
주요 메시징 앱의 사용자가 합법적으로 보이는 링크로 가장한 잠재적인 피싱 공격의 위험에 처할 수 있음이 알려졌습니다.. Facebook 메신저를 포함한 여러 주요 메시징 및 이메일 플랫폼, 신호, WhatsApp에, Instagram과 iMessage는 이제 사용자에게 URL 변경 트릭을 통해 피싱될 가능성을 제시합니다..
트릭은 어디에 숨겨져 있습니까??
사이버 보안 전문가는 취약점이 지난 3년 동안 잠재적으로 악용되었으며 언급된 일부 앱에 여전히 존재한다고 확인했습니다..
삽입된 RTLO가 있는 URL을 잘못 표시하는 앱 인터페이스의 결과 (오른쪽에서 왼쪽으로 재정의) 사용자를 잠재적인 URI 스푸핑 공격에 취약하게 만드는 유니코드 제어 문자.
히브리어 또는 아랍어 메시지를 표시하는 데 주로 사용됩니다. 문자열에 RTLO 문자를 삽입하면 메시징 앱이나 브라우저에서 정상적인 왼쪽에서 오른쪽 방향이 아닌 오른쪽에서 왼쪽으로 표시됩니다..
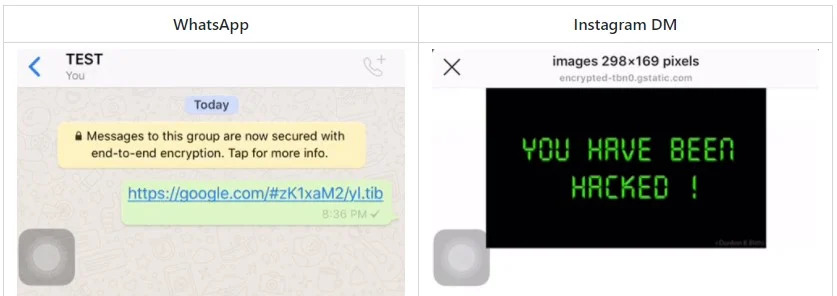
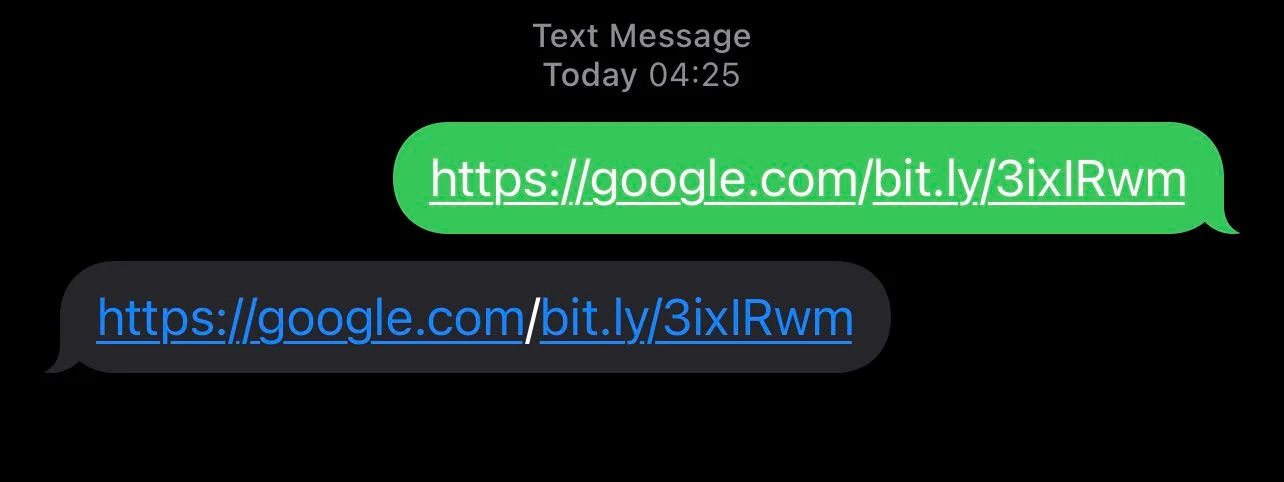
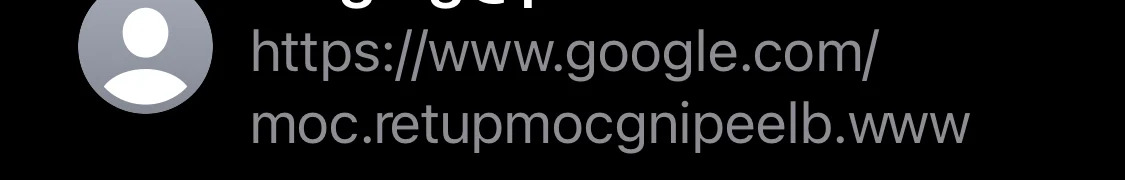
익스플로잇, 하나의 라이너, gTLD의 Android 및 iOS 신뢰와 양방향 텍스트 표시 지원을 남용합니다.. 따라서 교장은 하나의 제어 문자 'u202E'를 삽입하기만 하면 되는 복사 및 붙여넣기만큼 간단합니다.’ 두 URL 사이.
