Nemty ransomware developers continue to improve their malware


Nemty ransomware developers continue to actively work on their malware, developing it in an effort to increase interest to the product on underground forums.
Attackers made changes to the nature of their actions in the victim’s system. Now the program can not only encrypt files, but also terminate processes and services that interfere with this task.For the first time, Nemty came to the attention of information security specialists in mid-August. Over the past month, virus writers managed to release a new version of the malware under number 1.4, in which they corrected the errors found and added a stop list.
Read also: Another 0-day vulnerability discovered in Android
The program began to limits its activitiy if the target system was in Russia, Belarus, Kazakhstan, Tajikistan or Ukraine.
Recently, information security researcher Vitali Kremez found out that the authors of the encryptor, without changing the version number, made the next adjustments. The number of geographical regions from the stop list has replenished with Azerbaijan, Armenia, Moldova and Kyrgyzstan that have been added to them.

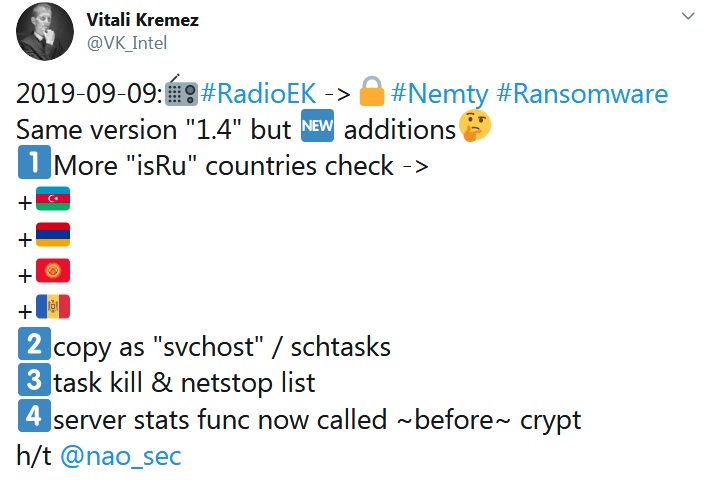
However, the main innovation has become a feature that makes Nemty’s behavior much more aggressive. The code added by the developers can forcibly terminate the processes running on the system, so that, among others, the files opened by the victim can be encrypted.
The main targets of the malware are nine Windows programs and services, including WordPad and Microsoft Word text editors, Microsoft Excel application, Microsoft Outlook and Mozilla Thunderbird email clients, SQL service and VirtualBox virtualization software.
According to Bleeping Computer, the last two items on this list give reason to think that large companies and corporations are most interested in potential victims of criminals.
“There is reason to believe that attackers will not stop in the search for the most effective ways of delivering malware to target systems. At the moment, they have already tested the infection through vulnerable RDP connections, as well as using the fake PayPal page”, — says Ionut Ilascu, one of the authors of Bleeping Computer.
Since criminals have already used one of the exploit packs – RIG, which exploits vulnerabilities in Internet Explorer, Java, Adobe Flash, and Silverlight – they may also resort to other sets of exploits.
Recent Posts
Remove Curestin.co.in Pop-up Ads
About Curestin.co.in Curestin.co.in pop-ups can not introduce out of nowhere. If you have actually clicked…
Remove Asyetaprovinc.org Pop-up Ads
About Asyetaprovinc.org Asyetaprovinc.org pop-ups can not expose out of the blue. If you have actually…
Remove Hotbxokihi.cc Pop-up Ads
About Hotbxokihi.cc Hotbxokihi.cc pop-ups can not expose out of nowhere. If you have clicked some…
Remove Hotbyavaye.today Pop-up Ads
About Hotbyavaye.today Hotbyavaye.today pop-ups can not open out of nowhere. If you have actually clicked…
Remove Easydefender.site Pop-up Ads
About Easydefender.site Easydefender.site pop-ups can not expose out of nowhere. If you have clicked on…
Remove Hotbmurumi.cc Pop-up Ads
About Hotbmurumi.cc Hotbmurumi.cc pop-ups can not open out of the blue. If you have actually…

