Trojan horse malware is not an easy thing to detect and remove. To get rid of it, and avoid the appearance of this tricky malware in the future, you must know your enemy’s face. And, of course, have a trojan remover for Windows.
The legend says that during the siege of Troy, Greeks failed to capture the city in a regular way. Walls and defensive armaments were too tough for the warriors to break through. Then, their main forces decided to retreat, and leave the “gift” for Trojans – a massive horse dummy. As the Greeks’ messenger explained to the defending warriors, this horse is a gift for their faithfulness and strength. Trojans, thinking that the enemy gave up and will not be back, towed the horse inside of the city walls. And there the show started – horse dummy has an inner space, which was filled with Greek warriors. Trojans were not ready to defend themselves on the streets, and a small group of Greek fighters captured the city and managed to open the gates for the main forces. The wooden dummy was depicted in the legend as a Trojan Horse.

What is trojan horse malware?
As you can see from the note above, the name for this malware type appeared because of the similarity with a legendary horse dummy. And it really has a lot of things in common with such a gift. Trojan viruses are injected under the guise of a legit thing – one which must not cause suspicion. At least, the mottos which you can see on the sources of this nasty stuff will ensure you that this program is 100% OK, and you have nothing to worry about. Nonetheless, you do.
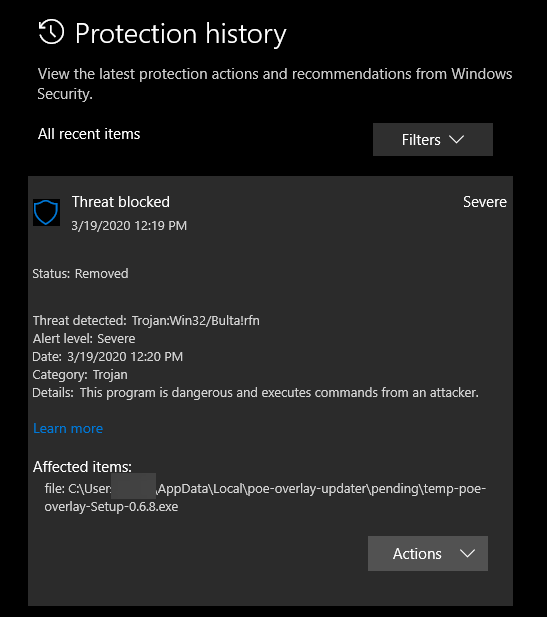
Cybercriminals choose different shapes of shells for their malware. Greeks were restricted by limited materials they had, hackers have likely no limits. The obvious “carrier” for the trojan horse malware is something not very legit, a thing that requires disabling the antivirus for correct work. Such programs are cheat engines, keygens, Windows activation tools and other hacking things. The fact that anti-malware tools detect it will likely be ignored – because they detect even a “clear” version of these tools. In the case of ones that are infected, there is a chance to get only a trojan, without a really functional tool.
Rarely, trojan horse malware functionality is added to a legal program. That usually happens when a third party edited the code of this program – to disable the license, for example. Usually, authors of such hacks are not paid in any way, so they try to monetize their job with such sly methods. Freeware is also an often carrier for trojans – their developers do not receive any payments, too.
Types of trojan virus
Crooks are free to spread any type of malware when it is disguised as something legitimate. Hence, you can get any of the possible malware types. Spyware, backdoors, coin miners, adware and ransomware are one of the most popular types of ones. Worms and viruses almost ceased to exist in the early ‘10s, so they are almost impossible to meet nowadays. However, these names are sometimes used as an umbrella term for malicious software.