RTLO 제어 문자를 삽입한 후에는 이제 텍스트가 다음과 같이 처리되기 때문에 URL이 반전됩니다. “오른쪽에서 왼쪽으로” 언어 (아라비아 말, 헤브라이 사람, 기타)
그래서, 예를 들면, 위협 행위자가 만들 수 있는”'gepj.xyz” link하지만 우리의 트릭으로 그것은 순진해 보입니다. “zyx.jpeg”, 위협 행위자는 다양한 유형의 악의적인 행동을 수행할 수 있습니다. “kpa.li” 될 것이다 “li.apk” 합법적인 APK 파일인 척. 이러한 경우 링크는 사용자를 대상이 될 수 있는 모든 대상으로 안내할 수 있습니다..
첫눈에, 이러한 피싱 URL은 google.com의 합법적인 하위 도메인처럼 보입니다.. 또는 apple.com.
연구원들이 취약점에 대해 말하는 것?
취약점은 다음 버전의 IM 앱에서 할당된 CVE를 받았습니다.:
- CVE-2020-20096 – 왓츠앱 2.19.80 또는 iOS의 경우 이전 및 2.19.222 또는 Android에서 이전;
- CVE-2020-20095 – 아이메시지 14.3 iOS의 경우 이전 버전;
- CVE-2020-20094 - 인스 타 그램 106.0 또는 iOS의 경우 이전 및 107.0.0.11 또는 Android에서 이전;
- CVE-2020-20093 – 페이스북 메신저 227.0 또는 iOS의 경우 이전 및 228.1.0.10.116 또는 Android에서 이전.
회사가 얼마 전에 통보를 받았기 때문에 Signal에는 할당된 CVE ID가 없습니다..
“모든 것에서 링크 미리보기 끄기, 특히 메일 앱 및 알림과 관련된 모든 것. 팝업이 있는 이상한 웹사이트를 방문하지 마세요.. 무작위 경품을 클릭하지 마십시오,” Sick.Code의 연구원 수정 사항이 아직 적용되지 않은 언급된 앱의 사용자에게 조언
그래서, 사이버 보안 커뮤니티에서 이러한 취약점의 미묘한 차이를 놓친 이유는 무엇입니까?? 그 이유는 뉘앙스이기 때문에 더 복잡하고 위험한 취약점에서 놓쳤기 때문일 수 있습니다.. 누가 알아?
8 월 2019 이름의 연구원 “자듀그” 취약점의 초기 발견. 나중에 Sick.Code의 프리랜서 보안 연구원이 취약점이 Twitter의 CVE 프로그램에 게시되었을 때 취약점에 관심을 돌렸습니다..
Sick.Codes 연구원이 연락했습니다. “자듀그” 저장소를 공개했는지 여부를 묻기 위해. 연구원은 CVE가 이제서야 공개되었다는 놀라움으로 응답했으며 취약점 악용 방법에 대해 더 많은 정보를 공유할 의사를 표시하지 않았습니다..
