Bitcoin miner virus, also known as trojan-miner, is a type of computer virus that uses your computer to mine cryptocurrencies. This process may lead to unwanted consequences, such as lag spikes, performance degradation, or even component failure. In this article, I will tell you how to detect the malware presence on your PC, and also will help you to remove this dangerous virus.
What is the bitcoin miner virus and why is it so popular?
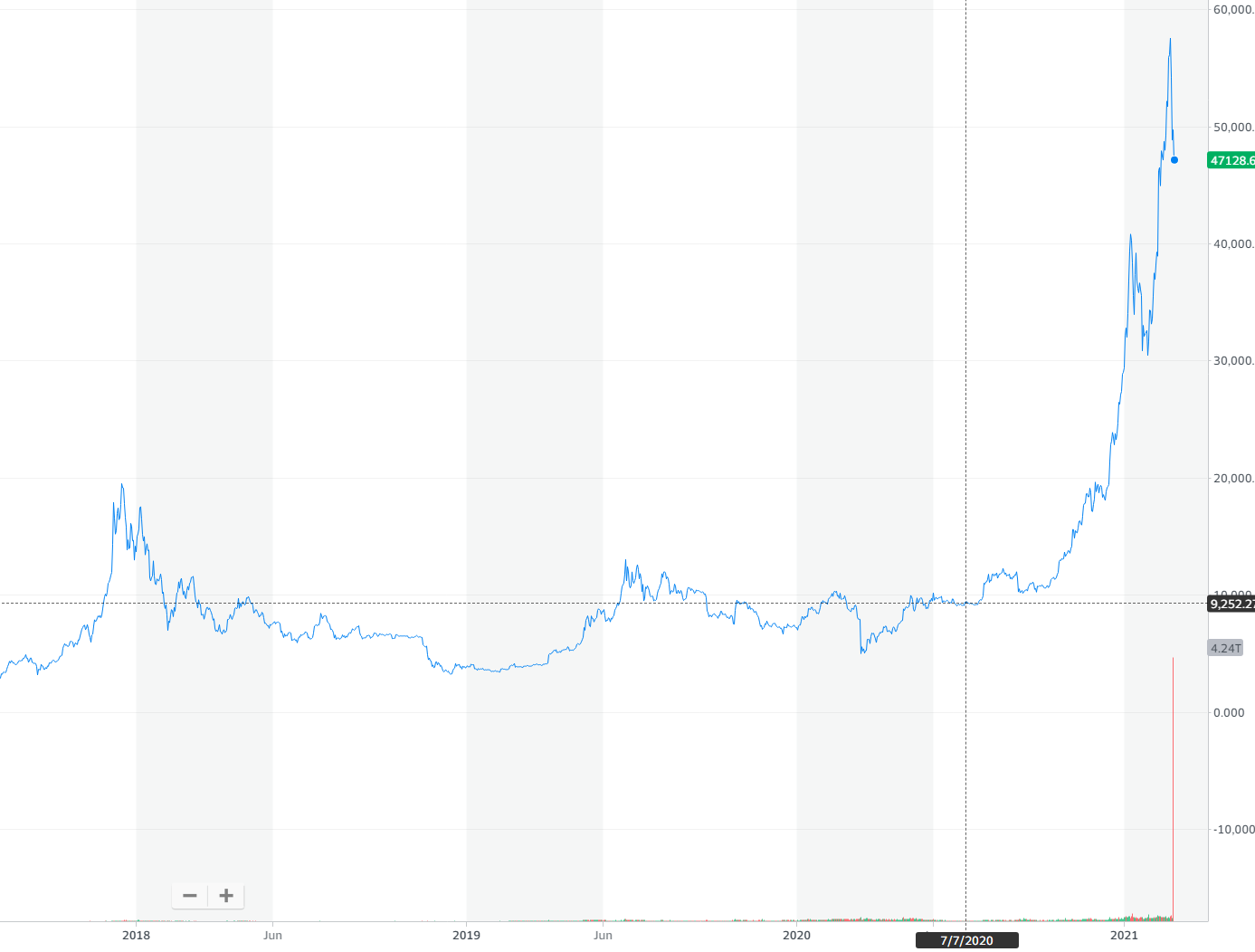
The popularity of trojan-miners becomes obvious when you have a look at a Bitcoin (and altcoins) price curve. It showed an exponential increase at the edge of 2018, and grew even more in 2020-2021. The enormous profits were always a lure for criminals, and cryptocurrencies are not an exclusion. Even more, the temptation to use illegal methods appeared when the GPU prices rose significantly, and so did the crypto mining farms’ prices.
