VXUG is a ransomware strain, which appeared on October 25, 2024. It belongs to CryLock ransomware family, considering its code similarities and behavior. Upon infection, VXUG encrypts and renames files, generating a ransom note named “how_to_decrypt.hta”. The ransomware modifies filenames by appending an email address, a unique identifier, and a victim-specific ID. The files end up looking like cat.jpg[staff@vx-underground.org][1].[F27195A8-B7BFB093] (cat.jpg before the encryption).
In this article, I will share my analysis of this virus, explain how this happened and how you can restore the files.
Ransom Note overview
The VXUG ransom note warns victims that their documents, databases, backups, and other files have been encrypted with AES encryption due to vulnerabilities found in the system. To restore access to their data, victims are instructed to purchase a decryption key directly from the attackers.
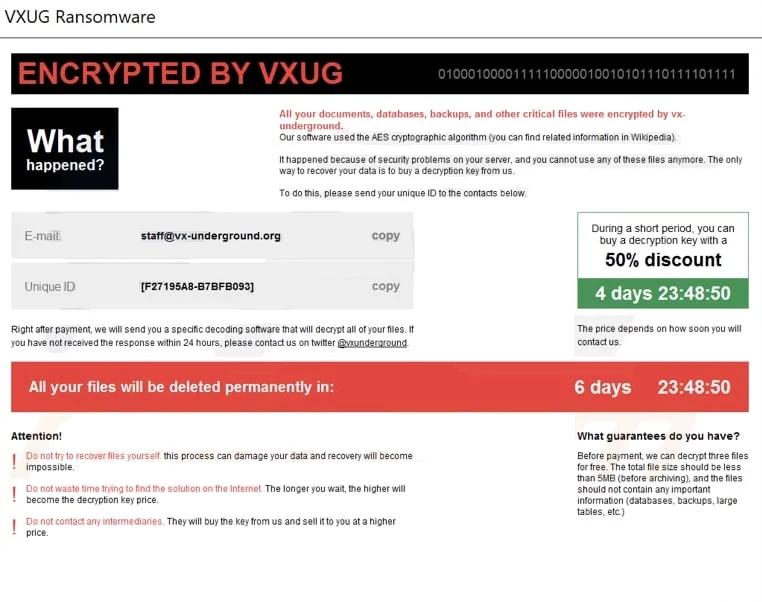
To proceed, victims are asked to send their unique ID to the specified email (staff@vx-underground.org) or to reach out via Twitter (@vxunderground). The note also includes a limited-time offer of a 50% discount on the decryption key, while threatening permanent file deletion if the deadline is missed.
It is worth noting that this ransomware tries to set up VX-Underground, a famous malware analysis and collection service. They serve as a library of different threats for malware researchers, with useful insights into how malware operates and which tactics threat actors use in their attacks. Ransomware actors behind VXUG ransomware are by no means related to the actual VX-Underground, despite offering their contact email address and a Twitter handle as options to get the data back.
In a further attempt to persuade victims, the attackers offer to decrypt three small, non-sensitive files for free as proof of their decryption capabilities. That is an often tactic of fraudsters, aimed at showing that they really can help with the problem.
How did I get infected?
Ransomware can infect computers through several common methods. Using pirated software, cracking tools, key generators, or visiting deceptive or compromised websites with malicious ads are frequent sources of infection. Similarly, downloading files and software from P2P networks, third-party downloaders, or unreliable sources can introduce ransomware.
Interested in more information about ransomware? Consider checking out professional in-depth ransomware analysis here.
Fraudulent emails containing malicious links or attachments—like MS Office files, PDFs, archives, scripts, or executables—are a frequent strategy attackers use to trick users into activating ransomware. These techniques aim to lure users into unknowingly executing ransomware on their devices.
Certain ransomware samples also use services of dropper malware: a specific type of virus that acts as a gateway for other threats. It is much more stealthy than other types of malware, and can be present in the system for a long time, continuously deploying malicious software.
General ransomware details
Ransomware attacks often leave victims with limited options for file recovery, as only the attackers hold the specific decryption tools needed to access the encrypted data. Without recent backups or the availability of third-party decryption tools, victims typically face the difficult choice of paying a ransom. However, paying is a gamble—cybercriminals may not uphold their end of the deal, leaving victims without access even after payment.
Beyond initial encryption, ransomware poses an ongoing threat. If active on a device, it can encrypt additional files and spread across the network, infecting other machines. For these reasons, it’s crucial to promptly isolate and remove ransomware from systems to prevent further damage and minimize the risk of widespread data loss.
Ransomware Removal Guide
Before the recovery procedures, you should consider scanning your computer with a GridinSoft Anti-Malware in order to find any traces of the infection. Though some ransomware viruses are removing themselves right after the encryption of your files, some may leave malicious processes on your computer for special purposes of cyber criminals.
-
Run GridinSoft Anti-Malware and choose the scan type, which is suitable for your needs. Of course, for the accuratest scan results we recommend you to choose the “Full Scan”.
