
Security specialists talk about a significant rise in zero-day exploitations. This year 66 cases were already detected and they outnumber any previous year before. It’s worth noting that these cases are double the amount in the 2020 year. They also add that the reasons for this can lie in ever more simplified ways of communication and a more open market on a large global scale.
Zero days: What is it?
For those who are unfamiliar with the term, zero-day mean security breach which remains unknown for the program’s producer until someone discovers it. These breaches can be discovered by the specialists and they inform the company, or hackers closely observe any companies activity and sell the information on such faults to other hackers or use it by themselves.
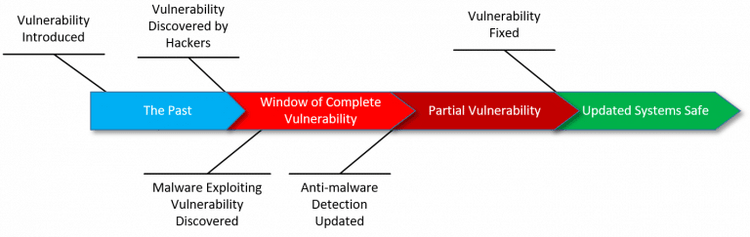
Why such incidents are the hackers’ target? This happens because two main motivations for hackers are just there. First of all, it’s the financial aspect that has its cause. If hackers, especially the ones in the ransomware field know the weakness of any company servers they can easily target it and demand money for the decryption key. The next is a political thing and some may suppose that it can be a handy thing in the political field when you want to oppose your rivals.
Advanced Persistent Threat Groups and zero-day vulnerabilities
Generally APT or Advanced Persistent Threat Groups perform in this field. These groups often do their job for years and can even retarget the victim. It is supposed they are hackers who mainly are employees of some nation states. The cybersecurity specialists name several countries where such groups are based. China, Iran, Israel, North Korea, Russia, United States, Uzbekistan, Vietnam are among them. However, the most powerful ones act from China and the United States. A well-known example of one of these groups` work is the attack on the American MSP provider Kaseya. In July 2021, the company experienced an attack by ransomware group, which had a loud resonance in the media space. Fortunately, less than 0.1% of the company’s customers were affected1.
Even though the popularity of this kind of crime is on the rise that doesn’t mean it is now easier to do specifically in terms of carrying out the task. The more advanced cybersecurity systems and the general rise in expenses make it harder to carry such operations. The price on the most valuable projects is reported to have risen up to 1150% for the past three years. Today hackers have to put much more effort in their work than ten years before.
- Updated Kaseya ransomware attack FAQ: What we know now.
