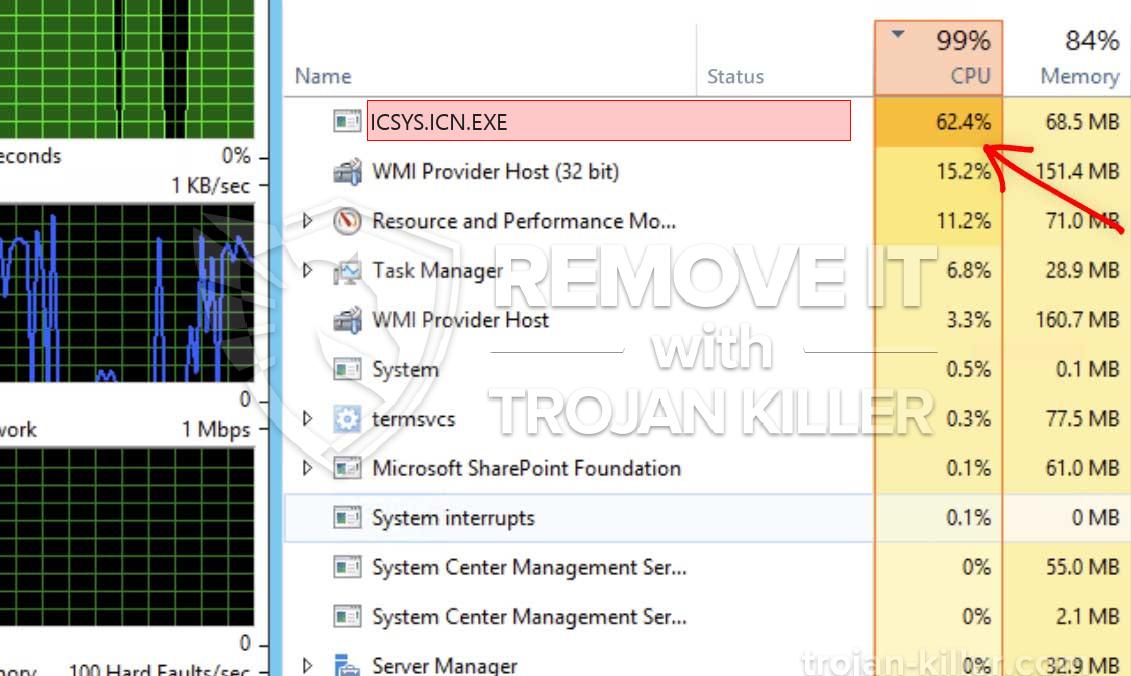
En helt ny, veldig farlig kryptovaluta-gruveinfeksjon er funnet av sikkerhetsforskere. den malware, kalt icsys.icn.exe kan forurense målofre ved hjelp av et utvalg av midler. Hovedpoenget bak ICSYS.ICN.EXE-gruvearbeideren er å bruke gruvearbeideroppgaver i kryptovaluta på datamaskiner til syke for å skaffe seg Monero-tokens til syke bekostning. The end result of this miner is the raised power expenses and also if you leave it for longer amount of times ICSYS.ICN.EXE might also damage your computers components.
icsys.icn.exe: distribusjonsmetoder
De icsys.icn.exe malware makes use of two prominent methods which are utilized to contaminate computer system targets:
- Nyttelast Levering via Tidligere infeksjoner. If an older ICSYS.ICN.EXE malware is deployed on the target systems it can instantly upgrade itself or download and install a more recent version. Dette er mulig ved hjelp av den innebygde oppgraderingskommandoen som får utgivelsen. Dette gjøres ved å feste til et spesifikt forhåndsdefinert hacker styrt server som gir den skadelige koden. Den nedlastede viruset vil sikkert få navnet på en Windows-tjeneste samt settes i “%Systemet% temp” plassering. Vital residential properties and also operating system arrangement documents are altered in order to allow a relentless and also quiet infection.
- Utnytter programvare for sikkerhetsproblem. The newest version of the ICSYS.ICN.EXE malware have actually been found to be brought on by the some ventures, kjent kjent for å bli brukt i ransomware-streik. Infeksjoner er gjort ved å målrette åpne tjenester via TCP port. Angrepene er automatiserte av hackere styrt ramme som søker ut om porten er åpen. If this condition is fulfilled it will certainly check the solution as well as recover details concerning it, inkludert alle typer versjoner og også oppsettdata. Exploits and also popular username and password combinations may be done. When the manipulate is caused versus the vulnerable code the miner will certainly be released together with the backdoor. Dette vil gi den en dobbel infeksjon.
Besides these techniques other strategies can be utilized also. Miners can be distributed by phishing emails that are sent wholesale in a SPAM-like fashion and also depend upon social engineering methods in order to perplex the sufferers into believing that they have actually gotten a message from a reputable solution or firm. The virus files can be either straight connected or placed in the body components in multimedia web content or message links.
The criminals can also develop harmful touchdown web pages that can pose vendor download and install web pages, software program download portals as well as various other often accessed areas. When they utilize similar sounding domain to legit addresses and safety certifications the customers may be coerced into connecting with them. I noen tilfeller rett og slett å åpne dem kan utløse miner infeksjon.
