
If you’re into crypto then the following information is definitely for you. Cyber security researchers warn of new strains of cryptor which specifically targets cryptocurrency communities at Discord. They say under the radar of this malware such communities as DeFi, NFT and the Crypto were recently seen to be targets. For those who are little far from all this cryptocurrency thing NFTs mean non-fungible tokens. This term stands for unique tokens that give the ownership right for data stored on the blockchain technology. Few years ago the whole industry rose significantly with an estimated worth of more than $2.5 trillion.
People on Discord started to receive fake messages
Inside the industry people use Discord, a group`s chatting platform, where you can join any chat and send privately one another messages. Crypto that this campaign deploys specialists named Babadeda (a Russian language placeholder used by the crypter). It can easily bypass signature-based antivirus solutions. In recent campaigns attackers used Babadeda to deliver RATs, information stealers and even LockBit ransomware.
In the campaign threat actor created a Discord bot account on the official company discord channel. They sent unsuspicious users a private message inviting them to download a related application that would give the user access to new features and/or additional benefits. Many people believed such messages to be legitimate because it looked like they were sent by the company. That message contained a URL which would direct the user to a fake site. Everything was so orchestrated that a user would download a malicious installer. What will you see inside of it – spyware, ransomware or a backdoor – only crooks know.
Threat actor took extra measures to make everything look legit
The actor took extra measures to make everything look legitimate. And among those are :
Once the user downloaded the malicious installer it begins execution and copies compressed files into a newly done folder named quite legitimate IIS Application Health Monitor in one of the following directory paths:
C:\Users\\AppData\Local\
C:\Users\\AppData\Roaming\
A little technical details of the cryptor
The installer copies malicious files along with other free or open-source application-related files. After the cryptor did dropping of the files execution starts via the main executable. At this stage the fake Application Error message will pop up to make a user think that the program failed while it is still secretly running in the background. Upon the close inspections of the function`s code cyber security specialists discovered that it is much longer than the actual DLL loading code. This was specifically done to obfuscate its real intentions and make it harder for detection. In the next stage execution takes place inside an additional file, usually it is a PDF or an XML file. But cybersecurity specialists note that they also saw usage of such files as PNG, Text or JavaScript. Then follows a complex set of actions that is too long to put in one post.
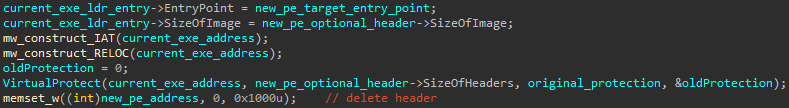
In conclusion we will be short. The final stage finds itself in the fixing of the import address table and relocation table of the newly injected PE. And the malware jumps to the entry point of the newly injected PE with the original command-line arguments.
