Researchers taught Rowhammer to steal data


A team of researchers from the United States, Australia and Austria developed a new version of Rowhammer attack.
Unlike previous versions, a new attack called RAMBleed allows not only modifing data and increase privileges, but also steal data stored on the device.Rowhammer is an exploit class for hardware vulnerability (CVE-2019-0174) in modern memory cards. By default, data in memory cards is stored in cells located on a silicon chip in rows forming a grid.
In 2014, scientists found that multiple readings of data stored in the same row result in an electrical charge that can affect data in adjacent rows. The attack was called Rowhammer, and with its help, scientists could either damage data or use it for malicious purposes.

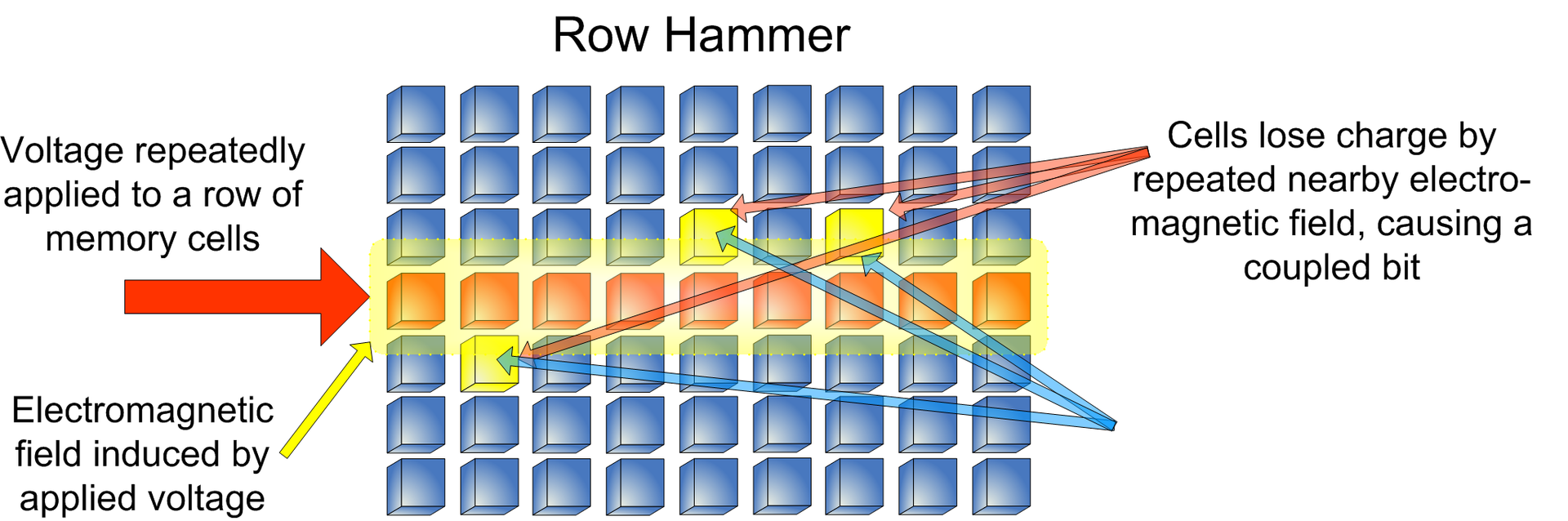
Since 2014, researchers significantly expanded capabilities of the original attack, however, it was only now possible to remove data from the memory and steal it.
“It is widely assumed however, that bit flips within the adversary’s own private memory have no security implications, as the attacker can already modify its private memory via regular write operations. We demonstrate that this assumption is incorrect by employing Rowhammer as areadside channel. More specifically, we show how an unprivileged attacker can exploit the data dependence between Rowhammer induced bit flips and the bitsin nearby rows to deduce these bits, including values belonging to other processes and the kernel”, — report researchers.
In order to make RAMBleed attack possible, scientists managed to force Linux memory allocator (buddy allocator) to enable a large block of consecutive physical addresses that allowed them to orchestrate the attack.
Researchers created a new mechanism, “Frame Feng Shui“, to place victim’s program pages in the right place in physical memory. In addition, they developed a new method of managing data in memory and repeating their reading (so-called row hammering) to determine which data is in neighboring memory cells.
“Thus, primary contribution of this work is to show that Rowhammer is a threat to not only integrity, but also to confidentiality”, — say scientists.
Source: https://rambleed.com/docs/
Recent Posts
Remove Hotbkowobe.today Pop-up Ads
About Hotbkowobe.today Hotbkowobe.today pop-ups can not open out of the blue. If you have actually…
Remove Hotbmizifo.today Pop-up Ads
About Hotbmizifo.today Hotbmizifo.today pop-ups can not open out of nowhere. If you have actually clicked…
Remove Hotbvukavi.today Pop-up Ads
About Hotbvukavi.today Hotbvukavi.today pop-ups can not expose out of nowhere. If you have actually clicked…
Remove Schutzmeldung.de Pop-up Ads
About Schutzmeldung.de Schutzmeldung.de pop-ups can not introduce out of the blue. If you have actually…
Remove Hotbharoki.com Pop-up Ads
About Hotbharoki.com Hotbharoki.com pop-ups can not introduce out of nowhere. If you have clicked on…
Remove Safeguardcomp.site Pop-up Ads
About Safeguardcomp.site Safeguardcomp.site pop-ups can not launch out of the blue. If you have clicked…