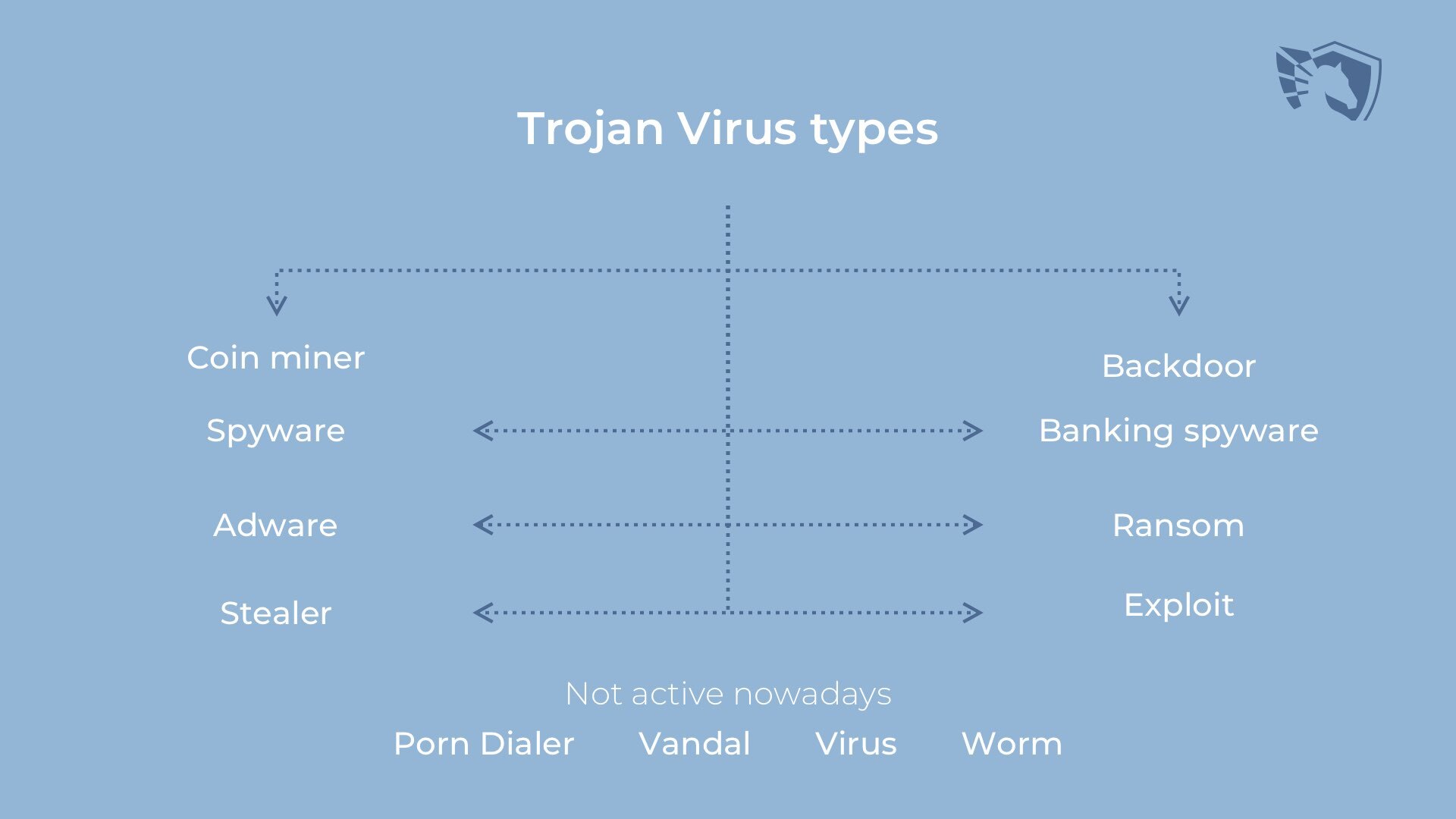
Some of the trojan virus types that were widespread over a decade ago do not exist now. Besides the aforementioned virus and worm trojans, there are so-called porn dialers, vandal trojans and locker trojans. First ones disappeared after the dial-up connection was squeezed out of the market by a broadband internet connection. This thing was changing the provider number at the dial window on a random number, which belongs to a country far away from yours. The bills for such a “connection” were often higher than $2000. Vandal trojans were destroying the partition tables on your disks – so you were not able even to start your system. Lockers were predecessors of ransomware – they were locking your desktop, showing a scary banner that stated something like “FBI locked your PC for watching porn” and asking for ransom payment (~$100-300).
How to avoid trojan virus injection?
Just take a look at the distribution ways of these malicious programs. The answer to this question is exactly on the surface. Do not use any dubious tools – keygens, cheats or hacktools. At least, try to find relevant feedback on them – in order to be sure you are not shooting your knee. The same thing with freeware – even if these programs are published directly by their developers, their benevolence must be proven.
A separate category of programs that must be checked with an increased suspicion is abandonware. These programs are no longer supported by their developers – because of their bankruptcy or the loss of any reason to support the old program. Hence, the spreading of these things is backed by third parties. If it is a popular old game, like Heroes of Might and Magic 3, they can even release updates for it. But they also can inject malware into their “products”.
