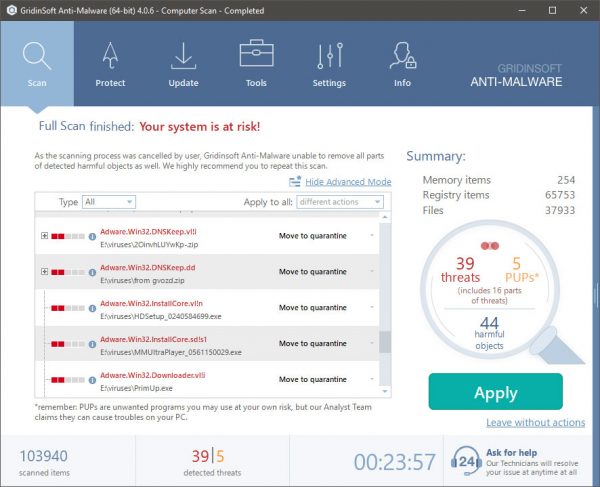
En ny, svært skadelig kryptokurver-gruveinfeksjon har blitt oppdaget av sikkerhets- og sikkerhetsforskere. den malware, kalt SystemNTN.exe kan smitte målrammede ved hjelp av en rekke metoder. The main point behind the SystemNTN.exe miner is to use cryptocurrency miner tasks on the computers of sufferers in order to get Monero tokens at targets expenditure. The end result of this miner is the raised electrical energy expenses as well as if you leave it for longer time periods SystemNTN.exe may even damage your computers elements.
SystemNTN.exe: distribusjonsmetoder
De SystemNTN.exe malware benytter 2 foretrukne metoder som brukes til å infisere datamaskinmål:
- Nyttelast Levering ved hjelp av tidligere infeksjoner. If an older SystemNTN.exe malware is released on the sufferer systems it can instantly upgrade itself or download a more recent version. This is possible using the integrated upgrade command which gets the release. Dette gjøres ved å koble til en spesifikk forhåndsdefinert hacker-kontrollert server som gir skadelig programvare-kode. Det nedlastede viruset vil få navnet på en Windows-løsning og bli plassert i “%Systemet% temp” område. Crucial residential or commercial properties and running system configuration documents are changed in order to allow a persistent as well as silent infection.
- Programvare Utnytter Søknad om sikkerhetsproblemene. The most current variation of the SystemNTN.exe malware have actually been discovered to be caused by the some exploits, mye forstått for å ha blitt benyttet i ransomware-streikene. Infeksjoner er gjort ved å målrette åpne tjenester ved hjelp av TCP-port. Angrepene er automatiserte av hackere styrt struktur som søker ut om porten er åpen. If this condition is fulfilled it will check the solution and also retrieve information regarding it, inkludert all slags variasjon og konfigurasjonsinformasjon. Ventures og fremtredende kombinasjoner av brukernavn og passord kan gjøres. When the manipulate is triggered against the prone code the miner will certainly be released together with the backdoor. Dette vil sikkert gi en dobbel infeksjon.
In addition to these methods various other methods can be used too. Miners can be dispersed by phishing emails that are sent wholesale in a SPAM-like manner and also depend on social design techniques in order to perplex the targets right into believing that they have gotten a message from a reputable service or business. The virus files can be either directly attached or inserted in the body materials in multimedia material or text web links.
The crooks can additionally create malicious touchdown pages that can impersonate supplier download web pages, software application download sites as well as other often accessed locations. When they utilize comparable sounding domain names to reputable addresses and also safety certifications the customers might be coerced right into interacting with them. I noen tilfeller rett og slett å åpne dem kan aktivere miner infeksjon.
An additional technique would certainly be to utilize haul service providers that can be spread making use of those techniques or by means of data sharing networks, BitTorrent er en av de mest populære. It is often utilized to distribute both reputable software application and also data as well as pirate material. To av en av de mest populære tjenesteleverandørene for nyttelast er følgende:
Other methods that can be taken into consideration by the crooks consist of the use of internet browser hijackers -harmful plugins which are made compatible with the most prominent internet browsers. They are published to the appropriate repositories with phony user testimonials and developer qualifications. I de fleste tilfeller beskrivelsene kan inkludere skjermbilder, video clips as well as intricate summaries encouraging fantastic attribute improvements and also efficiency optimizations. However upon setup the behavior of the affected web browsers will certainly change- customers will discover that they will be rerouted to a hacker-controlled touchdown page and their settings might be changed – standard startside, Internett-søkemotor, og også helt nye faner siden.