One more approach would certainly be to make use of payload providers that can be spread out making use of the above-mentioned approaches or using documents sharing networks, BitTorrent er blant de mest fremtredende. It is frequently utilized to disperse both legit software program and also files and also pirate material. Two of the most preferred payload providers are the following:
Other approaches that can be considered by the lawbreakers consist of the use of web browser hijackers -unsafe plugins which are made suitable with one of the most prominent web internet browsers. They are submitted to the pertinent repositories with phony user testimonials and also programmer qualifications. I mange tilfeller kan beskrivelsene bestå av skjermbilder, video clips and also intricate summaries appealing fantastic function improvements and also performance optimizations. Nonetheless upon installation the behavior of the impacted browsers will certainly alter- customers will certainly discover that they will be redirected to a hacker-controlled touchdown web page and their setups may be altered – standard startside, Internett-søkemotor, og også helt nye faner nettside.

icsys.icn.exe: Analyse
The ICSYS.ICN.EXE malware is a traditional instance of a cryptocurrency miner which depending on its arrangement can create a wide array of hazardous activities. Its primary objective is to carry out complicated mathematical tasks that will certainly make the most of the available system sources: prosessor, GPU, minne og også plass på harddisken. The way they work is by linking to a special server called mining swimming pool from where the called for code is downloaded and install. As soon as one of the tasks is downloaded it will certainly be started simultaneously, mange tilfeller kan utføres på en gang. When a provided task is finished an additional one will certainly be downloaded in its place and also the loop will continue until the computer is powered off, infeksjonen er eliminert eller en annen sammenlignbar anledning oppstår. Kryptovaluta vil bli kompensert for den kriminelle kontrollerne (hacking gruppe eller en enkelt cyberpunk) direkte til sine vesker.
A dangerous characteristic of this category of malware is that examples similar to this one can take all system resources and practically make the victim computer system pointless up until the threat has actually been entirely eliminated. A lot of them feature a relentless setup that makes them truly challenging to eliminate. Disse kommandoene vil sikkert gjøre endringer i oppstartsalternativer, arrangement documents as well as Windows Registry values that will certainly make the ICSYS.ICN.EXE malware beginning immediately as soon as the computer system is powered on. Accessibility to recovery food selections and alternatives might be obstructed which renders several hands-on elimination overviews virtually worthless.
Denne infeksjonen vil sette opp en Windows-tjeneste for seg selv, adhering to the performed safety analysis ther following actions have actually been observed:
. During the miner procedures the connected malware can hook up to already running Windows services and third-party set up applications. By doing so the system administrators might not see that the source tons originates from a different process.
| Navn | icsys.icn.exe |
|---|---|
| Kategori | Trojan |
| Underkategori | kryptovaluta Miner |
| farer | Høy CPU-bruk, Internett hastighetsreduksjon, PC krasjer og fryser og etc. |
| Hovedhensikt | For å tjene penger for kriminelle |
| Fordeling | torrents, Gratis spill, Cracked Apps, e-post, tvilsomme nettsteder, Utnytter |
| fjerning | Installere GridinSoft Anti-Malware for å detektere og fjerne Icsys.icn.exe |
These type of malware infections are especially reliable at performing advanced commands if configured so. They are based upon a modular framework permitting the criminal controllers to coordinate all type of hazardous habits. Blant de prominente tilfeller er endring av Windows-registeret – alterations strings related by the os can cause severe performance interruptions and the lack of ability to gain access to Windows solutions. Relying on the scope of changes it can likewise make the computer system entirely pointless. On the various other hand adjustment of Registry worths coming from any kind of third-party set up applications can undermine them. Some applications may fall short to launch completely while others can all of a sudden stop working.
This certain miner in its existing version is concentrated on extracting the Monero cryptocurrency including a customized variation of XMRig CPU mining engine. If the campaigns prove effective after that future versions of the ICSYS.ICN.EXE can be released in the future. Som malware bruker programvare program susceptabilities å infisere målet verter, det kan være bestanddel av en farlig samtidig infeksjon med ransomware og også trojanere.
Elimination of ICSYS.ICN.EXE is strongly recommended, because you run the risk of not only a huge electrical power costs if it is operating on your PC, yet the miner might also carry out other unwanted tasks on it and also harm your PC completely.
Icsys.icn.exe fjerningen
SKRITT 1. Først av alt, du må laste ned og installere GridinSoft Anti-Malware.
SKRITT 2. Da bør du velge “Rask skanning” eller “Full skanning”.
SKRITT 3. Kjør for å skanne datamaskinen
SKRITT 4. Etter at skanningen er fullført, du må klikke på “Søke om” knappen for å fjerne Icsys.icn.exe
SKRITT 5. Icsys.icn.exe Fjernet!
video guide: Hvordan bruke GridinSoft Anti-Malware for remove Icsys.icn.exe
Hvor å forhindre din PC blir infisert med “icsys.icn.exe” i fremtiden.
En kraftig antivirus løsning som kan oppdage og blokkere fileless malware er hva du trenger! Tradisjonelle løsninger oppdager malware basert på virusdefinisjoner, og dermed er de ofte ikke kan oppdage “icsys.icn.exe”. GridinSoft Anti-Malware gir beskyttelse mot alle typer malware inkludert fileless malware som “icsys.icn.exe”. GridinSoft Anti-Malware gir cloud-baserte atferd analysator for å blokkere alle ukjente filer, inkludert zero-day malware. Slik teknologi kan oppdage og fjerne “icsys.icn.exe”.







