AntiPegasus program, an anti-spyware tool, has a malicious twin-brother. One of the fresh investigations that were done by Cisco Talos showed a huge fraud campaign. It was circulating among the people who installed and used the aforementioned program to stop the Pegasus spyware. Instead of AntiPegasus, users were getting the Sarwent RAT.
What are Pegasus and AntiPegasus?
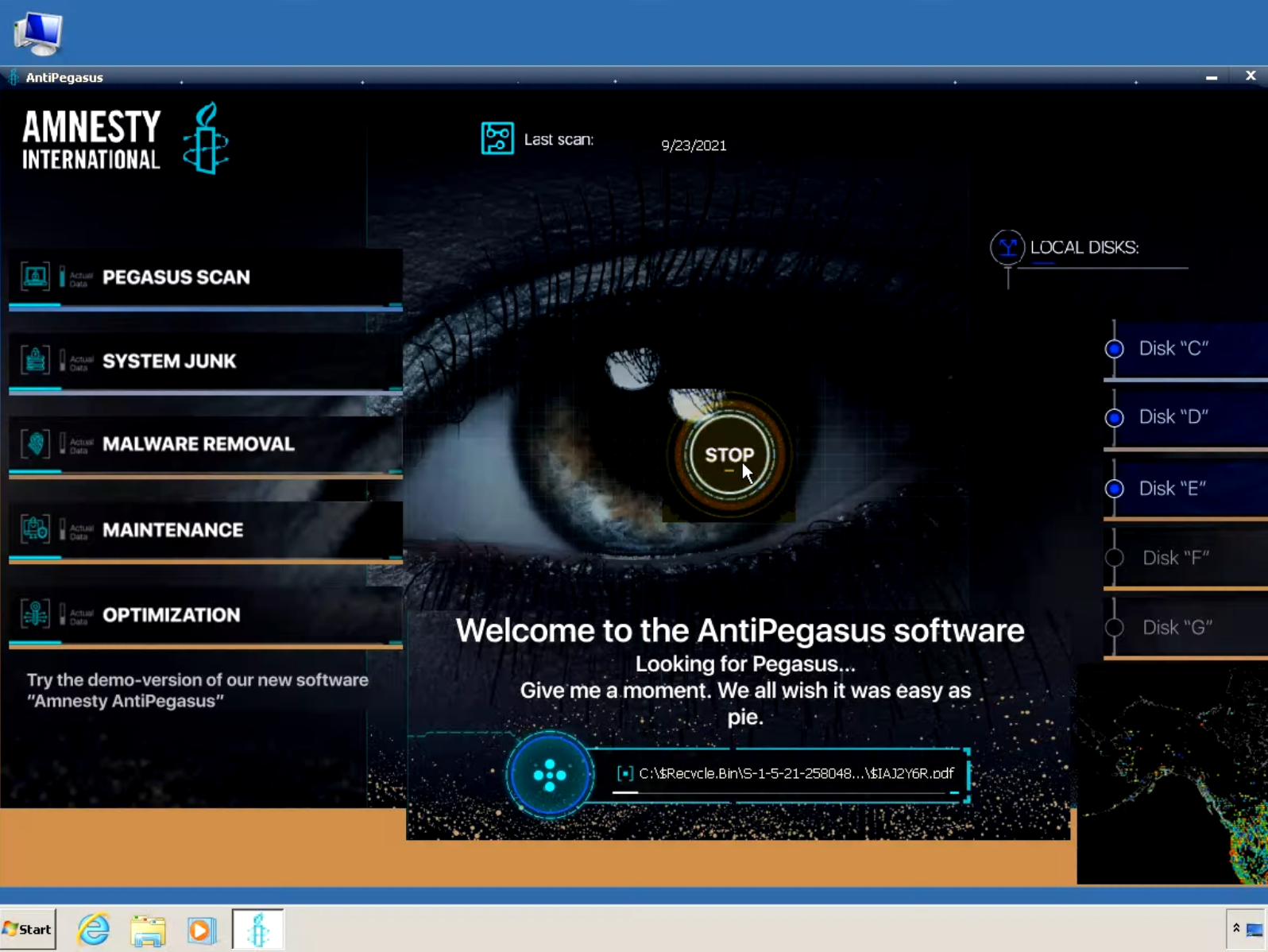
AntiPegasus is an anti-spyware program that is designed specifically to stop the Pegasus spyware. It was developed by Amnesty International, the UK-based non-commercial organization that took care of the usage of Pegasus by several governments. This software can be classified as an anti-malware program, but it still has the only task – find and remove Pegasus. It does its task pretty well and offers a free demo mode.

Pegasus itself is a project of Israeli firm NSO Group. This spyware is able to read text messages, overhear phone conversations, track the location, collect passwords, and a lot of other things that are typical for spyware. In fact, Pegasus is military-grade spyware that is able to get any type of information from the infected device. The developers from NSO (that belonged to the US-based company Francisco Partners at that point) claimed that this development provides “authorized governments with technology that helps them combat terror and crime.” Nonetheless, there were a lot of cases when some criminal structures used this software for their own purposes. Some countries also made use of it in order to spy on journalists or public figures that are objectionable to the government.
How did the AntiPegasus fraud happen?
Amnesty International is spreading the AntiPegasus tool on their official website. Fraudsters who spread the virus counterfeited the website of an anti-spyware tool. These fake sites (Cisco Talos detected 3 such pages) are pretty similar to the original Amnesty website. Worth saying that fraudsters did a great job copying the original site. It is quite hard to understand that you are looking at a counterfeit until you check the address bar. All these fake sites are registered in Kyiv, Ukraine, but the email addresses of domain owners are different and belong to various countries. It seems that such a choice of the hosting location is just a way to confuse the tracks.
Here is the list of site URLs that mimic the original site:
Remote-access trojan, or RAT, is a malware type that is designed to allow the third party to access the victim’s PC without any authorization. The way this trojan does its job is different, but it is always a bad case. It has backdoor functions on its basis, but in contrast to backdoors, it can also carry a lot of additional functionality. Even worse is the case when it is disguised not as a dubious tool, but as anti-malware software.
How does Sarwent look and work?
The Sarwent RAT even tries to mimic the legit AntiPegasus – at least, its interface repeats the original one. It also imitates the functionality of a real program – tabs with settings, scan history and other elements. Nonetheless, the remote-access trojan written on Delphi is right inside. The exact motivation, as well as actions done by that trojan, are not clear. Exactly, there are only 150 victims of such a scam in the whole world. The majority of victims are from Great Britain (142 users), four users from the USA and another 4 – from the Commonwealth of Independent States. It is strange to see the CIS countries in the list of attacked ones since usually cybercriminals from CIS avoid attacking their own countries. However, that is the other proof of the theory that hosting in Kyiv is just confusing the tracks.
The exact Sarwent has quite typical functionality as for the remote-access trojan. It establishes remote access to the infected PC via RDP or PowerShell. After establishing the connection and making all required changes, this RAT is able to steal the data, launch the apps, or act as a trojan-downloader. The command server of this trojan works in the medicalsystemworld[.]com domain.




