
Microsoft released a fix for the Exchange bug that disturbed email delivery on on-premise Microsoft Exchange servers. Exactly at the New Year Exchange admins worldwide found out that the servers couldn`t deliver emails somehow. Instead they were pushed in line and Windows event log showed errors. For the time being Microsoft released a temporary fix. It will require users to do customer action. For now the company works on an update that will automatically fix the issue.
“We have addressed the issue causing messages to be stuck in transport queues of on-premises Exchange Server 2016 and Exchange Server 2019. The problem relates to a date check failure with the change of the new year and it is not a failure of the AV engine itself. This is not an issue with malware scanning or the malware engine, and it is not a security-related issue”, the company explained the situation in their blog.
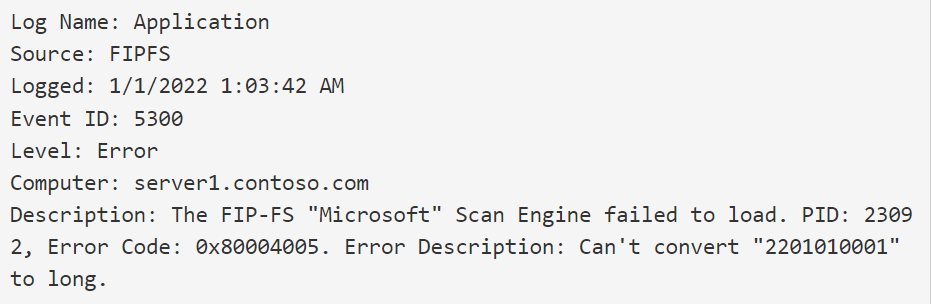
The malware engine crashed pushing emails to stuck in transport lines
The problem occured when Microsoft Exchange checked the version of the FIP-FS antivirus scanning engine and attempted to store the date in a signed int32 variable. But the mentioned variable could be stored only at a maximum value of 2,147,483,647. And it is less than the new date value of 2,201,010,001 for January 1st, 2022, midnight. Because of this the malware engine crashed pushing emails to stuck in transport lines.
As a temporary fix Microsoft released a PowerShell script named ‘Reset-ScanEngineVersion.ps1.’ Upon execution it will stop the Microsoft Filtering Management and Microsoft Exchange Transport services, remove older AV engine files and download the new AV engine. In order to use the automated script user should follow the next steps on each on-premise Microsoft Exchange server in their organization:
The execution of the script may take some time depending on the size of the organization
It will take some time for all emails to be delivered after implementation of such steps. Time depends on the amount of pushed emails in the lines. Microsoft added that the new AV scanning engine will be version number 2112330001. It references a non-existent date and the admins won`t be concerned again. Also the scanning engine will continue to receive updates in this new sequence.
You can also perform the steps manually either way they must be done on every on-premises Exchange 2016 and Exchange 2019 server in your organization. In the case of the automated script you can execute it on different servers in parallel. Besides, the execution of the script may take some time depending on the size of the organization.
