It’s no wonder that in recent years the ransomware industry saw a significant rise. People became reckless at cybersecurity, ignoring its basic principles. Crooks took this fate’s gift and used it to fill their wallets. And among the most notable players in this criminal game, the Russian-based hacker group REvil got the most attention at this moment.
Who got this time on REvil`s way?
The American media outlet The Washington Post reported that REvil is online again. In a relatively short period, it has already carried out 8 ransomware attacks. Among the victims are plastic manufacturers and a legal aid service for the poor. It’s the first activity since the hacker group went offline last summer. Their activity is the thing that American president Joe Biden repeatedly made an accent on to the Russian president Vladimir Putin during their conversations.
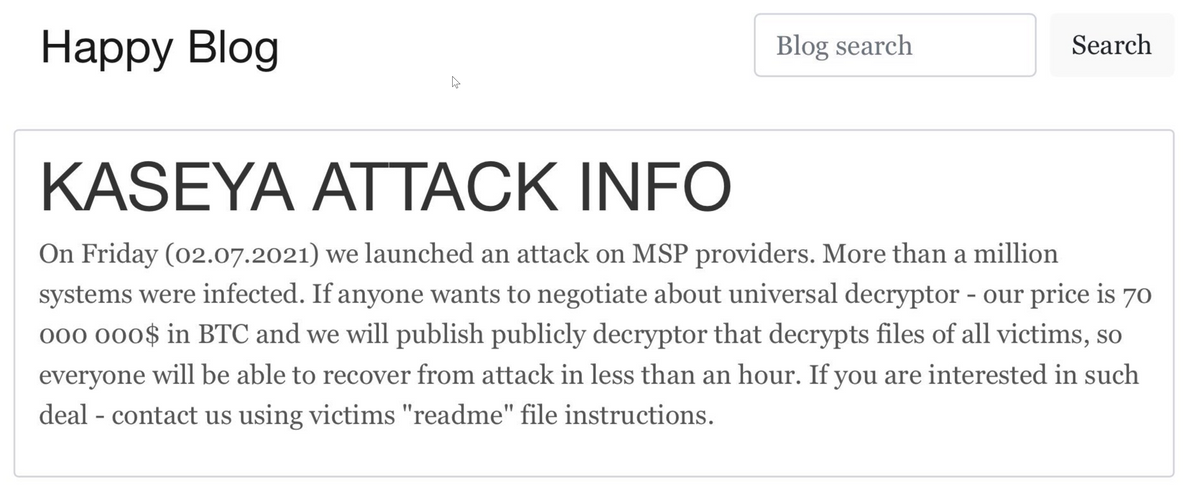
Before going on a short hiatus this summer, REvil carried out the string of several successful and unsuccessful attacks. In those cases that are public, Kaseya, the IT company, was infected on July 21. Maryland IT company JustTech with 120 employees was also the target. The biggest case of all was stopping the operation of the world’s largest meat company JBS. The company’s operations in Canada, Australia and the United States were temporarily shut down.
REvil ransomware choices
Schools in New Zealand, Coop grocery stores in Sweden, and small towns in Maryland were affected by the hacker group activity. Also, a hospital in Romania turned out to be a target but the administration had paper backups of all patients` files. So they got through it easily, despite the fact that the attack was successful. Possibly, having a paper copy of all your electronic documents is a way to forget about ransomware. Of course, until someone spills a cup of tea on it. But besides joking, information safety requires much safer storage methods than ones we have nowadays.
As Coop spokeswoman Helena Esscher says, they had to close about 700 of our stores, and it took six days before all of them opened again. The financial impact they got after the attack depends on several factors, such as loss of sales, of course, but also insurances and to what extent they cover events like that which occurred.”
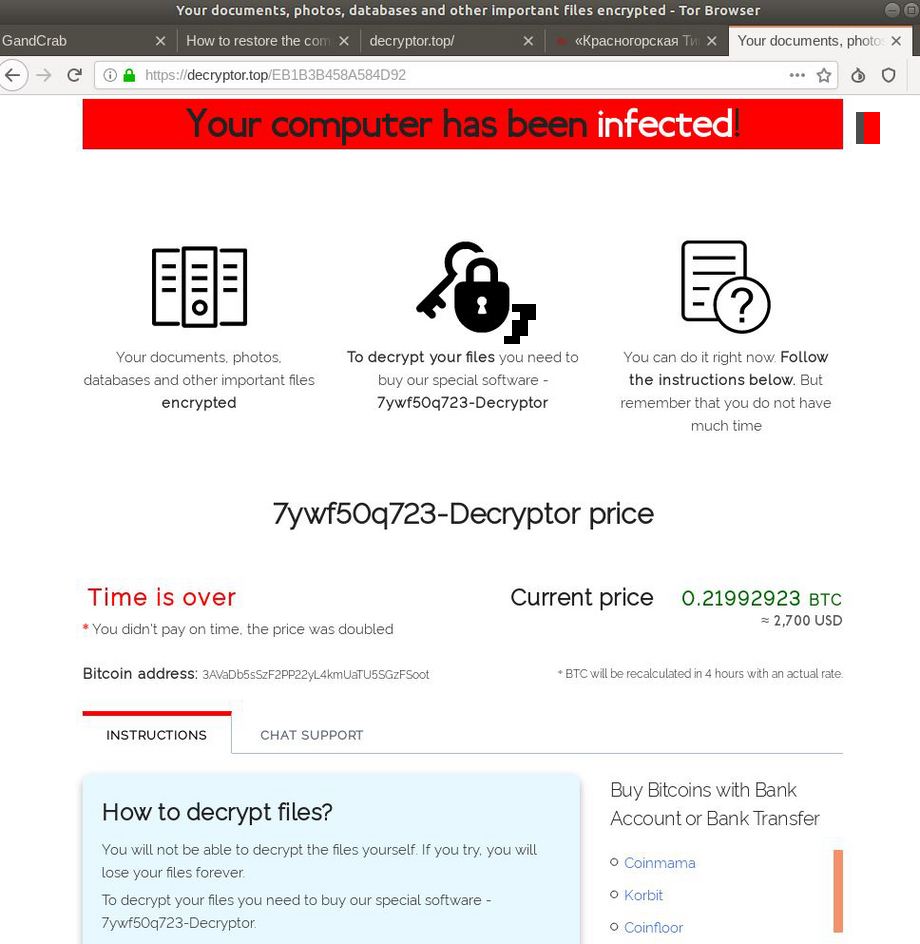
REvil`s ransoms ranged from $45,000 to $5 million per infected device with Kaseya company being charged $70 million. If this sum is paid, it will be a new record of the paid ransom size that has ever been asked. Currently, the biggest ones are paid by Acer and Accenture – both were forced to pay $50 million. The ransomware turned out to be an extremely serious problem. It is even listed in the current American president`s plans of action as one of the top problems to deal with1.
What’s the matter of all discussions?
The Federal Bureau of Investigations was also put into the spotlight. The Washington Post wrote that the law enforcement obtained a key decryptor but waited for almost three weeks not to scare the hackers off. The story of the Coventry bombing repeats itself once again?. The plan was to carry the takedown just when REvil`s platform went offline. Many argue that the bureau shouldn’t have waited so much time with the decryption key. Many businesses could have recovered with less money expenses, had the bureau shared the key earlier.
“We make the decisions as a group, not unilaterally”. “These are complex…decisions, designed to create maximum impact, and that takes time in going against adversaries where we have to marshal resources not just around the country but all over the world,” — FBI Director Christopher A. Wray.