SystemNTN.exe: Analyse
The SystemNTN.exe malware is a traditional instance of a cryptocurrency miner which depending on its setup can create a wide array of hazardous activities. Its primary goal is to do intricate mathematical jobs that will benefit from the available system sources: prosessor, GPU, minne og også harddisk område. The way they operate is by attaching to an unique web server called mining swimming pool from where the required code is downloaded. Så snart en av oppgavene er lastet ned, vil den bli startet på samme tid, mange tilfeller kan være borte for når. When an offered task is completed an additional one will certainly be downloaded in its place and the loophole will proceed up until the computer is powered off, infeksjonen elimineres eller en mer sammenlignbar anledning skjer. Kryptovaluta vil sikkert bli kompensert for den kriminelle kontrollerne (hacking gruppe eller en enkelt hackere) rett til sine budsjetter.
A hazardous feature of this classification of malware is that examples similar to this one can take all system resources and also practically make the sufferer computer pointless till the danger has been entirely eliminated. A lot of them feature a relentless setup that makes them actually hard to get rid of. Disse kommandoene vil selvfølgelig gjøre endringer i oppstartsalternativer, arrangement documents and also Windows Registry values that will make the SystemNTN.exe malware beginning immediately once the computer system is powered on. Accessibility to recuperation food selections and options might be blocked which provides several manual removal overviews virtually worthless.
Denne infeksjonen vil sette opp en Windows-tjeneste for seg selv, following the performed safety analysis ther adhering to actions have been observed:
. During the miner operations the associated malware can hook up to already running Windows solutions as well as third-party installed applications. By doing so the system administrators might not notice that the source lots comes from a separate process.
| Navn | SystemNTN.exe |
|---|---|
| Kategori | Trojan |
| Underkategori | kryptovaluta Miner |
| farer | Høy CPU-bruk, Internett hastighetsreduksjon, PC krasjer og fryser og etc. |
| Hovedhensikt | For å tjene penger for kriminelle |
| Fordeling | torrents, Gratis spill, Cracked Apps, e-post, tvilsomme nettsteder, Utnytter |
| fjerning | Installere GridinSoft Anti-Malware to detect and remove SystemNTN.exe |
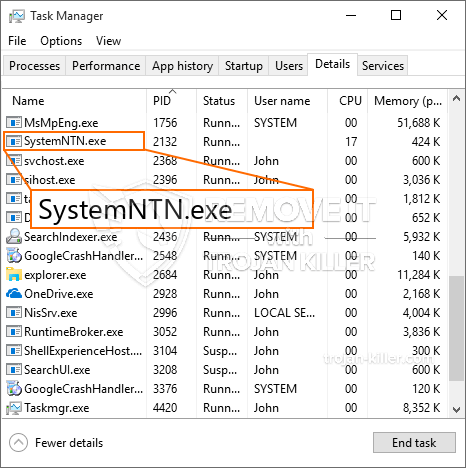
id =”82685″ juster =”aligncenter” width =”600″]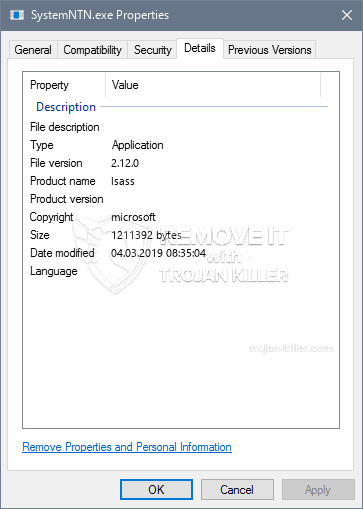 SystemNTN.exe
SystemNTN.exe
These type of malware infections are particularly effective at carrying out innovative commands if set up so. De er basert på et modulært rammeverk som gjør det mulig for de kriminelle kontrollørene å orkestrere alle slags farlige handlinger. Blant de populære forekomster er endring av Windows-registeret – alterations strings connected by the os can cause significant efficiency interruptions and also the inability to accessibility Windows solutions. Relying on the range of changes it can also make the computer system totally unusable. På de ulike derimot manipulering av register worths kommer fra alle typer tredjeparts installerte programmer kan undergrave dem. Some applications may fail to introduce entirely while others can all of a sudden quit working.
