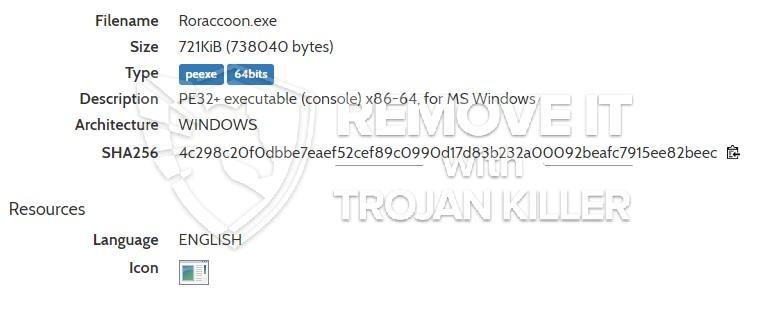
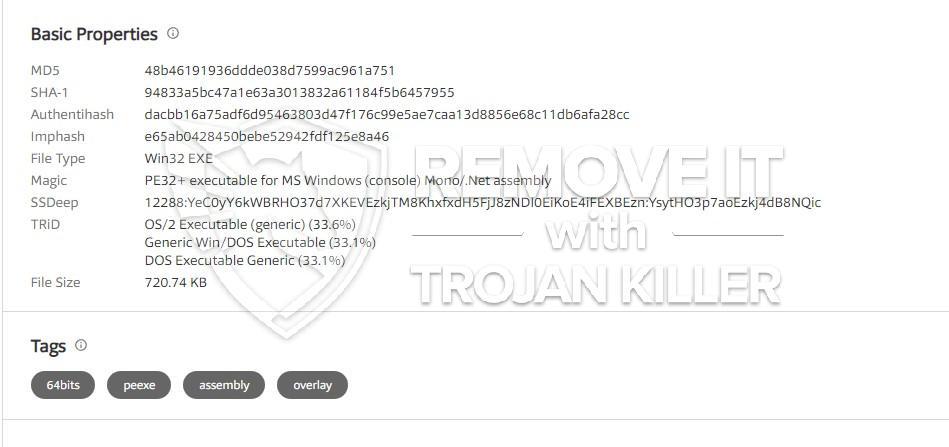
Trojan.Roraccoon is a generic detection used by Microsoft Security Essentials, Windows Defender and other anti-virus items for a file that appears to have trojan-like features or habits.
Trojan.Roraccoon consists of harmful or possibly undesirable software which downloads and sets up on the afflicted system. Typically, this infection will set up a backdoor which permits remote, surreptitious access to contaminated systems. This backdoor might then be utilized by remote opponents to upload and set up more destructive or potentially undesirable software application on the system.
What is the Trojan.Roraccoon infection?
Trojan.Roraccoon is a trojan that calmly downloads and installs other programs without authorization. This could include the setup of additional malware or malware components to an affected PC.
Trojan.Roraccoon is a is a broad category used by Microsoft Security Essentials, Windows Defender and other anti-viruses engines a file that appears to have trojan-like features or behavior for software that exhibits suspicious habits classified as possibly malicious.
Trojan.Roraccoon is a trojan that silently downloads and sets up other programs without consent. This might include the installation of extra malware or malware components to an affected computer.
The Behavior Monitoring function observes the habits of processes as they run programs. If it observes a procedure behaving in a potentially destructive way, it reports the program the process is running as possibly destructive.
Due to the generic nature of this detection, techniques of setup may differ. The Trojan.Roraccoon infections might often install themselves by copying their executable to the Windows or Windows system folders, and then modifying the computer system registry to run this file at each system start. Trojan.Roraccoonwill frequently customize the following subkey in order to achieve this:
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
Trojan.Roraccoon might get in touch with a remote host at opencapture.co.kr using port 80. Commonly, malware may contact a remote host for the following purposes:.
- To report a brand-new infection to its author.
- To get configuration or other data.
- To download and carry out arbitrary files (including updates or extra malware).
- To receive direction from a remote enemy.
- To upload information taken from the affected computer system.
Is Trojan.Roraccoon a False Positive?
Files reported as Trojan.Roraccoon are not necessarily destructive. For instance, users can be deceived into utilizing non-malicious programs, such as Web browsers, to unconsciously perform harmful actions, such as downloading malware. Some otherwise harmless programs might have defects that malware or assailants can make use of to perform malicious actions. Must you be uncertain regarding whether a file has actually been reported properly, we encourage you to send the affected file to https://www.virustotal.com/en/ to be scanned with multiple antivirus engines.
How did Trojan.Roraccoon infection got on my computer?
The Trojan.Roraccoon virus is dispersed through several means. Harmful sites, or genuine websites that have actually been hacked, can contaminate your maker through exploit sets that use vulnerabilities on your computer system to install this Trojan without your consent of understanding.
