Microsoft announces it introduces new changes to it’s automation capabilities called active content in Office (The most common kinds are macros). If earlier users could enable them by clicking the corresponding button now they will see the Learn more button where they could learn the possible danger the received files might present and what possible solutions might be done to avoid it. While the user proceeds to the Learn more button the internet files with the macros in it will be blocked by default.
Bad actors actively exploit macros for criminal operations
The company says such steps should reduce the instances of cybersecurity breaches in companies and in home user machines as well. They explain that threat actors for the past years have been actively exploiting this useful feature in their criminal operations. By simply sending an email attachment or via some other way an internet file threat actors could successfully implement steps of the attack.
Now to open the file received from the internet user have to go to the Learn more button where they could learn how to properly open the file without putting themselves in danger. The change will affect five Office apps that run macros: Word, Visio, PowerPoint, Excel and Access. The said alteration will begin rolling out in Version 2203 with Current Channel (Preview) in early April 2022. After this it will be introduced to other update channels like Semi-Annual Enterprise Channel, Monthly Enterprise Channel and Current Channel.
Company also plans to introduce the same change to Office 2013, Office 2016, Office 2019,Office 2021 and Office LTSC. The date is yet to be determined.
“A wide range of threat actors continue to target our customers by sending documents and luring them into enabling malicious macro code. Usually, the malicious code is part of a document that originates from the internet (email attachment, link, internet download, etc.). Once enabled, the malicious code gains access to the identity, documents, and network of the person who enabled it.”
Tom Gallagher, Partner Group Engineering Manager, Office Security
Microsoft introduces changes on macros only in Windows
Macros are a useful feature of Microsoft Office apps that allow you to automate some operations done in one of these apps. For example every month you have to make a report for your accounting manager. And everytime in this report you have to do a certain same formatting of the document. But with Office macros everything can be done much easier if you simply automate some actions with the help of macros. It’s rare that a user would use them while simply editing or reading a document in Word. But threat actors employ macros to spread malware, getting remote access and stealing sensitive information.
With a new change introduced the users instead of simply allowing the internet macros to run will be presented with an information on how to enable safely the macros by saving the file and removing the Mark of the Web (MOTW). Additionally users can read about the security risks connected with bad actors using macros and also learn the safe practices to avoid phishing and malware.
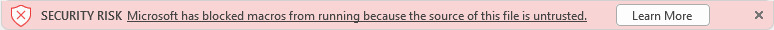
The MOTW is an attribute that Windows ads to files originated from an untrusted location (Internet or Restricted Zone).The attribute is only added to files saved on an NTFS file system, not files saved to FAT32 formatted devices.
The administrators in organizations can use “Block macros from running in Office files from the Internet” policy to prevent workers from unintentionally opening files from the internet that contain possible malicious macros. Company ads that if an administrator enables this policy, the organization won’t be affected by the default change.
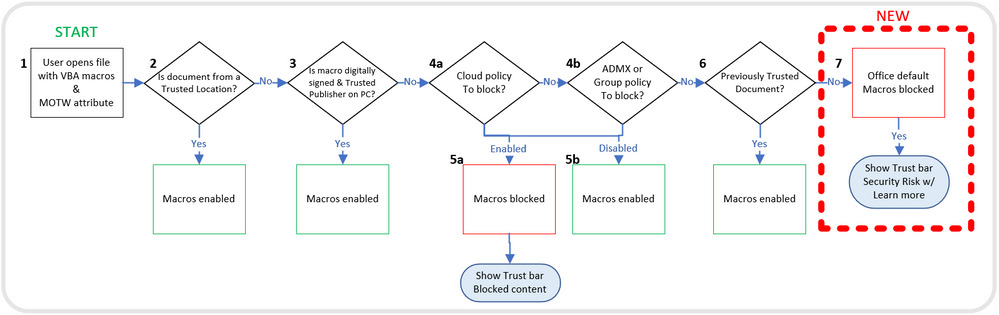
Microsoft emphasizes the importance of enabling this policy for organizations. They say for years they’ve recommended blocking macros obtained from the internet in their security baselines. To secure customers with such a policy by default is the next step of hardening cybersecurity as Hani Saliba, Partner Director of Engineering, Office Calc expressed their opinion on the introduction of change on how macros mechanism will work now.
The other ways to know your files is safe will be next:
Before enabling the policy for organizations Microsoft recommends for IT administrators to work previously with the business units that use macros in their Office files, such as the Finance department, and with independent software vendors (ISVs) that organization rely on who make use of macros in Office files.
How to avoid malicious macros?
So maybe you still wondering what you should do with that email sent a few days ago consider the following questions:
Also, the change won’t affect Office on the web, Office on Android or iOS devices and Office on a Mac. It will only touch the Windows based devices.




