Recently IKEA, a Swedish-origin Dutch-headquartered multinational conglomerate, reported the waves of an internal phishing campaign. Threat actors used internal compromised servers to send company’s employees emails with malicious attachments. Cyber security specialists say similar techniques hackers used in recent campaigns of spreading Emotet and Qakbot trojans. The whole complexity of the situation alludes that there may be possible cyber security threats to the company. Although no further details were provided.
Threat actors attacked IKEA with an internal phishing campaign
Usually in conducting attacks like this, threat actors would compromise internal Microsoft Exchange servers using ProxyLogin and ProxyShell vulnerabilities. As soon as they gain access to the server they begin to perform reply-chain attacks against employees with stolen corporate emails. Being sent as reply-chains emails from the company they certainly give off a feeling of legitimacy.
“This means that the attack can come via email from someone that you work with, from any external organisation, and as a reply to an already ongoing conversation. It is therefore difficult to detect, for which we ask you to be extra cautious,” goes in an internal email sent to IKEA employees.
As the IT specialists of IKEA say, the warning signs to look for if the email is malicious are seven digits at the end of any attachment. Company also told employees not to open any emails sent to them and straightaway report them to the IT department. As a precautionary measure as well, the company’s management in regard to their concerns restricted the ability of employees to retrieve emails that may end up in the employees` quarantine boxes.
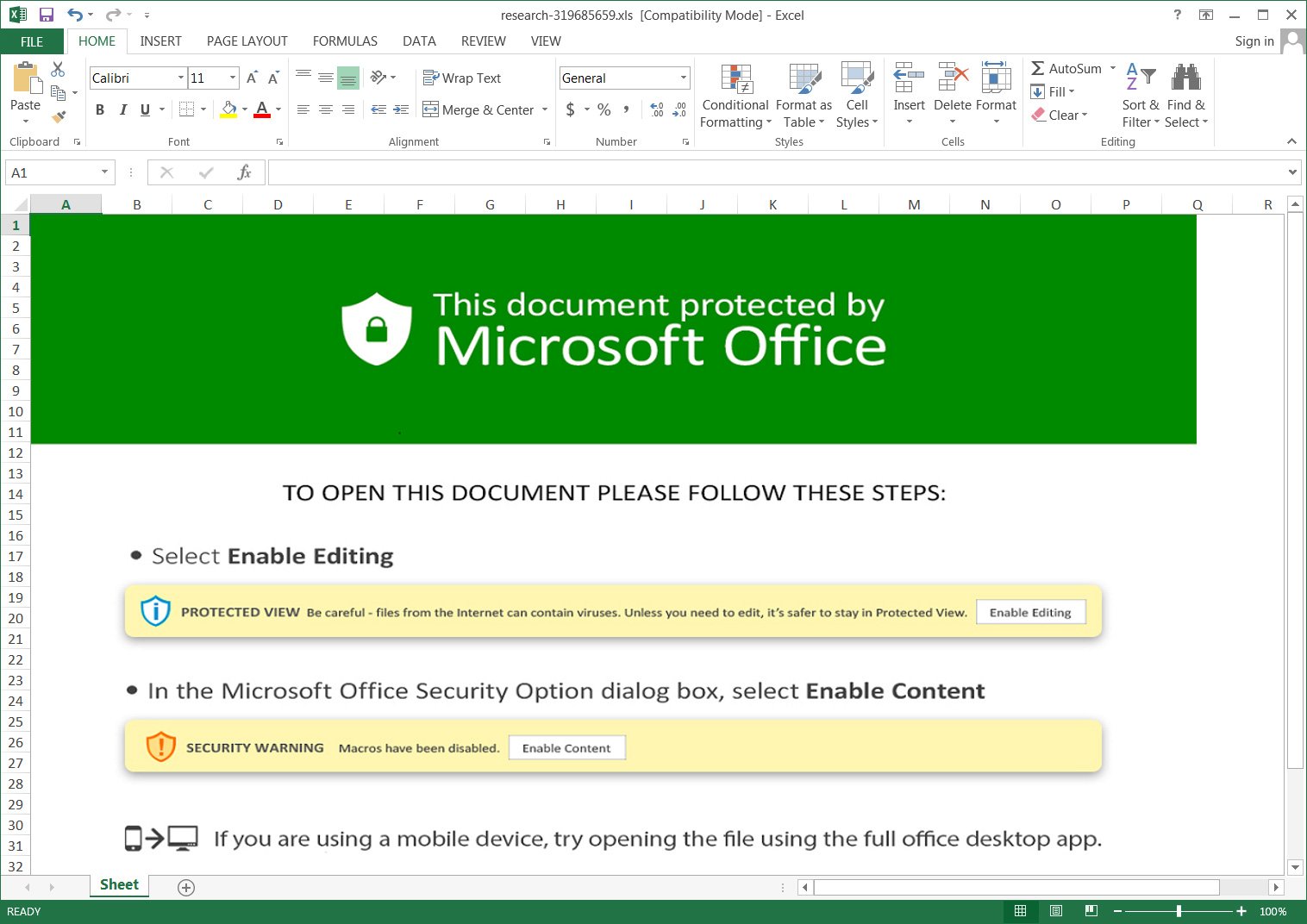
The malicious emails contained URLs that would redirect the browser to a download titled “charts.zip” which had an Excel document. Potential recipients of such emails were prompted to click the enable buttons to view the attachment. Of course such actions immediately activated the malicious macros. They in turn download files titled ‘besta.ocx,’ ‘bestb.ocx,’ and ‘bestc.ocx’ from a remote site and save them to the C:\Datop folder. Now renamed DLLs files begin the execution process with regsvr32.exe command to install the malware payload.
How to know if I received a phishing email?
You can say phishers these days are fierce and those “You won 1 million please respond to this email” phishers desperately trying to keep up with the times ( Tell me who are those people who respond to them, though). Nowadays threat actors apply more cunning ways to trick you into providing your information.
Now as I write this I think back to that woman call from allegedly some bank and still wonder if that was a phisher. But back on track: the best solution to a problem is to prevent it. Know the next proven tips for phishing email detection:




