About Tcbu
Tcbu is assorted by our antivirus team as the DJVU virus genus. Another variants of this family here: About STOP/Djvu Ransomware. There are certain scanners that ignore it as well as therefore allowing its irruption. Actually, we have to term it that way, because of the “.tcbu” extension that it appends at the end of your files.
Let’s clarify. Tcbu malware assaults your PC through stealth and sleight also. After that, once intruded it applies AES or RSA encryption logics to hold your files.
Tcbu encrypted your files, but that might not be the only damage done to you. The viruses might still be in your computer. To remove them, we suggest downloading GridinSoft Anti-Malware.
Download GridinSoft Anti-Malware
GridinSoft Anti-Malware Review, How to get free trial?, EULA, and Privacy Policy.
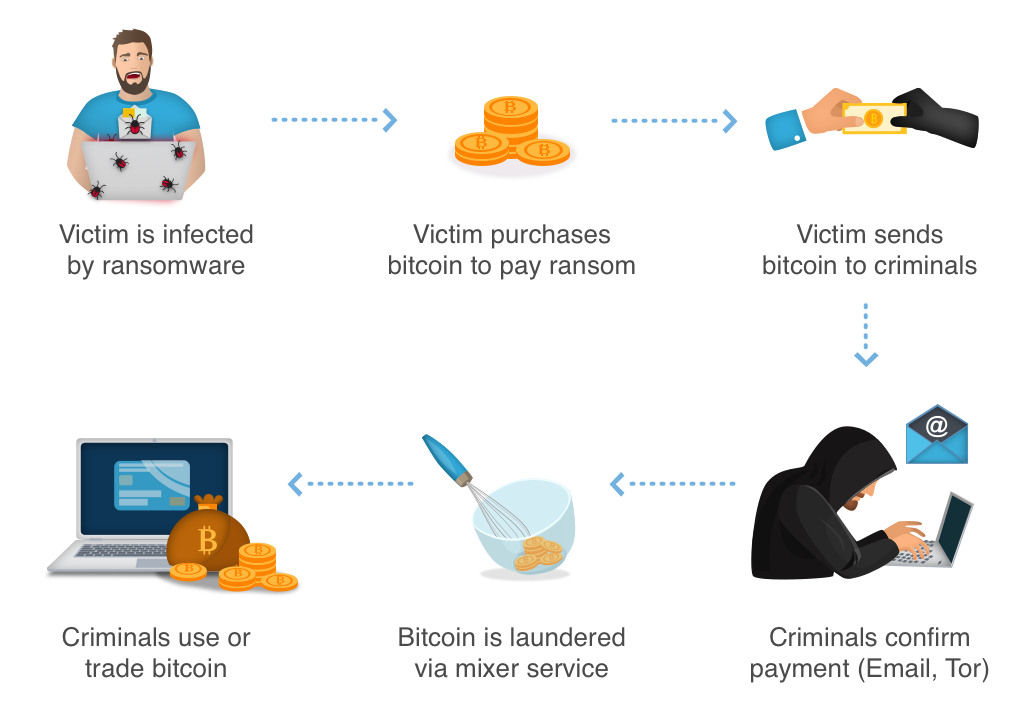
After that, they extort you for their unblocke. After Tcbu slips right into your computer, it places every one of your files under closure. It appends its very own extension “.tcbu” at the end, thus making documents isolated.