The process of mining requires very powerful hardware, and the top-tier mining farms are sold for hundreds of thousands (or even millions!) of dollars. These farms are, exactly, just a large block of computers, which are running with a single task – calculating the blockchain block hash. To maximize the performance, such constructions must have the best cooling systems and power supplies. And since it is a very and very expensive process, the creators of the bitcoin miner virus decided to make a profit in an outlaw way.
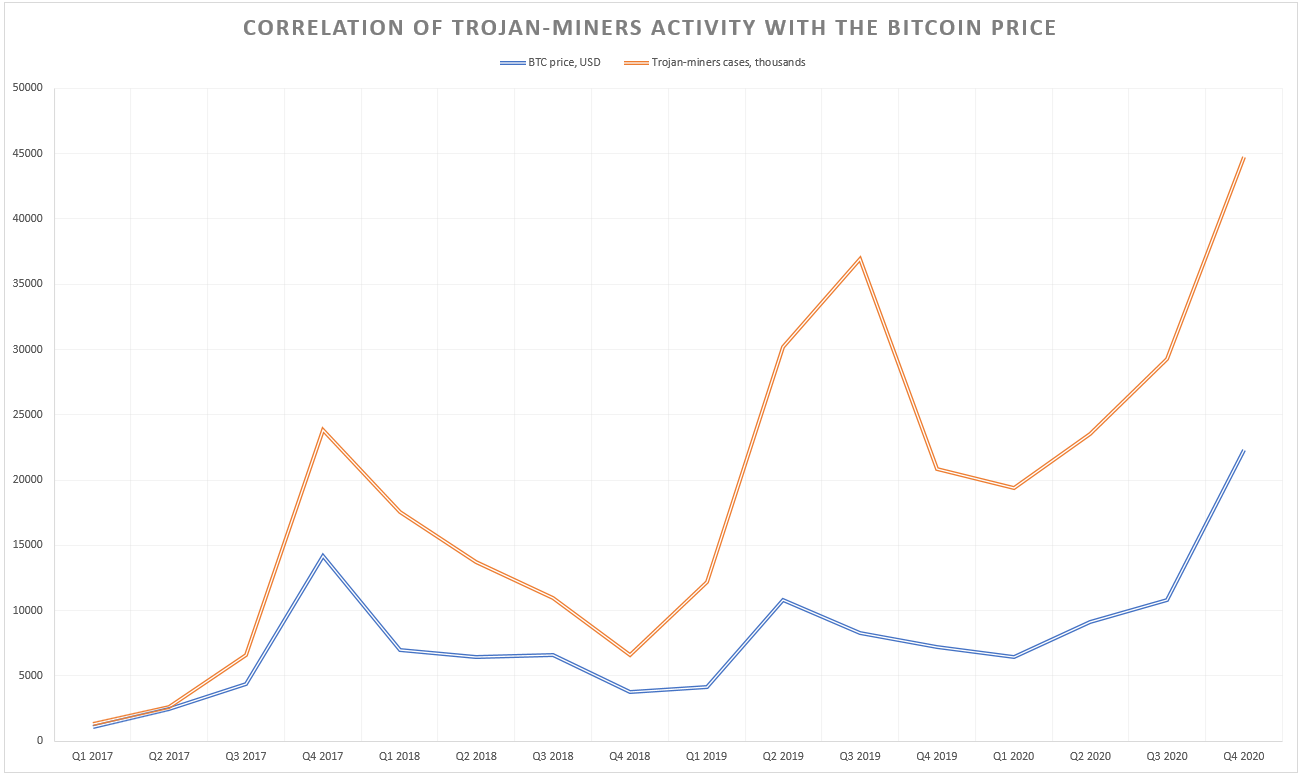
The Bitcoin miner virus mechanism was slightly described in the first paragraph. It makes use of your processor and GPU in order to mine different cryptocurrencies. That virus makes the same hash calculations, however, in contrast to the mining farms, it does this action on your main system. And since the mining process is extremely hardware intensive, all resources of your PC are consumed. As a result, it is very hard to perform the usual actions – you may struggle even on browser usage.
