360 Netlab experts have discovered a new, very unusual botnet Gwmndy that attack Fiberhome routers.
The botnet is growing quite slowly – in just one day, only 200 devices are added to it.“Unlike typical botnets that are trying to infect as many victims as possible, this one stops searching for new bots, gaining 200 per day. It seems that his creator is satisfied with such a quantity, probably providing him with enough proxies for whatever”, — the researchers said.
The second distinguishing feature of the botnet is its purpose. Unlike most botnets, it is not used neither for DDoS attacks, nor for crypto jacking, nor for spamming, nor for stealing information.
The botnet’s sole purpose is to change the router’s settings so that it turns into a proxy host for SSH tunneling. Why its operators need this is not clear.
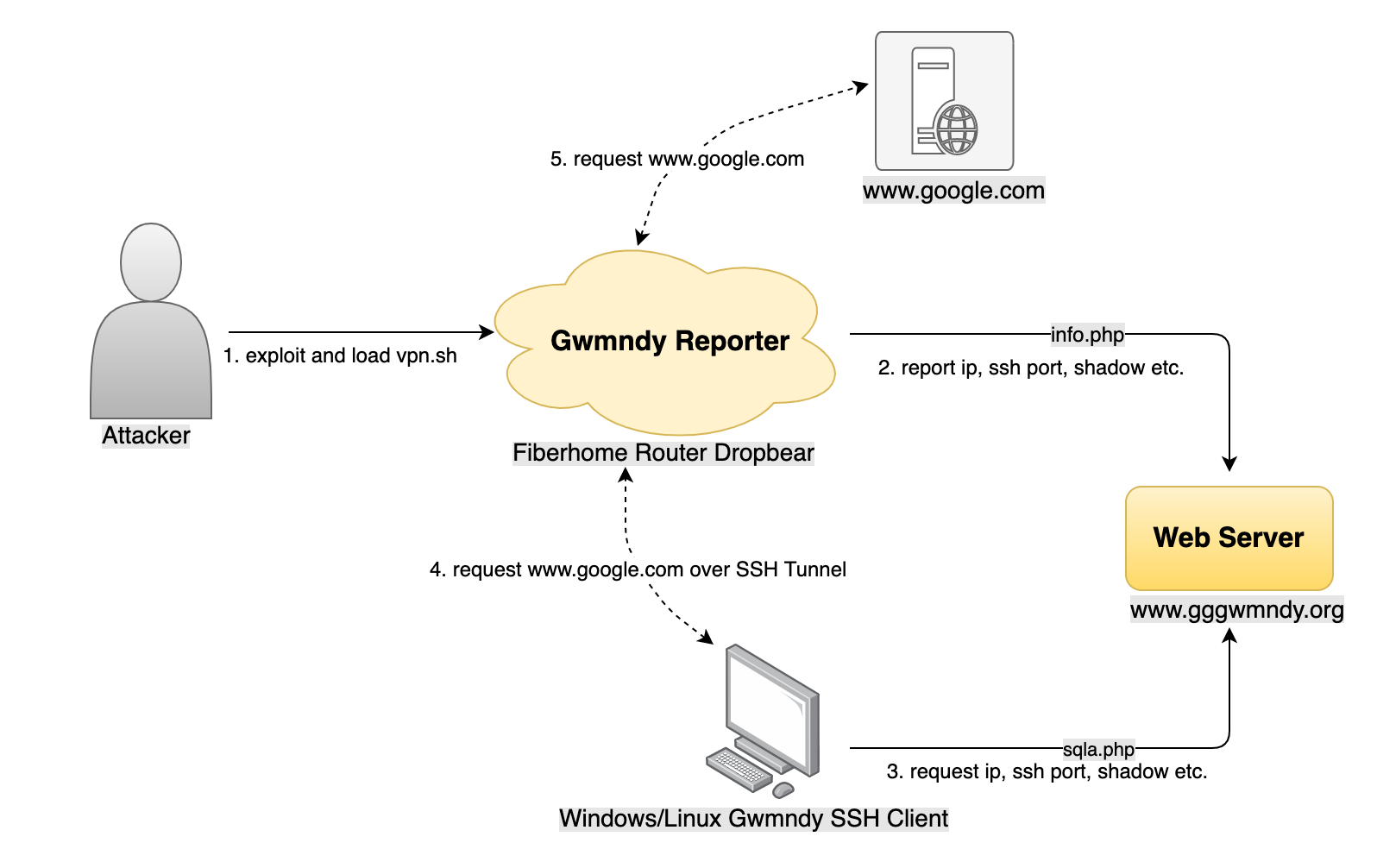
To infect routers, attackers use previously unknown Gwmndy software. Infection occurs using an executable file in ELF format, which gets to the device in one of many standard ways.
“We did not see how Gwmndy spreads, but we know that some Fiberhome routers use very weak passwords and have in abundance vulnerabilities”, — the researchers explained.
Once on the device, the malware installs a backdoor, and also creates an SSH tunnel for dynamic port forwarding and a local SOCKS5 service. According to the researchers, malware acting as a proxy is a rare case.
Read also: The new version of the banking Trojan TrickBot “kicks off” Windows Defender
Some malicious programs use a proxy or TOR to connect to their C&C servers, while others transmit data in clear text without a proxy. However, malware, which is a proxy in itself and can be used by other programs downloaded with it, deserves close attention, insist experts.
360 Netlab Professional Tips
We especially recommend home broadband users to update the Fiberhome router software system in a regular manner, and set up complex login credentials for the router Web.