Files with “.tcbu” extension appended by the Tcbu virus:
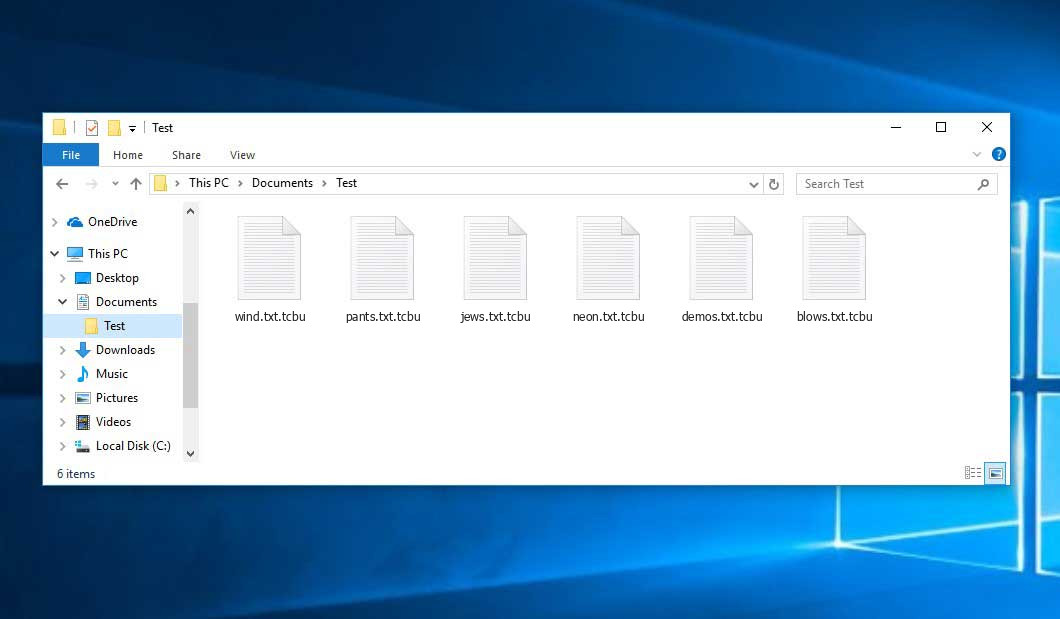
It reaches documents, registers, photos, songs, videos, all of it! Thereafter, you can’t longer view them. Relocating records or renaming it will not facilitate. Sole remedy to release your documents from the ransomware’s keep is decryption. The malware intended you to send blackmail currency if you wish to get your data back. It makes that clear (in the blackmail text) it will decrypt data after defrayal.
The note is usually a text file, left on your desktop. You can also reveal it in each folder that includes encoded documents. It describes your troubles and also proposes you an answer. According to Tcbu, exclusive remedy to decode your documents is with out-and-outer decoding code. And also, to obtain it you have to disburse a buyout. The sum is $980, as well as it’s generally asked for in cryptocurrency.
The note by the Tcbu virus states the following info:
ATTENTION! Don't worry, you can return all your files! All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-WbgTMF1Jmw Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that's price for you is $490. Please note that you'll never restore your data without payment. Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours. To get this software you need write on our e-mail: restorealldata@firemail.cc Reserve e-mail address to contact us: gorentos@bitmessage.ch Our Telegram account: @datarestore Your personal ID: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Do NOT send money for decrypt of “tcbu” files!
The Tcbu ransomware guarantees, to send you the code after you give. As well as, that’s it. That’s all you obtain – a promise. You have no assurances that conformity results in something suitable. Do not rely on words of cyber criminals. That is people, that will double-cross you. Do NOT disburse them a cent. Don’t call them Do NOT comply with their needs.
How did my PC got harmed by Tcbu?
Your computers get corrupted with the Tcbu malware because of your failure to be on the guard. Some people do not pay attention to important details while browsing the web or downloading different softwares.
The Tcbu virus uses the old yet gold annexationist methods to deceive you. And rushes in unobserved. That involves masking behind damaged web links, sites, and torrents. It applies free software as a way to hide itself. And shapes as a phony system or program update. Like, Adobe Flash Player or Java.
Yet more often yes than not, it makesuse of junk emails. You open an email that seems to find from a well-known business. Like, Amazon or PayPal. And, the email prompts you to visit a web link, or download and install an tool. If you do, you end up with ransomware.
Keep in mind that these types of risks are cheating your inadvertence. They need you to rush and miss doing due diligence. That eases their hidden infiltration. They rest on you to leave your fate to chance. Do not! Do not take recklessness over care. One keeps infections out. The other welcomes them in.
Consequently, do not pay them a loan. Don’t connect to the internet criminals. If you do, you’ll regret it. It’s a futile try to restore your records, as well as it will not finish well for you. Below’s why.
There are a few occasions that can unravel when you see the redemption currency message on your display. Claim, you make a decision to comply. You reply to the bleeders, pay their ransom money, and wait. You wait on them to send you the decoding trick they promised. Well, what happens if they do not?
Nevertheless, you have no guarantees. All, you rely on, is a promise. Can you absolutely think promises of virtual thieves? The answer is ‘No.’ These are individuals, who will naturally disenchant you. Don’t send cash! There’s also another way.
They can send you a deciphering key. However, when you try to execute it, it fails to work.
Yes, they can send you the incorrect code. After that, you have much less funds, as well as your files continues to be blocked. Don’t disburse! And also your best-case case isn’t a reason for enjoyment. What takes place after you send the blackmail currency, obtain the appropriate trick, as well as totally free your files? Well? Consider it. You paid money to eliminate a sign and symptom, yet not the infection launching it.
So, you eliminate the encryption, yet the Tcbu ransomware stays. It’s still creeping in the corners of your system, complimentary to strike once again. After that, you’re back at a new start.
Why is Tcbu unsafe?
Futhermore, to encipher a victim’s data, the Tcbu ransomware has also started to install the Azorult Spyware on PC to steal account passwords, cryptocurrency wallets, desktop records, and more.
So, your computer got attacked by Tcbu and also probably you have actually lost time trying to fix it manually. We are absolutely positive that the remedy below will certainly be successful in removing Tcbu in an automated manner.
How to protect PC from Tcbu ransomware?
However, let us initially speak about debarment of such cryptoware attacks in the future. There is something exists that you can do to escape this kind of nasty menace from entering into your device beforehand?
There are a couple of things we wish to talk about here. First one is your private responsibility for being unbelievably attentive while you utilize your device and largely while you browse the web. When examining your e-mail and see some doubtful attachments consisted of, do not rush to open them.
Similarly, when you get on Facebook and social networks also someone you are in touch with sends you messages containing accessories, be very careful, especially if these are some exe-extension files.
Another thing to take into account is examining the dependability of your current security tool. Unfortunately, there are multiple safety and security applications nowadays that just announce to be dependable, whereas in times of real virus incursions they simply stop working to do the task as announced.
In case Tcbu intruded into your PC this specifies that your current anti-malware program did not do its declared assignment as well as really fell short to protect your system. So obviously it is a factor for you to overrate your choices and also definitely switch over to some other software that can most exactly provide the wanted grade of safety.
Not all antiviruses are good
We can additionally discuss some part of users that like not to have any kind of protection software program at all. Definitely, this is a huge error from their side, due to the fact that presently the net has plenty of cyber jeopardies that may secretly invade susceptible systems, particularly those that are not equipped with some standard level of safety.
So, having antivirus incessantly running and guiding your PC is a necessary point in nowadays’ cyber world.
Tcbu is getting on the nerves of many people, so you’re not its only victim.
People ask how to repair the problem effectively. Getting rid of the infection manually may be a long-lasting undertaking and can damage other important system files. Scan your PC with GridinSoft Anti-Malware to detect and delete Tcbu in the right way.

15 Reasons to Choose GridinSoft, How to get free trial?, EULA, and Privacy Policy.
Tcbu removal guide
STEP 1. Recover files from Tcbu ransomware encryption
You can download free decryption tool here: Decryptor for STOP Djvu. But it work when the Tcbu virus used an offline key for encryption.
If key does not found, we advice to restore your PC
There are a lot of different ransomware viruses on the internet. Some of them are more dangerous than the others because they not only leaving malicious processes to protect themselves, but also removing backups of your system to make the recovery process impossible.
Please Note: Not all ransomware infections are able to remove backups of your system, so it is always worth to try a windows recovery.
We recommend use Safe Mode with command prompt to safely perform a recovery of your files. You will have to reboot your computer, so you better save this instruction:
How to Restore Files from a Backup in Windows 7/8/10
STEP 2. Removing Tcbu ransomware malicious files
Once the recovery process is complete, you should consider scanning your computer with a GridinSoft Anti-Malware in order to find any traces of Tcbu infection. Though some ransomware viruses are removing themselves right after the encryption of your files, some may leave malicious processes on your computer for special purposes of cyber criminals.
