Information security specialist Alex Lanstein discovered an original vector for the distribution of the RAT trojan. Criminals give links to the RAT trojan in WebEx invitations.
Cybercriminals deliver malware by redirecting the victim through an open redirect from the Cisco website to the infected page that hosts the fake WebEx client, an online conferencing software.“Using open redirects add legitimacy to spam URLs and increases the chances that victims will click on an URL. An open redirect is when a legitimate site allows unauthorized users to create URLs on that site to redirect visitors to other sites that they wish”, — reports Alex Lanstein.
The attack begins with a letter containing an invitation to a WebEx conference. The official site of the system is indicated as the sender, and the appearance of the message corresponds to legitimate samples. The text contains a link where the victim allegedly can join the conversation.
Cybercriminals use an open redirect mechanism that allows you to send a visitor to a third-party resource through a legitimate site.
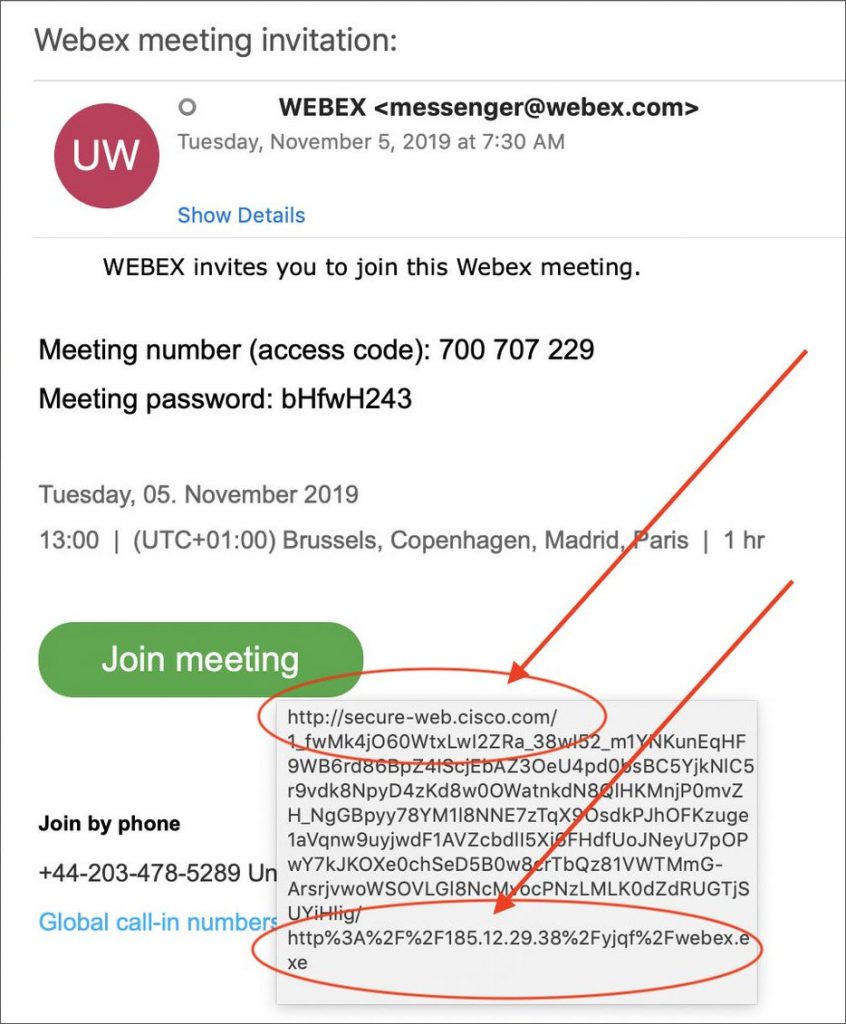
Despite the fact that the link from the fake invitation includes the official Cisco domain, in reality it opens the intruders page.
“As WebEx is owned by Cisco, the use of this URL could easily trick a user into thinking that the webex.exe is the legitimate WebEx client that is commonly pushed on users when they join a meeting”, — writes Alex Lanstein.
The victim is offered to download the webex.exe file, supposedly necessary to start the conference, however, instead of the utility, the WarZone Trojan, which is capable of:
- upload, delete and run files;
- intercept keyboard input;
- activate remote access services to the machine;
- remotely control the camcorder;
- steal saved passwords from Firefox and Chrome.
Specialists could not accurately determine whether the backdoor belongs to a particular family. Some services identify it as WarZone, others identify it as the AveMariaRAT trojan. The program is embedded in the MusNotificationUx system process, which is responsible for pop-up notifications of available Windows updates. The malware also creates a shortcut in the startup list to continue working after the computer restarts.
Read also: xHelper “undeletable” Trojan infected 45,000 Android devices
According to statistics compiled by Spamhaus specialists, in the third quarter of this year, the AveMariaRAT malware took the penultimate place in the top 20 trojans in terms of the number of command servers – it has 19 control centers. The largest number of resources is in the Lokibot botnet, the authors of which hold 898 criminal network nodes.
Recommendation:
Anyone who has encountered this spam campaign and executed the webex.exe should immediately scan their computer for infections. Victims should also assume that any login credentials for sites they visit are compromised and the passwords should be changed immediately.
This spam campaign also illustrates that following the advice of checking an email URL before clicking may not always be enough.




