepare the set up for the data theft and encryption. Here lies the possibility. Once detecting the ransomware precursor security teams can successfully stop the full blown ransomware attack.
A full-blown ransomware attack is the end result of a chain that starts with seemingly innocuous malware,” specialists from Lumu Technologies say in the Flashcard.
Shutting down any communications with malicious command-and-control servers will ensure that no further compromise will be done. With the help of precursor malware, threat actors move laterally across the network and receive access before actually deploying the malware that will steal and encrypt the data.
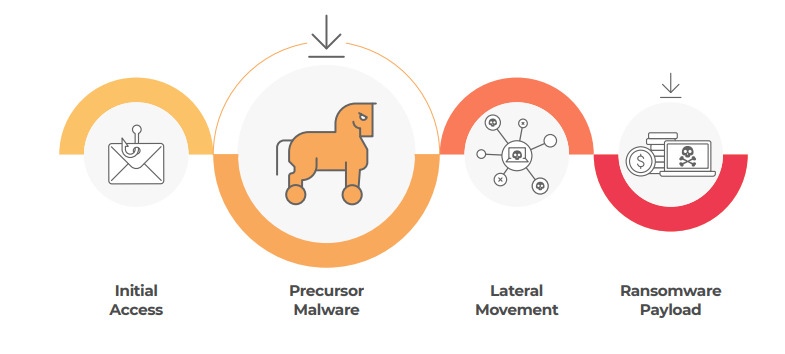
To simplify, a ransomware attack chain consists of initial access, it can be phishing, a vulnerability exploit or malware; then comes the precursor malware like Dridex, Emotet and TrickBot. And the final stage is the actual ransomware that steals and encrypts data.
Why is it not good to simply pay the ransom?
After encrypting the files the ransomware demands a ransom payment for the decryption key. Criminals write their ransom notes in such a way to persuade the victim that the only cheapest and easiest way is to pay that ransom.
But often cybersecurity specialists warn that nothing is cheap and easy here. On the contrary there’s more negative consequences of paying the demanded ransom.
The most obvious reason for fear can be that you don’t have any real guarantees that you will receive your files back. Although some threat groups graciously promise the return of the data.
Next, you also don’t have guarantees that there’s no left ransomware strain in your system. Imagine you have just paid the ransom and here it comes again. Your files are encrypted.
And third, in some countries there exist legal consequences of paying the ransom. In addition to the mentioned above you will get problems with the law.
Lumu Technologies statistics on ransomware precursor
Specialists from Lumu Technologies also collected a short statistics on what specific malware was being used as a ransomware precursor. This type of info will be very much helpful in the use of cybersecurity specialist that can “hunt” for concrete threat appearing.
Emotet, originally a banking trojan, evolved to include malware delivery and spamming took the first place making up three quarters of detected precursor malware in 2021. This malware works together in a ransomware chain with TrickBot to deploy Conti and Ryuk ransomware.
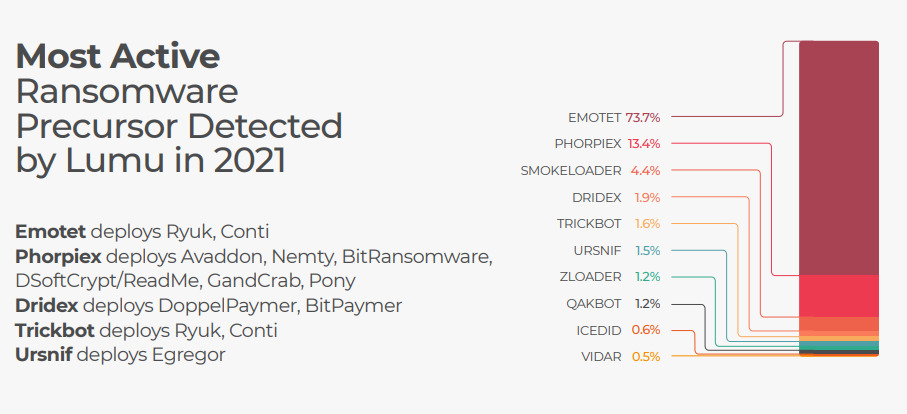
Phorpiex took the second place among the most detected precursor malware with 13% in 2021. In the past Phorpiex was used for cryptojacking, but now it is being used for the deployment of Pony,GandCrab, DSoftCrypt/ReadMe, BitRansomware, Nemty and Avaddon.
Dridex that has been known to be used for stealing bank credentials now deploys BitPaymer and DoppelPaymer. Ursnif has been seen to deploy Egregor.