-
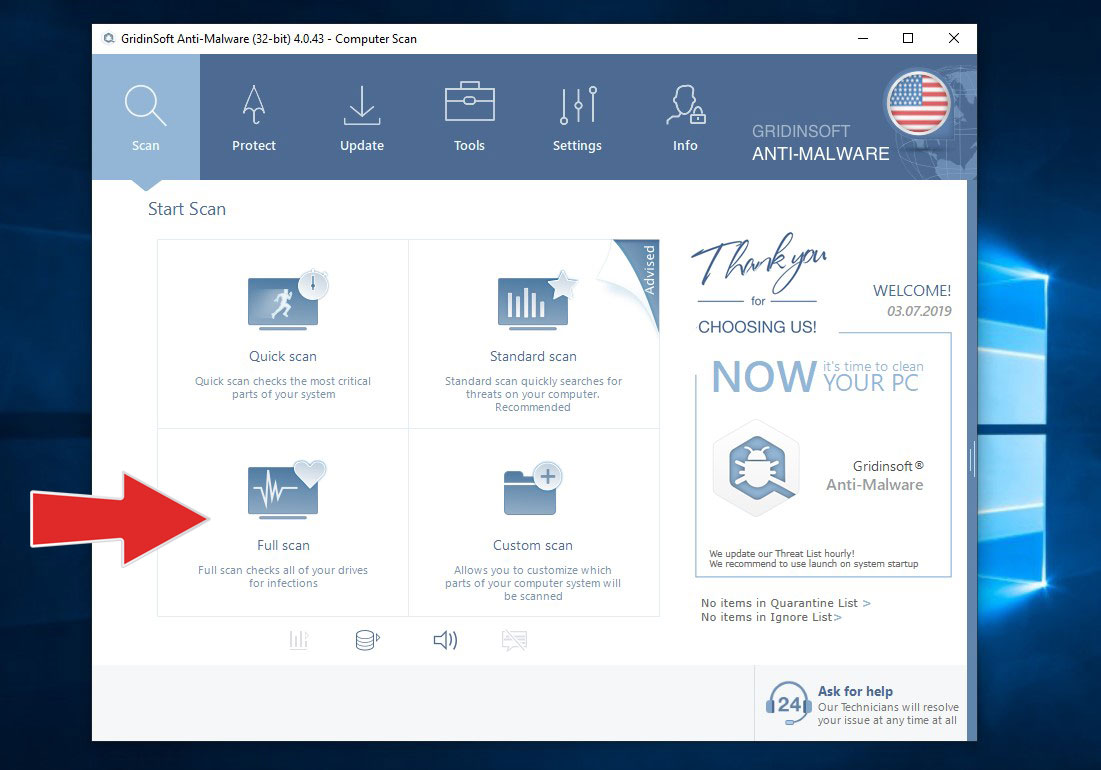
Run GridinSoft Anti-Malware and choose the scan type, which is suitable for your needs. Of course, for the accuratest scan results we recommend you to choose the “Full Scan”.
