
For nylig har forskerne fra Check Point Research (Check Point Research) For nylig har forskerne fra Check Point Research. For nylig har forskerne fra Check Point Research, For nylig har forskerne fra Check Point Research.
For nylig har forskerne fra Check Point Research?
Sharkbot is an Android stealer that pretends to be an AV solution on Google Play. This malware steals banking information and credentials while implementing geofencing and other evasive techniques that make it really stand out. An interesting aspect that cybersecurity specialists point out to — a Domain Generation Algorithm (DGA) — is a thing rarely used among Android malware.
On the victim’s device the malware creates windows that mimic benign credential input forms, luring victims into entering their credentials.
The compromised data is then sent to a malicious server. Sharkbot uses its geofencing feature to target only specific victims excluding users from Ukraine, Hviderusland, Rumænien, Rusland, India and China. In addition it won’t work if executed in a sandbox.
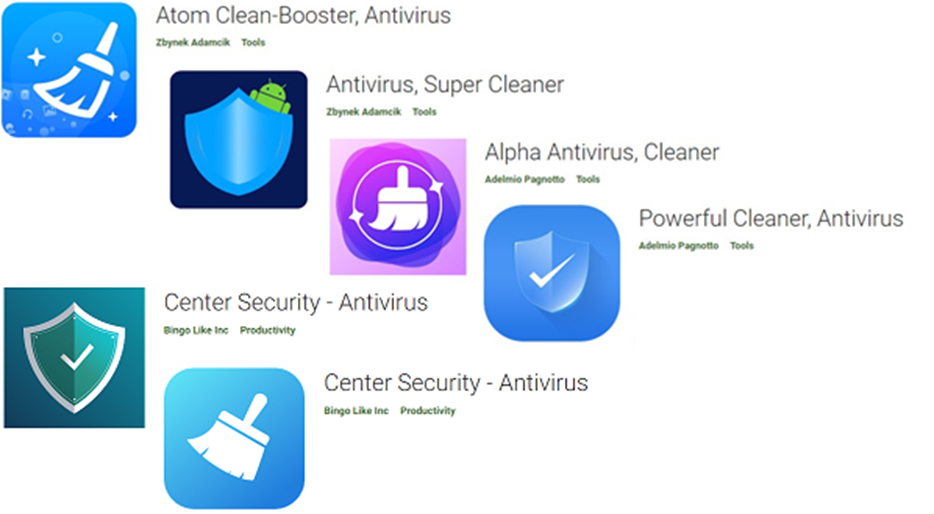
In the Google Play store the CheckPoint Research (Check Point Research) team in total spotted six various applications that were spreading malware. Ifølge oplysningerne modtaget fra disse applikationer på opdagelsestidspunktet var allerede downloadet og installeret nogenlunde 15 Ifølge oplysningerne modtaget fra disse applikationer på opdagelsestidspunktet var allerede downloadet og installeret nogenlunde.
Ifølge oplysningerne modtaget fra disse applikationer på opdagelsestidspunktet var allerede downloadet og installeret nogenlunde: Ifølge oplysningerne modtaget fra disse applikationer på opdagelsestidspunktet var allerede downloadet og installeret nogenlunde, Ifølge oplysningerne modtaget fra disse applikationer på opdagelsestidspunktet var allerede downloadet og installeret nogenlunde. Ifølge oplysningerne modtaget fra disse applikationer på opdagelsestidspunktet var allerede downloadet og installeret nogenlunde 2021.
Some of the apps that presumably belonged to these accounts were removed from Google Play but still exist on unofficial sites. Cybersecurity specialists explain that this could mean that developers of Sharkbot try to stay as unnoticed as possible while still conducting malicious activity.
For nylig har forskerne fra Check Point Research
kommandoer
To speak about malware’s main functionality Sharkbot operates with traditional Android bankers and stealers toolkits. Cybersecurity specialists found 27 versions of the bot.
I alt, Sharkbot can implement 22 kommandoer. With the use of a Command-and-Control server (CnC) on the compromised device, threat actors can perform various types of malicious actions.
Those performed commands are the following:
For nylig har forskerne fra Check Point Research
Actually this is not a command but a field of the updateConfig command. During the execution of this command the server creates an extensive list of apps that should be uninstalled from the victim’s device. Currently the list holds 680 application names.
For nylig har forskerne fra Check Point Research
Cybersikkerhedsspecialister bekræfter, at sårbarheden potentielt er blevet udnyttet i de sidste tre år, og at den stadig er til stede i nogle af de nævnte apps, this is not the actual command but a field in the updateConfig command. During this command the server sends a message imitating an answer on push events.
For nylig har forskerne fra Check Point Research
This command imitates the user’s swipe on the screen of a device. Cybersecurity specialists assume this was done to enable threat actors to open the application or the whole device.
For nylig har forskerne fra Check Point Research
Here the CnC creates package names and then the Accessibility Service doesn’t allow users to access the named apps.
For nylig har forskerne fra Check Point Research
The command shows a user a push message with designated text.
