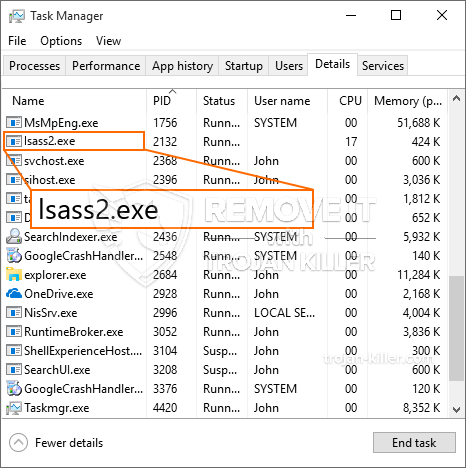
A brand-new, extremely dangerous cryptocurrency miner virus has actually been found by protection scientists. The malware, called Lsass2.exe can infect target victims utilizing a variety of methods. The essence behind the Lsass2.exe miner is to employ cryptocurrency miner activities on the computers of victims in order to get Monero tokens at victims expense. The outcome of this miner is the elevated electrical power expenses and also if you leave it for longer time periods Lsass2.exe might also damage your computer systems components.
Lsass2.exe: Distribution Methods
The Lsass2.exe malware utilizes two preferred techniques which are utilized to contaminate computer targets:
- Payload Delivery through Prior Infections. If an older Lsass2.exe malware is released on the sufferer systems it can instantly update itself or download a newer variation. This is possible using the built-in upgrade command which acquires the release. This is done by connecting to a specific predefined hacker-controlled server which supplies the malware code. The downloaded and install infection will certainly obtain the name of a Windows solution and be placed in the “%system% temp” area. Crucial residential or commercial properties as well as running system arrangement data are changed in order to allow a consistent and also silent infection.
- Software Application Vulnerability Exploits. The newest variation of the Lsass2.exe malware have actually been discovered to be caused by the some exploits, widely understood for being made use of in the ransomware strikes. The infections are done by targeting open services using the TCP port. The attacks are automated by a hacker-controlled structure which searches for if the port is open. If this problem is met it will check the solution and fetch info regarding it, consisting of any kind of variation and also setup data. Ventures and prominent username and password mixes might be done. When the make use of is set off against the susceptible code the miner will be released along with the backdoor. This will provide the a double infection.
Apart from these techniques various other approaches can be used too. Miners can be dispersed by phishing e-mails that are sent out in bulk in a SPAM-like fashion as well as rely on social engineering techniques in order to puzzle the sufferers right into thinking that they have obtained a message from a legitimate service or company. The infection data can be either straight connected or inserted in the body contents in multimedia content or text web links.
The criminals can additionally develop malicious touchdown web pages that can pose supplier download web pages, software application download websites as well as other regularly accessed locations. When they make use of similar sounding domain names to legit addresses as well as safety certificates the users may be coerced into communicating with them. In some cases just opening them can set off the miner infection.
Another technique would certainly be to make use of payload carriers that can be spread utilizing the above-mentioned approaches or via data sharing networks, BitTorrent is one of the most preferred ones. It is regularly used to distribute both legitimate software application as well as data and also pirate material. 2 of one of the most preferred payload carriers are the following:
Various other methods that can be taken into consideration by the bad guys consist of using internet browser hijackers -unsafe plugins which are made suitable with the most popular web internet browsers. They are uploaded to the relevant repositories with fake customer reviews and also programmer qualifications. In most cases the summaries may include screenshots, videos as well as intricate summaries promising terrific attribute enhancements and also efficiency optimizations. Nevertheless upon installment the habits of the affected browsers will certainly alter- customers will certainly discover that they will be rerouted to a hacker-controlled landing page and also their settings could be changed – the default web page, search engine and also new tabs web page.
Lsass2.exe: Analysis
The Lsass2.exe malware is a traditional instance of a cryptocurrency miner which relying on its arrangement can trigger a variety of unsafe actions. Its primary objective is to execute complex mathematical tasks that will make use of the available system sources: CPU, GPU, memory and also hard drive area. The means they operate is by connecting to a special web server called mining swimming pool where the called for code is downloaded. As quickly as one of the tasks is downloaded it will be started simultaneously, numerous circumstances can be gone for once. When a provided job is finished an additional one will certainly be downloaded and install in its location and also the loophole will proceed until the computer is powered off, the infection is eliminated or one more similar event happens. Cryptocurrency will be rewarded to the criminal controllers (hacking team or a solitary cyberpunk) straight to their wallets.
A hazardous attribute of this category of malware is that examples such as this one can take all system resources and practically make the victim computer pointless until the danger has actually been entirely gotten rid of. Most of them include a persistent installment which makes them truly challenging to eliminate. These commands will certainly make modifications to boot choices, configuration documents and also Windows Registry values that will certainly make the Lsass2.exe malware begin instantly once the computer is powered on. Accessibility to healing menus and choices may be blocked which provides lots of hand-operated elimination guides virtually useless.
