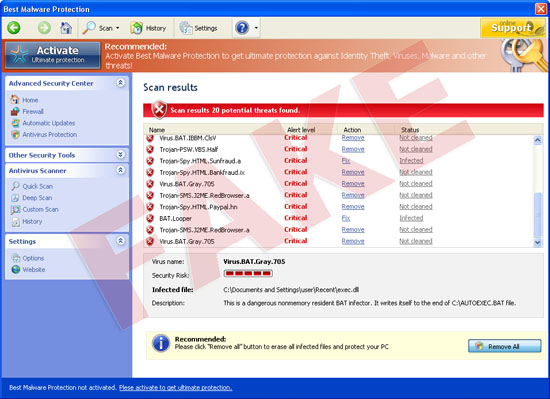
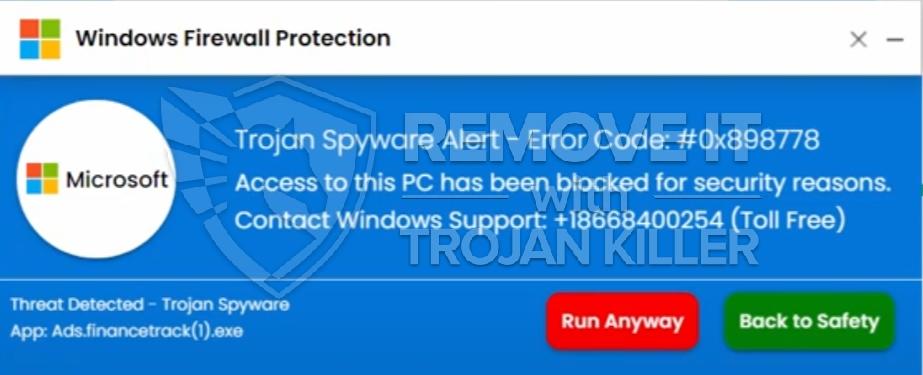
Please be urgently advised of new malware made by the load of crooks – it is named Best Malware Protection. It is a direct successor of Internet Security Essentials virus, of which we told you in one of our previous posts. It has the only aim – to deceive unwary users and obtain money from them. Our goal is to warn you about this threat which can essentially damage the security of your PC. After encountering certain strange unfamiliar application in your computer named Best Malware Protection you must get rid of it without loitering.
Best Malware Protection penetrates inside of the PC via trojan downloaded or infiltrates itself when users click on it. It penetrates without asking for user’s consent or approval. Upon successful installation Best Malware Protection will show fake security notifications on your computer. Best Malware Protection totally ignores the authentication barriers as the restriction, since it is capable of installing itself without user’s desire. Upon penetration into the PC, Best Malware Protection will “invite” additional files and amend your system in such a way that it will be launched with every Windows startup. Immediately Best Malware Protection fake antivirus starts telling users plenty of fairy-tales about poor level of PC security. You will be bombarded by fake and deceitful alerts and same fake scanners. Best Malware Protection will tell of non-existent threats, system and registry problems and then it suggests to purchase full version of Best Malware Protection. Please do not trust it under any circumstances. Best Malware Protection malware claims that it is capable of providing excellent defense for your system and that it can repair all errors in your machine. It is a deception for all unwary users. Best Malware Protection just tries to steal money from you without giving you any decent protection that your computer requires so badly.
Please carefully read the instructions stipulated below and find out how to eliminate Best Malware Protection malady. It is our job to assist you in this important and uneasy task, this is why we have elaborated automatic and manual removal advises. You may find them stipulated below.
Best Malware Protection automatic remover:
1. Download the latest version of GridinSoft Trojan Killer to clear (not infected) computer and install it.
2. Update the virus database.
3. Copy the entire folder “GridinSoft Trojan Killer” to your jump drive (memory stick). Normally it is located at the following path: (C:\Program Files\GridinSoft Trojan Killer). “C” stands for the system disk of your computer. The name of the system disk, however, can be marked with another letter.
4. Open your jump drive (memory stick). Find the folder “GridinSoft Trojan Killer” there. Open it , find the file under the name “trojankiller.exe” and rename it to “iexplore.exe”.
5. Move memory stick to infected PC, open “GridinSoft Trojan Killer” folder and run iexplore.exe. Optional: copy the folder “GridinSoft Trojan Killer” from your jump drive to some other folder created on your PC and run “iexplore.exe”.
Best Malware Protection manual removal guide:
Instructions on how to restore your Internet connection:
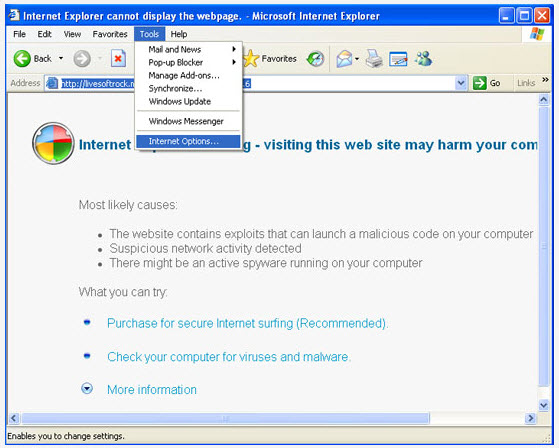
1. Start Internet Explorer and click on the Tools menu and then select Internet Options as shown in the image below:
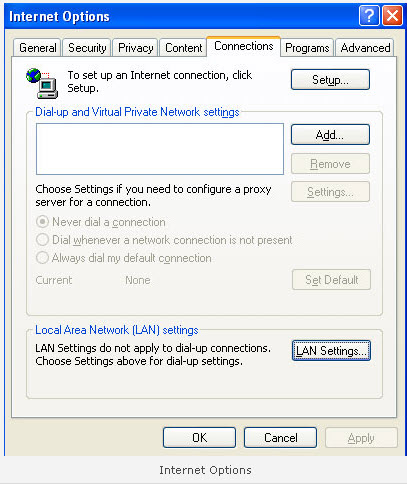
2. Select Connections tab and now click on the Lan Settings button as shown in the image below:
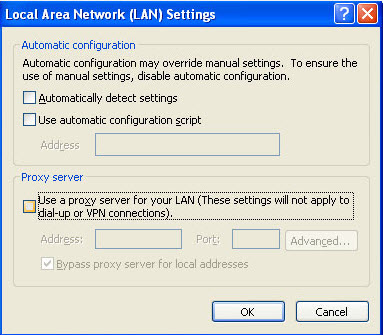
3. Under the Proxy Server section uncheck the checkbox “Use a proxy server for your LAN” and press the OK button to close this screen:
Delete Best Malware Protection files:
%CommonAppData%\[random]
%CommonAppData%\[random]\[random].exe
%CommonAppData%\[random]\[random].mof
%CommonAppData%\[random]\[random].dll
%CommonAppData%\[random]\[random].ocx
%CommonAppData%\[random]\[random]
%AppData%\Best Malware Protection
%AppData%\Best Malware Protection\cookies.sqlite
%AppData%\Best Malware Protection\Instructions.ini
Delete Best Malware Protection registry entries:
HKCR\PersonalSS.DocHostUIHandler
HKCU\Software\Microsoft\Internet Explorer\Download “RunInvalidSignatures” = “1?
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings “ProxyServer” = “http=127.0.0.1?
HKCU\Software\Microsoft\Windows\CurrentVersion\Run “Best Malware Protection”
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options “Debugger” = “svchost.exe”