그러나 두 명의 연구원이 PoC 공유에 동의했습니다. ( 개념의 증거) GitHub에서. one-liner PoC는 공개적으로 사용 가능하며 기술 지식이 거의 없는 사람도 테스트를 시도할 수 있습니다..
관심 있는 분들을 위해, 다른 RTLO 기반의 전체 무리가 있습니다. 착취 훨씬 더 복잡한 기술 개념을 포함하는 기술.
영향을 받는 앱 사용자의 경우, 연구자들은 URL이 포함된 메시지를 수신할 때 각별히 주의할 것을 권고합니다., 수신된 URL의 왼쪽을 항상 클릭하고 문제를 해결해야 하는 예정된 업데이트를 주시하십시오..
사이버 보안 전문가들은 이러한 피싱 유형이 공격 다른 많은 IM 및 이메일 앱에 영향을 미칠 수 있지만 다시 한 번 — 기사에 언급된 앱에만 문제가 있는 것으로 확인되었습니다..
Telegram에도 이러한 종류의 취약점이 있는 것으로 보고되었지만 해당 개발자가 이 문제를 가장 먼저 해결했습니다..
언급해야 할 한 가지 흥미로운 점은 RTLO 유니코드 문자가 합법적으로 사용되기 때문에 개발자가 문제를 정확히 해결하는 방법입니다. 수정 사항은 잠재적으로 합법적인 기능을 망칠 수 있기 때문입니다..
피싱 문제에 대한 추가 설명?
그리고 여기에 피싱에 관한 약간의 지식 기반이 표시됩니다.. 모든 사람이 피싱이 무엇인지 알고 있거나 일반적으로 이해하고 있습니다..
위키피디아에 따르면, 피싱 공격자가 민감한 정보나 기밀 정보를 공격자에게 공개하도록 속이려는 의도로 사기성 기만 메시지를 보내는 일종의 사회 공학 공격입니다.. 때로는 피해자의 컴퓨터에 악성 소프트웨어를 배포하기 위해 수행됩니다..
같은 사이트의 기사에는 다음과 같이 나와 있습니다. 2020 피싱은 가장 흔한 사이버 공격 유형으로 다른 유형의 사이버 범죄보다 2배 이상 발생했습니다..
피싱은 서로 다르지만 목적이 같은 유형으로 분류됩니다.: 보이스피싱, 소셜 미디어 피싱, 대단히, 비즈니스 이메일 손상 (BEC), 마이크로 소프트 365 피싱 및 스피어 피싱.
언급된 유형 중 일부를 설명하려면. 포경은 공격자를 의미합니다.’ 목표로 삼는 의도 “월척”, 일반적으로 어떤 회사의 CEO는 이 사람을 통해 이 특정 대상이 일반적으로 액세스할 수 있는 매우 민감한 정보를 얻습니다..
그리고 스피어피싱이란 공격자가 무작위로 공격하는 것이 아니라 특정인을 표적으로 삼는 것을 의미합니다.. 이러한 유형의 피싱에서 사이버 범죄자는 종종 미래의 피해자에 대해 약간의 조사를 하기 때문에 보다 신뢰할 수 있는 피싱 메시지를 생성할 수 있습니다.. SANS 연구소에 따르면, 95 기업 네트워크에 대한 모든 공격의 퍼센트는 스피어 피싱에서 비롯됩니다..
피싱을 피하는 방법에 대한 팁에 대해 이야기하기, 긴 목록을 자세하게 작성하거나 생략할 수 있지만, 개인적으로 가장 좋은 규칙은, 모든 사기꾼 또는 관련자와 마찬가지로, 항상 상식에 귀를 기울일 것입니다.
그 이메일이 정말로 당신을 위한 것인지, 아니면 당신의 은행에서 그러한 유형의 메시지를 예를 들어 수신할 수 있을지 생각해 보십시오.? 주의하세요, 첫 번째 클릭으로 메시지를 받은 후 즉시 이동하지 마십시오..
