Researchers from X-Force, IBM department on cybersecurity – reported about malware spam-campigns, in frames of which criminals send keylogger HawkEye on employees of industrial enterprises emails worldwide.
For two months attackers spread software among employees of companies that work in logistics, healthcare, marketing and agriculture.“In the cybercrime arena, most financially motivated threat actors are focused on businesses because that is where they can make larger profits than attacks on individual users. Businesses have more data, many users on the same network and larger bank accounts that criminals prey on. X-Force is not surprised to see HawkEye operators follow the trend that’s become somewhat of a cybercrime norm”, — report X-Force specialists.
Criminals interested in confidential data and credentials that later used for stealing accounts and attacks on corporate emails.
Besides, HawkEye can upload malware programs on infected devices.
During the April and May spam-campaigns attackers spread HawkEye Reborn versions 8.0 and 9.0 in letters allegedly from banks and other legitimate organizations, but, according to researchers, attached pictures of low quality and poorly formatted text. In attachments letters contained archive with malware file, previously converted from PDF into PNG, and later in LNK. While unpacking it secretly starts keylogger, and, distracting attention, reflected fake recipe.
For infecting devices were used several executable files. Firstly, mshta.exe that involved PowerShell-script for connection to the located on the attackers’ AWS C&C-server and uploaded additional parts of a program. Secondly, was gvg.exe that contained Autolt-scenario, which ensured automatic start of a keylogger after system’s restart.
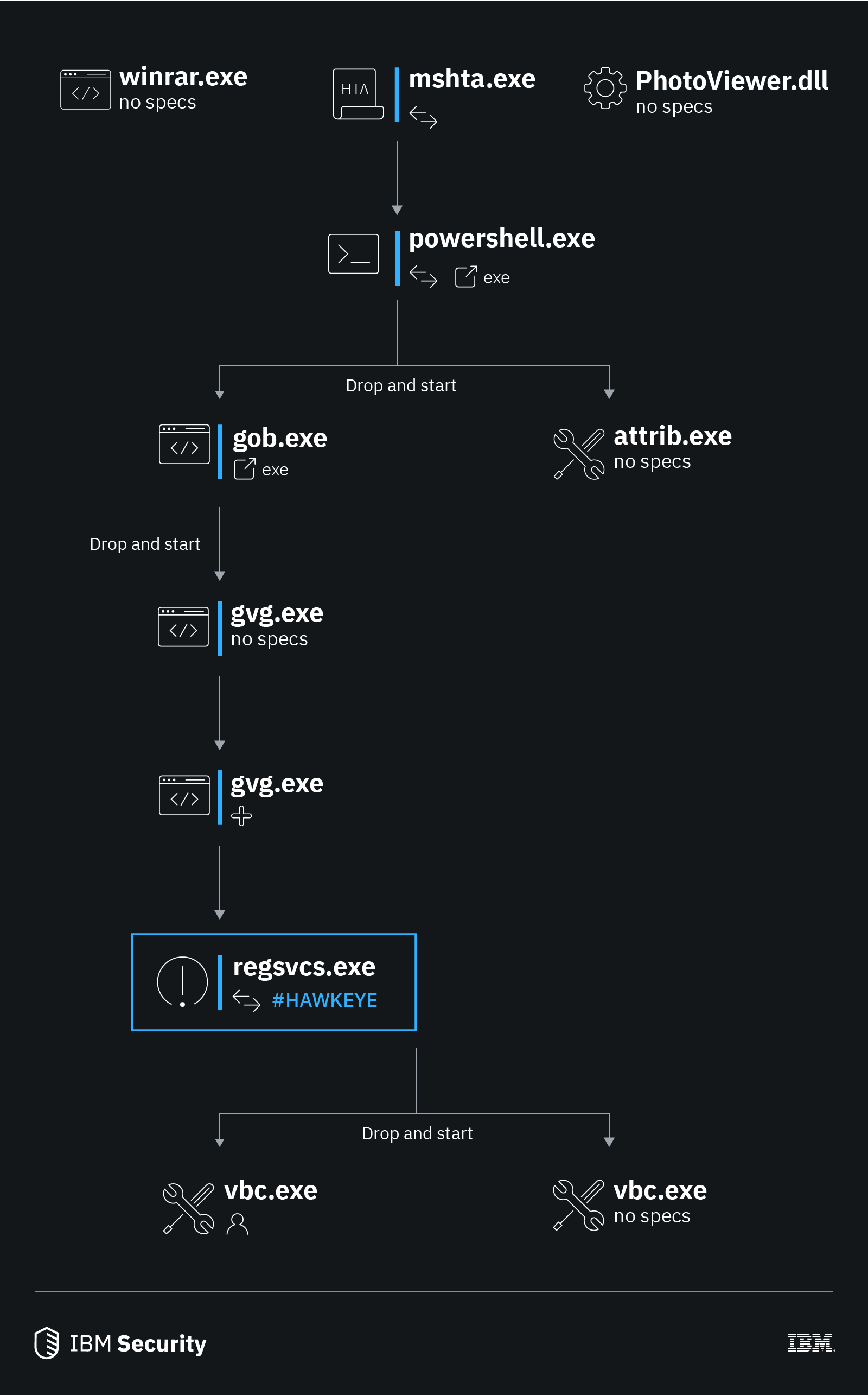
In the last six years, malware got multiply additional modules that extend opportunities for spying and stealing information. Next keylogger’s version, HawkEye Reborn 9, can collect information from different applications and send it to operators, using FTP, HTTP and SMTP protocols.
Experts say that in December 2018 program came to other owner and now is spread on DarkNet forums through intermediaries.
“Recent owner’s change and renewed process of HawkEye Reborn development demonstrate that this threat will develop in future”, – noted researchers from Cisco Talos.
- Block malicious and suspicious IPs from interacting with their users.
- Expect and warn about trending attacks and educate both management and users on new formats and ploys.
- Become aware of new attack tactics, techniques and procedures (TTPs) to better assess business risk relevant to the organization as cybercriminals evolve their arsenals.
Source: https://securityintelligence.com