This certain infection will certainly configuration a Windows service for itself, complying with the carried out safety evaluation ther adhering to activities have been observed:
. During the miner procedures the associated malware can hook up to currently running Windows solutions as well as third-party mounted applications. By doing so the system administrators may not discover that the source tons comes from a different process.
| Name | Lsass2.exe |
|---|---|
| Category | Trojan |
| Sub-category | Cryptocurrency Miner |
| Dangers | High CPU usage, Internet speed reduction, PC crashes and freezes and etc. |
| Main purpose | To make money for cyber criminals |
| Distribution | Torrents, Free Games, Cracked Apps, Email, Questionable Websites, Exploits |
| Removal | Install GridinSoft Anti-Malware to detect and remove Lsass2.exe |
id=”81268″ align=”aligncenter” width=”600″] Lsass2.exe
Lsass2.exe
These sort of malware infections are specifically effective at executing innovative commands if set up so. They are based upon a modular structure permitting the criminal controllers to coordinate all sort of hazardous habits. Among the preferred examples is the alteration of the Windows Registry – adjustments strings associated by the os can create serious efficiency disruptions and also the lack of ability to access Windows services. Depending upon the extent of adjustments it can likewise make the computer system completely unusable. On the other hand adjustment of Registry values belonging to any type of third-party mounted applications can undermine them. Some applications may stop working to introduce completely while others can all of a sudden stop working.
This specific miner in its present variation is focused on extracting the Monero cryptocurrency consisting of a customized variation of XMRig CPU mining engine. If the projects verify effective then future versions of the Lsass2.exe can be introduced in the future. As the malware utilizes software susceptabilities to contaminate target hosts, it can be part of a hazardous co-infection with ransomware and Trojans.
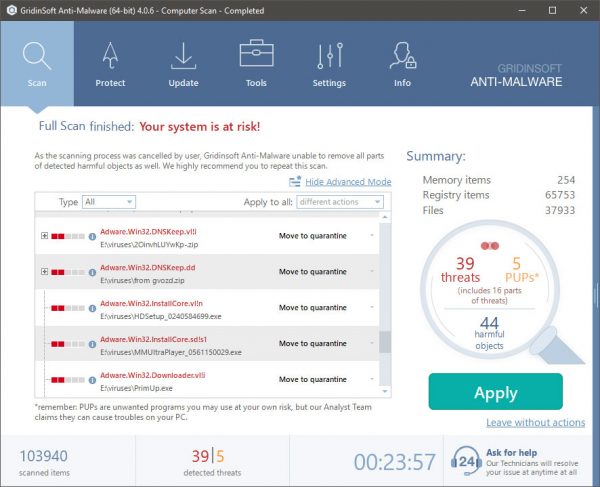
Removal of Lsass2.exe is strongly advised, because you risk not only a large electricity bill if it is working on your COMPUTER, however the miner might also perform various other undesirable tasks on it and even damage your PC completely.
Lsass2.exe removal process
STEP 1. First of all, you need to download and install GridinSoft Anti-Malware.
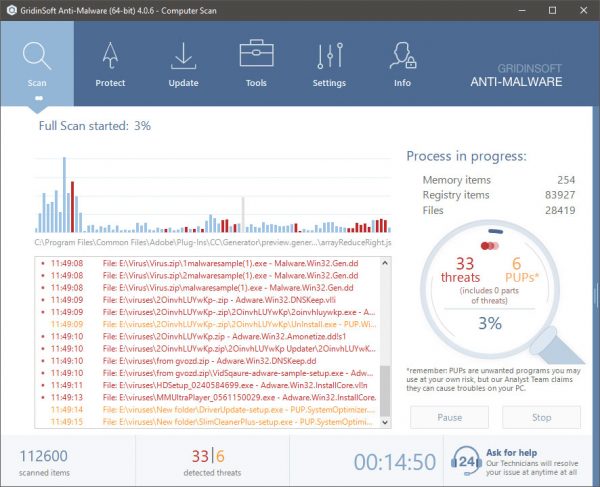
STEP 2. Then you should choose “Quick scan” or “Full scan”.
STEP 3. Run to scan your computer
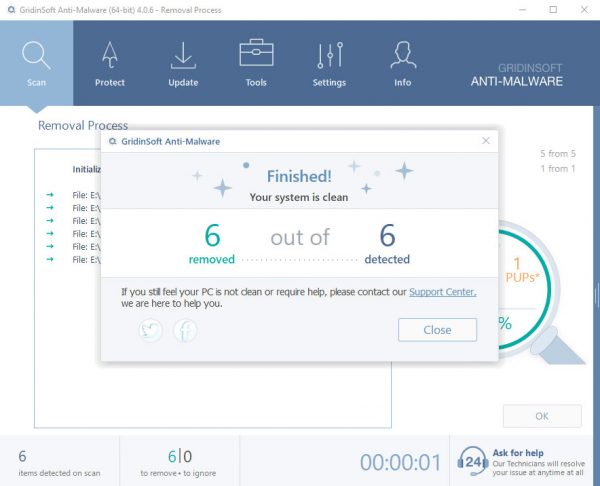
STEP 4. After the scan is completed, you need to click on “Apply” button to remove Lsass2.exe
STEP 5. Lsass2.exe Removed!
Video Guide: How to use GridinSoft Anti-Malware for remove Lsass2.exe
How to prevent your PC from being reinfected with “Lsass2.exe” in the future.
A Powerful Antivirus solution that can detect and block fileless malware is what you need! Traditional solutions detect malware based on virus definitions, and hence they often cannot detect “Lsass2.exe”. GridinSoft Anti-Malware provides protection against all types of malware including fileless malware such as “Lsass2.exe”. GridinSoft Anti-Malware provides cloud-based behavior analyzer to block all unknown files including zero-day malware. Such technology can detect and completely remove “Lsass2.exe”.