Another approach used to propagate this kind of malware is spam email consisting of infected attachments or links to destructive sites. Cyber-criminals spam out an email, with created header information, fooling you into believing that it is from a shipping company like DHL or FedEx. The email tells you that they tried to provide a package to you, but failed for some factor. Sometimes the emails claim to be notices of a shipment you have actually made. In any case, you can’t resist wondering as to what the email is describing- and open the connected file (or click on a link ingrained inside the e-mail). And with that, your computer system is contaminated with the Trojan.Roraccoon virus.
The threat might also be downloaded manually by fooling the user into believing they are setting up a helpful piece of software application, for example a phony upgrade for Adobe Flash Player or another piece of software application.
Trojan.Roraccoon removal process
STEP 1. First of all, you need to download and install GridinSoft Anti-Malware.
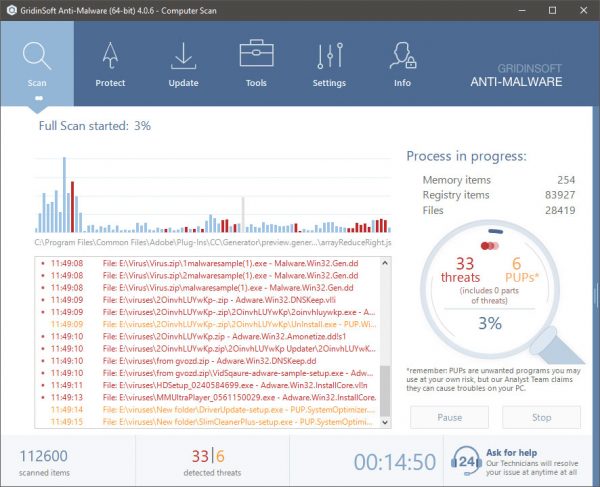
STEP 2. Then you should choose “Quick scan” or “Full scan”.
STEP 3. Run to scan your computer
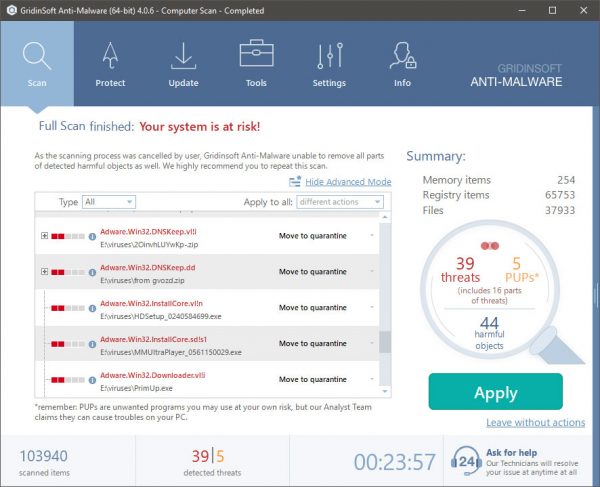
STEP 4. After the scan is completed, you need to click on “Apply” button to remove Trojan.Roraccoon
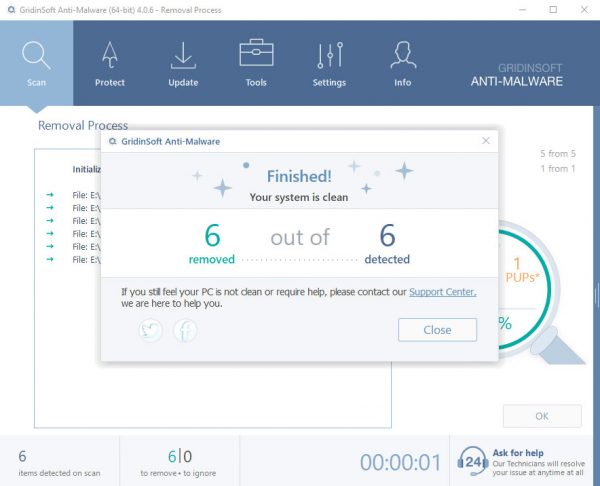
STEP 5. Trojan.Roraccoon Removed!
Video Guide: How to use GridinSoft Anti-Malware for remove Trojan.Roraccoon
Video Guide: How to use GridinSoft Anti-Malware for reset browser settings
How to prevent your PC from being reinfected with “Trojan.Roraccoon” in the future.
A Powerful Antivirus solution that can detect and block fileless malware is what you need! Traditional solutions detect malware based on virus definitions, and hence they often cannot detect “Trojan.Roraccoon”. GridinSoft Anti-Malware provides protection against all types of malware including fileless malware such as “Trojan.Roraccoon”. GridinSoft Anti-Malware provides cloud-based behavior analyzer to block all unknown files including zero-day malware. Such technology can detect and completely remove “Trojan.Roraccoon”.