This specific miner in its present version is concentrated on mining the Monero cryptocurrency containing a modified version of XMRig CPU mining engine. If the campaigns confirm successful after that future variations of the SystemNTN.exe can be introduced in the future. Siden skadelig programvare bruker programvaremottak for å forurense målverter, det kan være en del av en usikker samtidig infeksjon med ransomware samt trojanere.
Elimination of SystemNTN.exe is highly suggested, because you take the chance of not just a large electrical power expense if it is operating on your COMPUTER, but the miner may likewise carry out other undesirable tasks on it as well as also harm your PC permanently.
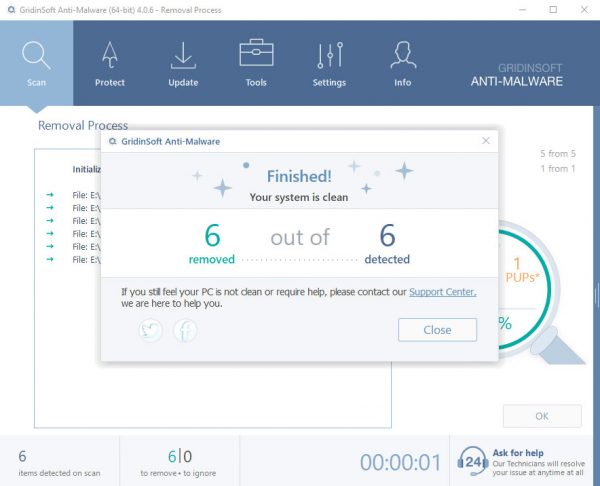
SystemNTN.exe removal process
SKRITT 1. Først av alt, du må laste ned og installere GridinSoft Anti-Malware.
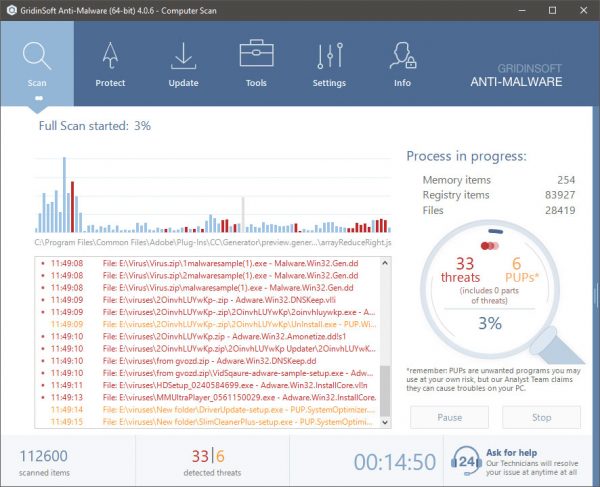
SKRITT 2. Da bør du velge “Rask skanning” eller “Full skanning”.
SKRITT 3. Kjør for å skanne datamaskinen
SKRITT 4. Etter at skanningen er fullført, du må klikke på “Søke om” button to remove SystemNTN.exe
SKRITT 5. SystemNTN.exe Removed!
video guide: How to use GridinSoft Anti-Malware for remove SystemNTN.exe
Hvor å forhindre din PC blir infisert med “SystemNTN.exe” i fremtiden.
En kraftig antivirus løsning som kan oppdage og blokkere fileless malware er hva du trenger! Tradisjonelle løsninger oppdager malware basert på virusdefinisjoner, og dermed er de ofte ikke kan oppdage “SystemNTN.exe”. GridinSoft Anti-Malware gir beskyttelse mot alle typer malware inkludert fileless malware som “SystemNTN.exe”. GridinSoft Anti-Malware gir cloud-baserte atferd analysator for å blokkere alle ukjente filer, inkludert zero-day malware. Slik teknologi kan oppdage og fjerne “SystemNTN.exe”.