A recently fixed vulnerability in Oracle WebLogic is actively exploited by cybercriminals for installation on vulnerable servers of cryptocurrency miners.
This is a deserialization vulnerability (CVE-2019-2725) that allows an unauthorized attacker to remotely execute commands.Problem was discovered in April this year, when cybercriminals had already shown interest in it. Oracle fixed vulnerability at the end of the same month, however, according to Trend Micro, it is currently actively used in attacks.
“Reports emerged on the SANS ISC InfoSec forums that the vulnerability was already being actively exploited to install cryptocurrency miners. We managed to confirm these reports after feedback from the Trend Micro™ Smart Protection Network™ security architecture revealed a similar cryptocurrency-mining activity involving the vulnerability”, — report Trend Micro specialists.
According to the researchers, with the help of the vulnerability, attackers install cryptocurrency mining machines on compromised computers. To bypass detection, they hide malicious code in digital certificate files.
Once executed in the system, malware exploits the vulnerability to execute commands and a number of tasks. First, using PowerShell, certificate file is loaded from C&C server, and CertUtil, a legitimate tool, is used to decrypt it. Then, using PowerShell, this file is executed on the target system and deleted using cmd.
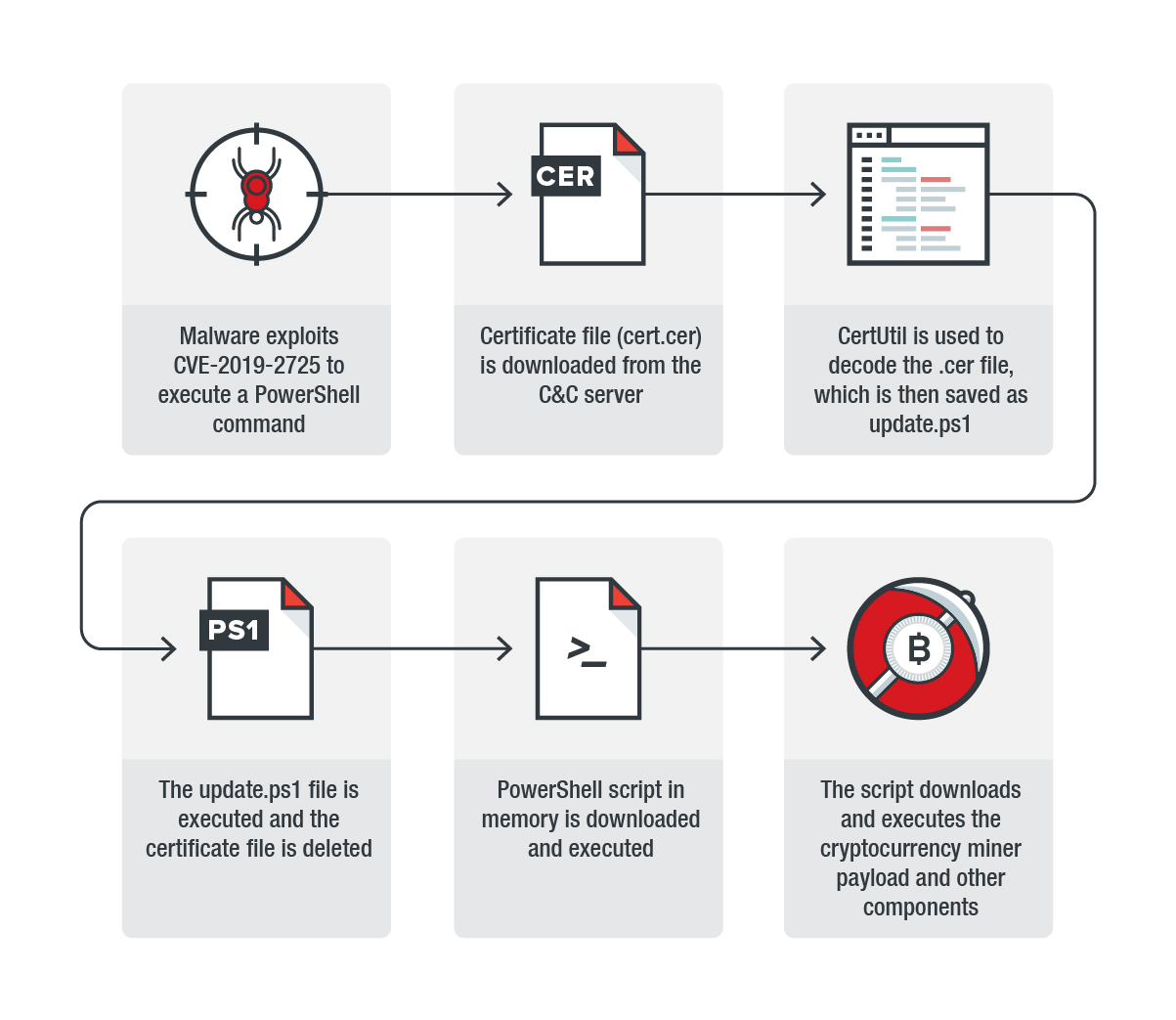
The certificate looks like a regular certificate in the Privacy-Enhanced Mail (PEM) format, but it takes form of a PowerShell command instead of the usual X.509 TLS format. Before receiving a command, the file must be decrypted twice, which is quite unusual, because the exploit team uses CertUtil only once.
The idea of using certificate files to obfuscate malicious code is not a new one. However, real attacks using this method were not previously detected, and if they occured, they are very rare.
It is worth reminding that, Oracle has already released an update that addresses CVE-2019-2725. Thus, it is highly recommended for organizations that use WebLogic Server to update their software to the latest version to prevent any attacks that exploit the vulnerability from affecting their businesses.
Source: https://blog.trendmicro.com
