Repentant cybercriminal leaked tools of Iranian hackers in Telegram


In the middle of March 2019 hacker that is known as Lab Dookhtengan published in Telegram tools of Iranian APT34 group (aka Oilrig and HelixKitten) as well as information about hackers and their alleged supervisors from Ministry of Information and National Security of Iran.
Journalists of ZDNet communicated with Lab Dookhtegan and report that he confirms participation in DNSpionage campaign and was a member of APT34. However, he does not provide any evidence and can be by far not Iranian intelligence serviceman.ZDNet argues that many Internet-security companies are investigating Lab Dookhtegan involvement. Authenticity of provided by him codes have already confirmed specialists from Chronicle that is cybersecurity department of Alphabet Holding.

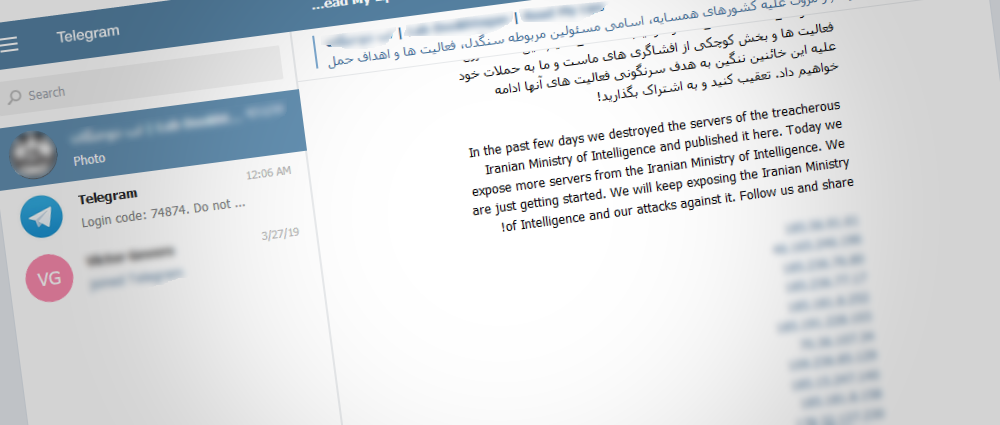
Information from Lab Dookhtegan in the telegram
Aside from initial codes, Lab Dookhtegan also published in open access information about 66 APT34 victims that was stored on group’s governing server. Among other published data were also credentials for internal servers and users’ IP-addresses. Majorly this list includes companies and organizations from Middle East, Africa, South-East Asia and Europe. Two biggest companies that suffered from attacks are Etihad Airways and Emirates National Oil.
Lab Dookhtegan also leaked data about groups previous activity, including lists of IP-addresses and domains where group hosted web sells and other operational data.
In addition, anonymous exposer spent much time on doxing of Iranian Ministry of Information and National Security employees that participated in APT34 operations. For some officers Lab Dookhtegan created special PDF-folders with “dossiers” where he discloses their names, positions, attached pictures, phone numbers, emails and links of their social media profiles. Journalists argue that it is difficult not to note Lab Dookhtegan’s negative stance towards these people as in this dossiers he calls them “merciless criminals”.
Lab Dookhtegan list
In addition to abovementioned, in Telegram were published screenshots that demonstrate demolishing of APT34 control panels and full cleaning of group’s servers that allegedly was committed by Lab Dookhtegan.
Chronicle analysts suggest that now APT34 will have to change their instruments and it will take time to restore combat readiness.
Source: www.zdnet.com
Recent Posts
Remove Curestin.co.in Pop-up Ads
About Curestin.co.in Curestin.co.in pop-ups can not introduce out of nowhere. If you have actually clicked…
Remove Asyetaprovinc.org Pop-up Ads
About Asyetaprovinc.org Asyetaprovinc.org pop-ups can not expose out of the blue. If you have actually…
Remove Hotbxokihi.cc Pop-up Ads
About Hotbxokihi.cc Hotbxokihi.cc pop-ups can not expose out of nowhere. If you have clicked some…
Remove Hotbyavaye.today Pop-up Ads
About Hotbyavaye.today Hotbyavaye.today pop-ups can not open out of nowhere. If you have actually clicked…
Remove Easydefender.site Pop-up Ads
About Easydefender.site Easydefender.site pop-ups can not expose out of nowhere. If you have clicked on…
Remove Hotbmurumi.cc Pop-up Ads
About Hotbmurumi.cc Hotbmurumi.cc pop-ups can not open out of the blue. If you have actually…


