This year almost at the end of October a new ransomware group appeared with quite an unordinary encryption technique. “Memento Team” instead of encrypting files itself copies them into password-protected archives by using a retitled freeware version of the legitimate file utility WinRAR. Then the gang locks the archive with passwords and deletes original files. In the ransomware note criminals instruct victims to contact them via a Telegram account. The team of cybersecurity analysts provided a description of some of their client’s experience with the new ransomware.
WinRaR became the new ransomware tool
“The modifications to the ransomware changed its behavior to avoid detection of encryption activity. Instead of encrypting files, the “crypt” code now puts the files in unencrypted form into WinRaR archive files, using the copy of WinRAR, saving each file in its own archive with a .vaultz file extension. Passwords were generated for each file as it was archived. Then the passwords themselves were encrypted,” – SophosNews report.
The wording and formatting of the group`s ransomware note looks similar to that of the REvil ransomware gang. In addition, it threatens to leak the data if payments are not made. But unlike REvil payments were asked to be made in Bitcoin. The gang demanded 15.95 BTC (roughly $1 million US). That’s the sum for all files and they also offered varying price rates for different types of files, separately. The exact usage of WinRar archives with passwords is very similar to old jokes from ’00s. Then it was just pranks, but now these are real cyberattacks.
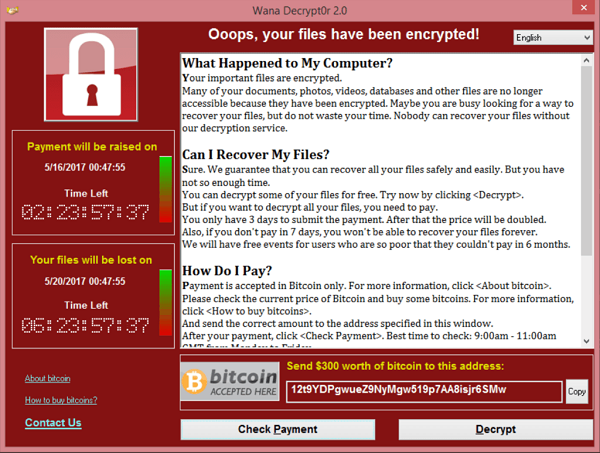
After almost six months secretly probing the victims’ network gang began their attack. Unluckily for them, the victim didn`t start the negotiation process. Targeted organizations previously made the backups of the encrypted files and could get back to rather normal work despite the attack. In general, 2021 year saw a significant rise in ransomware attacks and demanded payments. Below we provide you with a short excerpt of the most common trends for this year in this particular criminal ecosystem.
Ransomware 2021 year facts
These are just short sentences but they should give you the main points in the field. Ransomware started to spread itself to mobile phones thanks to mobile`s general more openness to malware. The majority of them cover the browser or an app with the ransom note making the device unusable. Due to the pandemic, most ransomware gangs projected their interests to vulnerable industries such as municipal facilities, schools and remote work employees. RaaS or Ransomware-as-a-service developed into quite an effective work business. It allows ransomware gangs to use already developed ransomware tools. The decentralized nature of the whole economy makes it difficult for the law enforcement agencies to successfully target them.
Ransomware evolves in its tactics and methods of work with several new quite effectively ransomware strains having made headlines. About some of them you surely have heard about. Conti, REvil, DarkSide and Netwalker change their behavior so the new detection methods need to be applied to continue the fight with them at the same level. And that makes some percent of success for the upgraded strains of ransomware as there could not be at that very moment help tools.