-
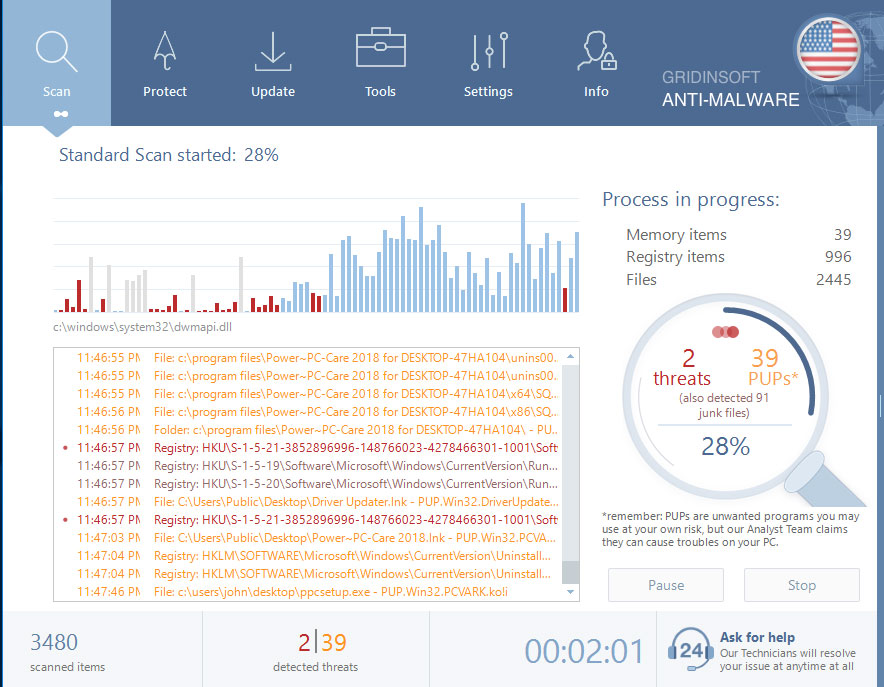
Give Anti-Malware a little time to check your system:
-
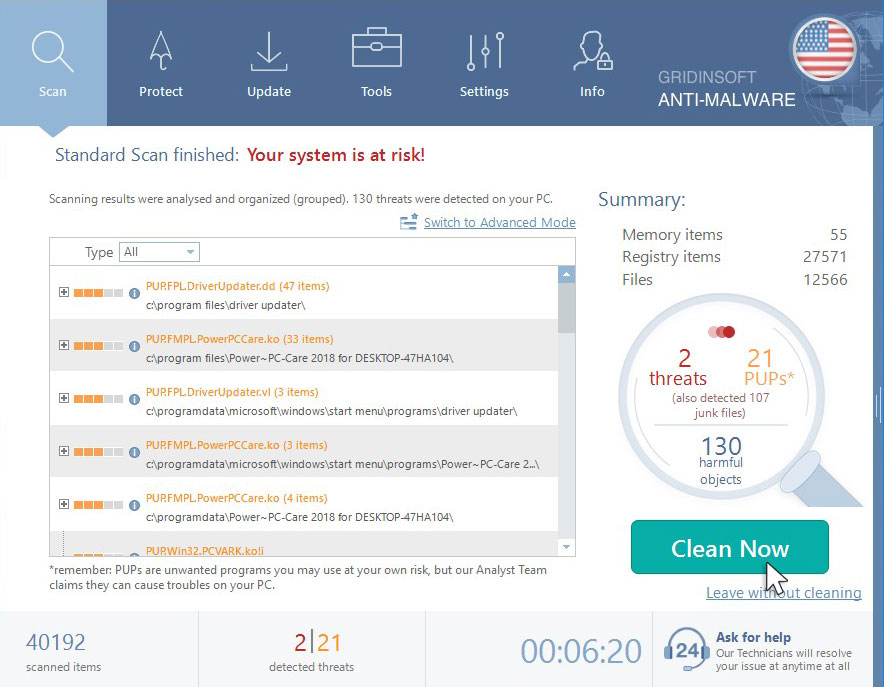
Move to quarantine all the viruses and unwanted files, that you see in the results list:
-
Enjoy the malware removal process:
-
Use of On-run protection may additionaly prevent different types of cyber attacks, our protect may flag the downloader of the ransomware as a malicious application preventing the download of Tcbu.
STEP 3. Prevent the Tcbu virus infection
Besides the protection tool, you should read and learn few simple rules. Follow them every time you work on your computer and your will decrease chances of your infection to a minimum:
- Don’t open suspicious spam letters. No way! Be very careful with your downloads. Download and install software preferably from its official website.
- Do backups of your important files regularly. Storing your really important files in few different places is a good decision.
- Keep your system free from adware, hijackers and PUPs The infected computer will be more likely compromised with other malicious software, and ransomware is not an exception in this case.
- Don’t panic and be reasonable. Don’t pay the ransom fee right after you got infected, it is always best to search on the internet for some answers. It is possible that someone have developed a decryption tool that might help you.