Typical places where you can find these nasty pieces of software are online forums, sites with hacked software and torrent trackers. There, in the territory where no one pays attention to what happens, it is very easy to meet something that will smack up your computer. Sure, you can find a well-working self-made program there, but the risks are always with you. Never forget this – and always hold your hand on the countermeasures. Exactly, the tool which will act as a trojan remover for your Windows – but which one?
How to remove the trojan horse malware?
Removing the application which acts as a carrier for trojan virus is not enough. Sure, you will remove the executable code of malware, but all changes it did to your system are still present. And reverting them all is likely impossible – malware makes tons of changes in different parts of your system. Searching for each one in Group Policies, Windows Registry and networking configurations may be a huge source of headache for you. It is better to use a program that is designed for this task.
Trojan Killer, as you can already understand by its name, is specially designed to defeat different malware types. Nonetheless, it is also capable of removing all other malware. It consumes very little RAM amount, takes only 300 MB of disk space after the installation, and has nothing excessive – only needed functions. This perfect trojan remover tool will work perfectly on Windows 7, Windows 8/8.1, Windows 10 and even Windows 11.

Remove trojan viruses with GridinSoft Trojan Killer
Download and install Trojan Killer using the button above. After the installation, you will be offered to start a free trial – the 6-day period when you can use all benefits of a full license for Trojan Killer. Type your email, receive the code and keep going.
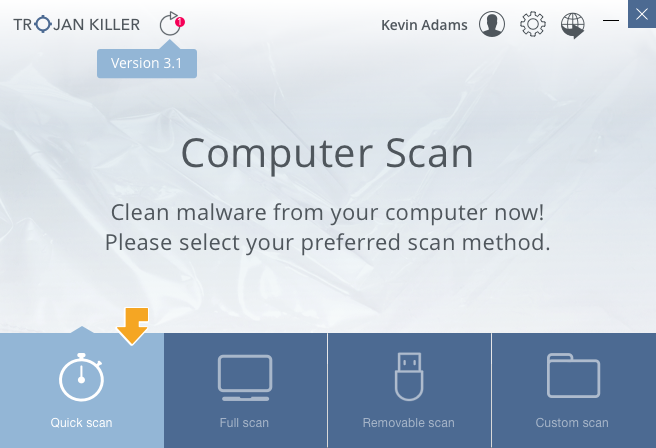
After starting the free trial, launch the Full Scan. It will last about 10-15 minutes. You can use your computer as usual.
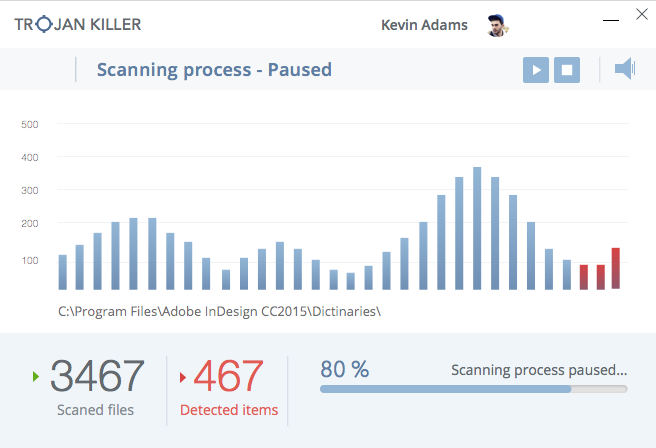
When the scan is finished, you will see the number of detections, and the “Cure PC!” button.
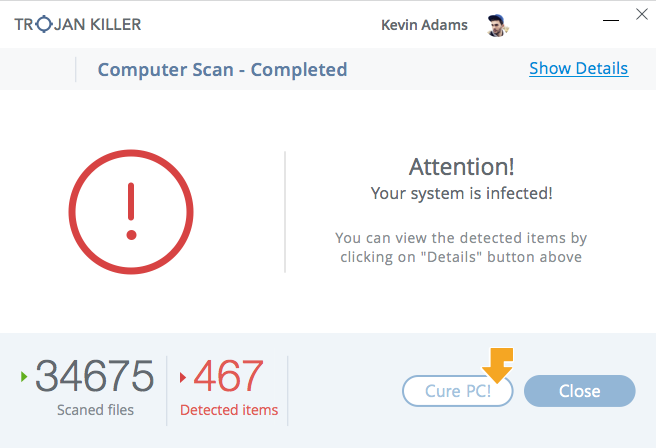
In less than 10-15 second, your system will be cleared out. Reboot your computer and use it like there was no trojan horse malware.