ESET experts talked about a banking Trojan Mispadu from Latin America that masks under McDonald’s ad for distribution.
The main goal of the Trojan is stealing money and credentials. It is interesting that in Brazil, the malware also spreads as a malicious extension for Google Chrome and is trying to steal bank card data and online banking, and also threatens users of the Boleto payment system.The Mispadu malware family was discovered during a study of banking Trojans in Latin America designed to attack users from Brazil and Mexico.
“The malware is written in Delphi and attacks its victims using the same methods as the Trojans Amavaldo and Casbaneiro that were previously discovered by experts. This is mainly the use of fake pop-ups and attempts to convince potential victims to provide confidential information to attackers”, – say ESET researchers.
Mispadu is spreading through spam and malicious advertising. The second method of distribution is not typical for Latin American bankers, so its researchers studied more details.
So, scammers started by posting commercial publications on Facebook, which offered users discount coupons at McDonald’s. By clicking on such an advertisement, a potential victim downloaded a ZIP file masked as a discount coupon and containing the MSI installer. Sometimes archives also contain legitimate software, such as Mozilla Firefox or PuTTY, but these are just decoys that are not used at all. By launching such an archive, the user, of course, does not receive a discount coupon, but a Mispadu banking trojan.
Interestingly, Mispadu operators used Yandex.Mail to store their payload. Apparently, the criminals opened an account on Yandex.Mail, sent a letter with a malicious coupon as an attachment to themselves, and then provided the victims with a direct link to this attachment.
On an infected device, Mispadu is able to take screenshots, simulate mouse and keyboard actions, and also intercept keystrokes.
“The malware can update itself through the Visual Basic Script (VBS) file that it downloads and runs. Mispadu also monitors the contents of the clipboard and tries to replace the addresses of Bitcoin-wallets that get there with the addresses of its operators, as Casbaneiro did”, – report ESET experts.
Nevertheless, after studying the purse of the attackers, the researchers concluded that so far these attempts have not been particularly successful.
Like other Latin American bankers, Mispadu collects detailed information about its victims: OS version, computer name, system language information, a list of Latin American banks installed in the application system, a list of installed security products, installation information for Diebold Warsaw GAS Tecnologia (a popular application for Brazil access protection to online banking).
Read also: Trojan Predator The Thief attacks easy money lovers and cryptocurrency hunters
As mentioned above, in Brazil, the malware was spreading as a malicious extension of Securty System 1.0 for Google Chrome, that is, it was found in the official Chrome Web Store directory. The malicious action scheme for this extension can be seen below.
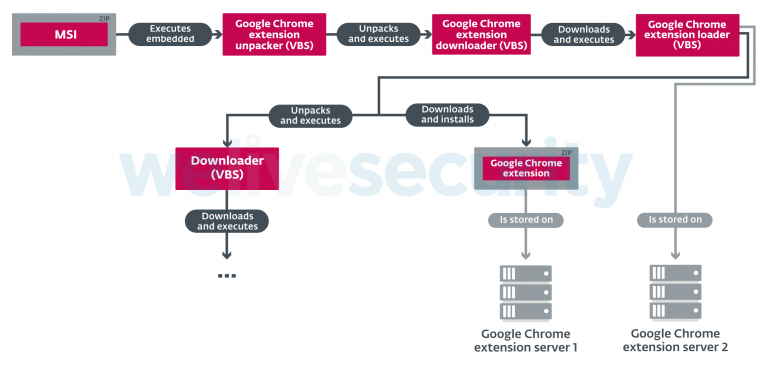
Since Tiny.cc short URLs were used during Mispadu Brazilian campaign, experts were able to collect statistics. The campaign attracted nearly 100,000 clicks from Brazil alone. Clicks coming from Android devices are most likely the result of an error, as Facebook ads were shown to users regardless of the device used.
It can be also noticed that the malicious campaign had clear phases: one phase ended in the second half of September 2019, and the campaign re-activated in early October 2019.





One Comment