-
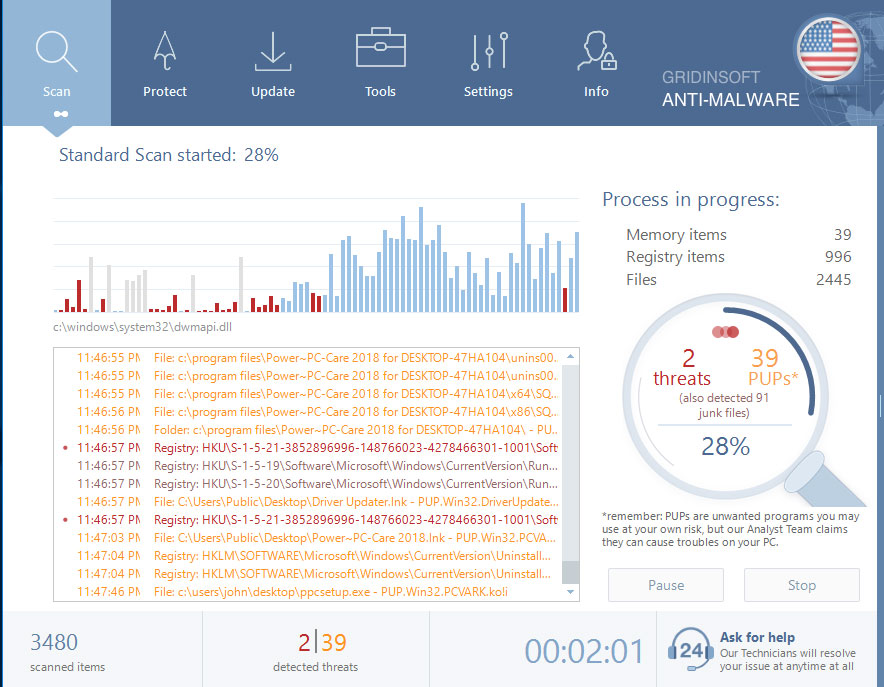
Give Anti-Malware a little time to check your system:
-
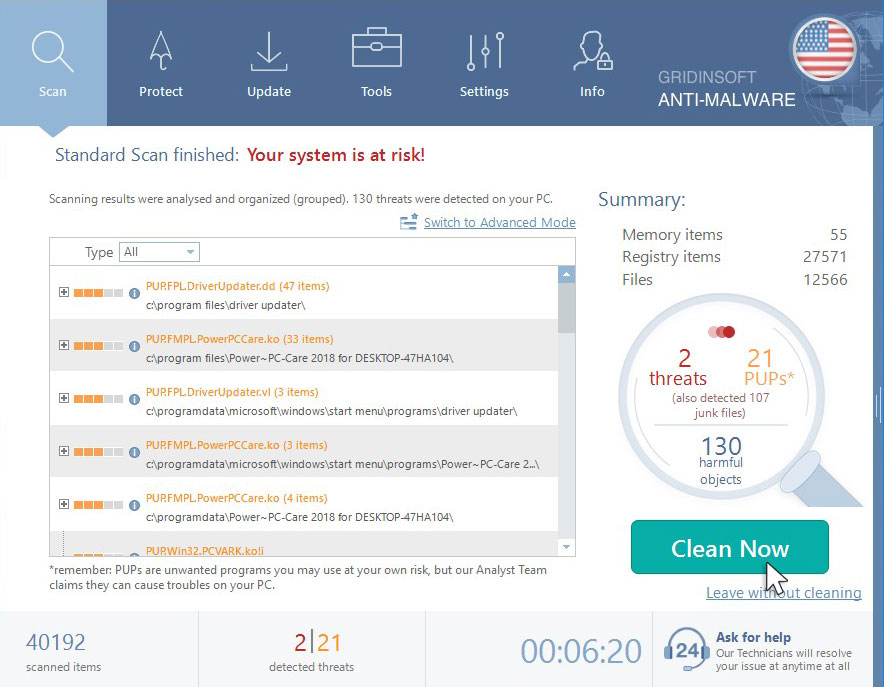
Move to quarantine all the viruses and unwanted files, that you see in the results list:
-
Enjoy the malware removal process:
-
Use of On-run protection may additionaly prevent different types of cyber attacks, our protect may flag the downloader of the ransomware as a malicious application preventing the download of the virus.
How to decrypt the files?
Unfortunately, this ransomware uses a rather strong encryption algorithm, which means it is not possible to get the files back for free. Moreover, you are unlikely to succeed with paying cybercriminals, as the contact information specified in ransom note directs to VX Underground, who has no relation to that virus. Thus, attempting to circumvent the decryption is the only way to get the files back.
Before proceeding to data recovery, I will heavily recommend you to follow the guide above to remove the threat from the system. Doing so is crucial to prevent further encryption and minimize spread across the network. Active ransomware can continue encrypting files and affect connected devices, making recovery even harder. By fully eliminating the threat first, you can secure the system, protect new data, and reduce the risk of reinfection during the recovery process.
First, I will advise you to seek a backup of the encrypted files. Emails, conversations in messengers or on social media, different websites you upload files to – they can contain your precious data in untouched form. This may not be a lot, but having some files recovered is better than nothing at all. Also, getting hold of files in pre-encrypted form may be helpful in other steps.
Another option to try is running large files (over 1GB) “as is”, without any decryption. Just remove the ransomware extension and give it a try, in a way you normally would. This works because ransomware often skips the encryption of large files, as this will take a lot of time and system resources to complete, which consequently leads to more user attention and potential triggering of security systems.