RIG exploit pack began distributing a previously unknown version of Vega ransomware.
Buran encoder encrypts user files and invites victim to contact cybercriminals via email for data recovery. The security analysts have not yet been able to create a decoder for the new malware and recommend victims copy ransom documents, as well as registry entries created by the malware.A new payload of the RIG malware kit was discovered by the research team nao_sec, which specializes in tracking exploit packs. As Internet security specialists have found out, RIG exploits vulnerabilities in Internet Explorer browser to deliver cryptographer to target devices. Once on the machine, Buran copies itself to the folder with %APPDATA%\microsoft\windows\ctfmon.exe, and then proceeds to encode victim’s information.
According to analysts, the new malware does not delete shadow copies of the volumes, does not disable Windows automatic recovery mechanism, and does not clean the event logs.
Ransomware encodes all files on the disk, with the exception of the objects included in its stop list. Encryption does not affect files with the extensions COM, EXE, DLL, SYS, as well as some other formats. In addition, ransomware misses about forty folders, content of which may interfere with operation of the device.
For the infected computer, a unique computer identifier is created, which Buran also uses as the extension of the modified files. Message to the victim is contained in a text document with the name !!! your files are encrypted !!!. txt. Attackers offer victim to contact them by e-mail to get the KEY, and warn against attempting to recover the data on his own.
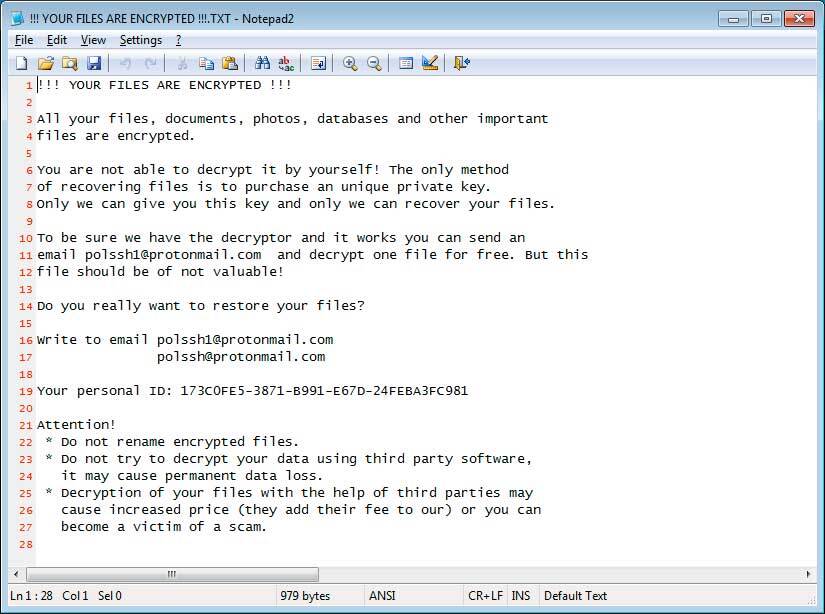
Researchers note that malware creates in the registry HKEY_CURRENT_USER\Software\Buran entries that are similar to the public and private encryption key, but it is not known whether it is possible to recover coded information using them.
RIG is currently one of the most active exploit packs. He replaced the Angler, Nuclear and Neutrino sets in 2016. RIG operators often contract to distribute ransomware and at various times delivered Matrix, Locky, CryptoShield and GandCrab to it with the help of encryption software.
Despite the general decline in the share of ready-made kits, RIG regularly appears in the field of view of information security specialists. So, last summer, he was spotted in the CEIDPageLock rootkit campaign.
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them.
- Scan attachments with tools like VirusTotal.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed.
- Use hard passwords and never reuse the same password at multiple sites.
- If you are using Remote Desktop Services, do not connect it directly to the Internet. Instead make it accessibly only via a VPN.
Source: https://www.bleepingcomputer.com




