In their blog Microsoft reports about malware attacks that have recently defaced several Ukrainian government and other organizations’ sites. The team first detected the malware on January 13th 2022.
They already notified all relevant government agencies in the United States and elsewhere, as well as the victims of the attack. The team shared all available so far information with other cybersecurity providers on the threat. At the time of publishing the post and based on Microsoft visibility, the team have detected the malware on dozens of impacted systems, all based in Ukraine.
Ukrainian organizations got malware on their systems
Although specialists from the company don’t yet know for sure what cybercriminal group could be behind it. They continue to observe the situation.
The malware affected some critical executive branch government agencies, emergency response agencies and other organizations located in Ukraine. Among targeted victims is an IT firm that provides management for public and private sites. This IT firm provides management for public and private sites as well as government agencies. The team worries that the number of the victims might grow.
”Given the scale of the observed intrusions, MSTIC is not able to assess intent of the identified destructive actions but does believe these actions represent an elevated risk to any government agency, non-profit or enterprise located or with systems in Ukraine ”, goes in the second Microsoft blog post.
They explain that the malware could have infected more organizations. But specialists add that so far they don’t observe any indication of Microsoft vulnerability exploitation in the company’s products and services.
The team continues to work closely with the cybersecurity community to identify and help to recover the malware victims. Microsoft themselves enabled protection from this malware in it’s Microsoft 365 Defender Endpoint Detection (EDR) and Anti-virus (AV). The safety mechanism will work whenever these products are present and both in the cloud and premises. The investigation still takes place.
Technical details on the malware
In addition the team provided the technical stuff about the situation. The security community can use it to detect and employ necessary defense against the malware.
The malware disguises itself as ransomware but when activated makes a computer completely unworkable. More specifically, the pretended ransomware lacks a ransomware recovery mechanism. Tracked as DEV-0586 the malware rather makes the targeted device inoperable via destructive work. MSTIC (Microsoft Threat Intelligence Center) uses DEV-#### designations for temporarily unknown in origin threats. Once the source of the threat is found it receives another appropriate name.
So far Microsoft has implemented protection measures to detect it as WhisperGate(e.g.,DoS:Win32/WhisperGate.A!dha) malware family for Microsoft Defender for Endpoint and Microsoft Defender Antivirus.
It works both on cloud environments and on-premises.Though the analysis work for this malware is ongoing Microsoft shared some already known details in it’s second blog post. First they go into details on why the team thinks the malware is not a ransomware kind of threat. According to the specialists the malware shows several inconsistencies to be ransomware
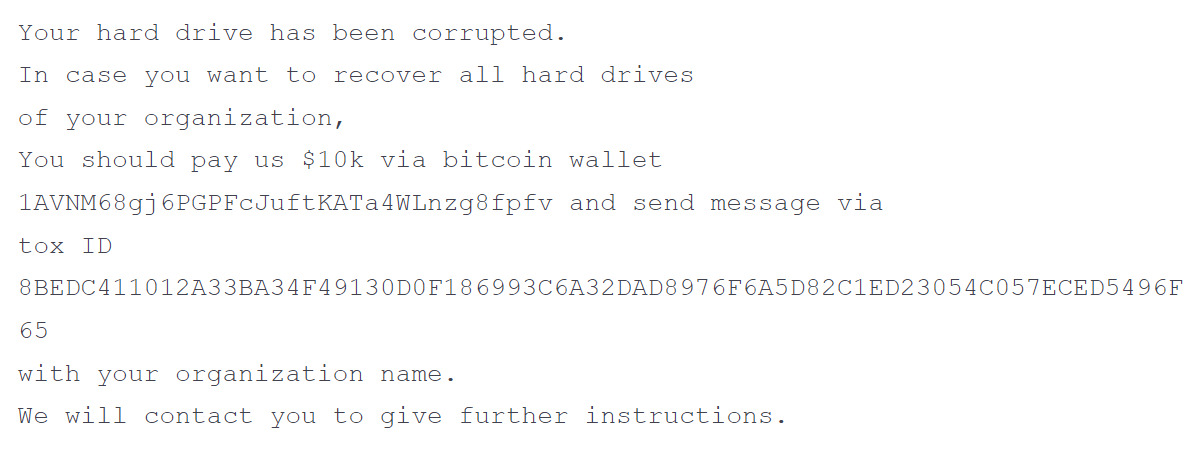
Commonly, criminal ransom notes have a custom ID. Threat actors then instruct a victim to send it to them in the process of communication.
Custom ID maps provide a route to a victim-specific decryption key. In this case the note doesn’t have it. Usually cybercriminals create websites with support forums or even add an email address, everything to make it easier for the victims to contact them. But here threat actors only give a Tox ID, an identifier that is used with the Tox encrypted messaging protocol. Nowadays threat actors mostly don’t write in their ransomware notes the amounts of money they want or cryptocurrency wallet addresses.
Here the same wallet address was observed in all malware intrusions. Specialists detected it’s only activity on January 14 with a small amount transfered.
When ransomware works it leaves the possibility for the recovery of the file system. This malware completely overwrites MBR( Master Boot Records) with no recovery option.Threat actors do the same payload. Typically for the ransomware the payloads get customized.
How the situation evolves?
The malware originates from Ukraine and specialists say it looks like Master Boot Records (MBR) Wiper activity. Shortly, the work of the malware consists of two stages. In the first one it overwrites Master Boot Record to display a fake ransom note.
In the next it corrupts to the unrecoverable state the victims files. Threat actors execute the malware via Impacket (publicly available tool that cybercriminal often use for work with network protocols. Two stage malware sit in different working directories, among them: C:\temp, C:\ProgramData, C:\ and C:\PerfLogs. Often the malware has the name stage1.exe. At this part of its malicious work the malware overwrites the Master Boot Record (MBR) on victims` systems and displays a ransom note. The Master Boot Record (MBR) is the part of any hard disk that helps boot an operating system into the computer’s main storage or random access memory.
The malware activates when the infected device is powered down. Upon execution of the next stage,stage2.exe downloads another part of the malware saved on a Discord channel. Threat actors hardcoded the download link in the downloader. The corruptor overwrites the contents of the files with a fixed number of 0xCC bytes. The total file size is then 1MB. Having done so, the malware renames each file with a visibly random four-byte extension.
For now the team is still working on the analysis of the malware and will come up with the updates concerning the whole situation later.
It is unclear for now what`s the current stage of this attacker’s operational cycle and how many victims threat actors targeted in Ukraine or other geographic locations. As a proactive defense measure the team also gave recommendations on how to adopt the proper security considerations. Microsoft is aware of the current geopolitical events in Ukraine and encourages all interested to take into consideration the known so far facts.