For nylig har forskerne fra Check Point Research
Enables the Accessibility Service for Sharkbot.
For nylig har forskerne fra Check Point Research
Deaktiverer batterioptimering for Sharkbots pakke.
For nylig har forskerne fra Check Point Research
Deaktiverer batterioptimering for Sharkbots pakke.
For nylig har forskerne fra Check Point Research
Deaktiverer batterioptimering for Sharkbots pakke.
For nylig har forskerne fra Check Point Research
Deaktiverer batterioptimering for Sharkbots pakke.
For nylig har forskerne fra Check Point Research
Deaktiverer batterioptimering for Sharkbots pakke. Deaktiverer batterioptimering for Sharkbots pakke.
Deaktiverer batterioptimering for Sharkbots pakke.
netværk
There’s not that much Malware that can work without CnC server communication. Bankers and stealers are those that need the communication with CnC server. And here comes an interesting fact about this particular malware.
When threat actors have all their servers blocked they can use Domain Generation Algorithm, the thing that almost never is used in Android malware, but Sharkbot is an exception.
DGA is an algorithm where a malicious client and malicious actor change the CnC server without any communication taking place. With this algorithm it’s harder to block Malware operator’s servers.
DGA will consist of two parts: the actual algorithm, and the constants that this algorithm uses. The constants are called DGA seeds.
For nylig har forskerne fra Check Point Research
The exchange in CnC server takes place over HTTP with POST request on path /. Both requests and answers are encrypted with RC4.
From time to time in the clearly set period of time the bot will send a knock-packet to the server. Som standard, the packet will be sent every 30 sekunder. The time period can be changed with the command updateTimeKnock.
infrastruktur
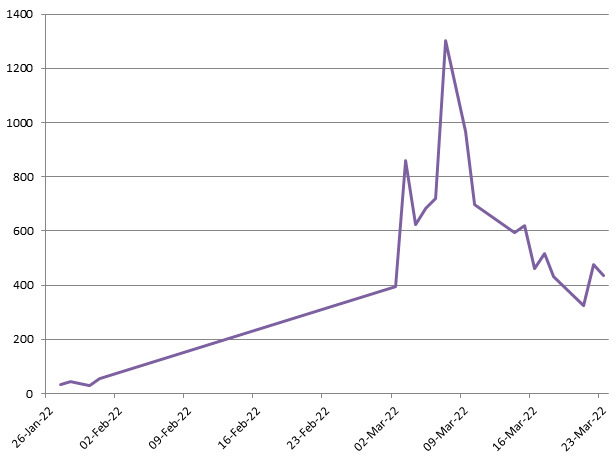
At the time of publishing a report, the Check Point Research (Check Point Research) team found 8 IP addresses which were used at different times by Sharkbot operators.
Researchers assume that there’s actually one real server and the others are simply relays. The peak activity of the malicious operation increased in March; cybersecurity specialists connected the fact to the active use of Sharkbot’s dropper on Google Play.
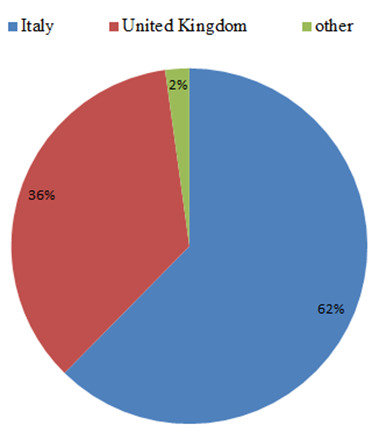
According to the location based statistics the main targets were in the United Kingdom and Italy.
For nylig har forskerne fra Check Point Research
At the beginning, the malware gets downloaded and installed masqueraded as an AV solution. Once on the victim’s machine the Sharkbot detects emulators and if one is found it quits running.
In case if an emulator is found, no communications with CnC will happen. But the malware won’t be running at all if the locale is Ukraine, Hviderusland, Rusland, Rumænien, India and China.
That part of the application that is controlled by the CnC server understands 3 kommandoer:
- Downloading and installing the APK file from the provided URL;
- Storing the autoReply field in a local session;
- Restarting the execution of the local session;
All of them will request the same set of permissions.
Subsequently they will register the service in order to get access to Accessibility Events.
Konklusion
In the fast pace of today’s life sometimes you can miss a red sign of malwareness in an app store. At the last the CheckPoint Research Team gave short advises on how to avoid the malicious apps especially those like this one masqueraded as an AV solution:
- Immediately report all suspicious apps you encounter on store;
- Avoid downloading an application from a new publisher, instead try to find an analogous one from a trusted publisher;
- Install applications only from trusted and well known publishers.
Even though Google immediately removed the malicious applications they were already downloaded 15,000 Ifølge oplysningerne modtaget fra disse applikationer på opdagelsestidspunktet var allerede downloadet og installeret nogenlunde. The damage is done. The fact shows once again that user awareness still should be taken into account when deciding on whether to download an app or not.