How dangerous is the bitcoin miner virus?
A lot of users think that bitcoin miner viruses are not dangerous for their PCs. Their logic is next: it doesn’t harm my personal data, and cannot damage my hardware, so I can put off the solution moment. And such statements may be right if all facts are true. But they don’t. The possible harmful effects for your data are hidden in the origins of trojan-miner. The cases when it is delivered solitary are very rare – usually, there is also something like worm or spyware inside. Hence, for coin miners distributors it is very easy to make money not only with money but also with data selling.
Hardware components may also be in danger. Of course, if there are no serious issues, like a pound of dust on the cooling fan, broken fan blade, or so, the chance of getting the problems is relatively low. But if we are talking about old PCs, or laptops, which have never been cleaned from dust or checked on mechanical issues, you can easily discover that your CPU or GPU are overheating. Modern chips are equipped with overheating protection, so the processor failure chance is minimal. Nonetheless, the systems with obsolete processors are still widespread, and the possibility of bad consequences for them is quite high.
How did I get this virus?
There are many ways of getting a bitcoin miner virus on your PC. In contrast to ransom trojans, which are deploying ransomware and a pack of other viruses, they are usually downloaded by other trojan viruses. And the most popular methods for so-called trojan-downloaders are cracking programs (KMS Pico, KMS Tools, and others) and different dubious programs. Last are placing themselves as “system optimizers” or so. A less popular method of coin miner injection is the adware bundle, which contains this virus as a component of a big pack of malware.
Both of these ways are extremely easy to avoid. To be safe from trojan-miners, do not use any untrusted utilities, especially if your antivirus program shows you the notifications that this tool is possibly dangerous. Adware injection usually happens after clicking the advertisement somewhere on the Web. Installing AdBlock and cutting the habit of clicking the bright and blinking ads on different websites will secure you of this source of malware injection.
How to remove the malware from my computer?
Coin miners are very stealthy viruses: the more time they will be active, the more money they will bring to their distributors. You can spot the suspicious process in Task Manager, but stopping it and removing this process from the root directory is only a partial action. To remove it completely, use anti-malware software. In my opinion, GridinSoft Anti-Malware will be the best for this task.
Bitcoin miner virus is getting on the nerves of many users, so you’re not its only victim.
People ask how to fix the problem effectively. Getting rid of the infection manually may be a long-lasting undertaking and can damage other important system files. Scan your PC with GridinSoft Anti-Malware to detect and delete Luckymedia in the right way.

GridinSoft Anti-Malware Review, How to get free trial?, EULA, and Privacy Policy.
The basic solution – Microsoft Defender, which is present on each PC with Windows 10, has several critical disadvantages. First, it consumes a lot of hardware capacities, so the users usually disable it in order to make the PC performance better. Another problem is that this security tool can easily be disabled through the Group Policies. Malware creators know about this vulnerability and exploit it as often as possible.
Follow the steps in the slider explaining how to use GridinSoft Anti-Malware.
- Step 1. Download GridinSoft Anti-Malware. Click on its installer in the left-bottom section of your browser.
- Step 2. Allow changes to be made via User Account Control.
- Step 3. Click on “Install” to install the program.
- Step 4. Wait until the program is fully installed into your PC.
- Step 5. Click on “Finish“.
- Step 6. Run the program. Wait until scanning is completed and all malware linked with “Franchemduty.work” is detected.
- Step 7. Click on “Clean Now” for remove virus.
- Step 8. Select the license type and purchase the program. Remove all identified threats with purchased version of the software.