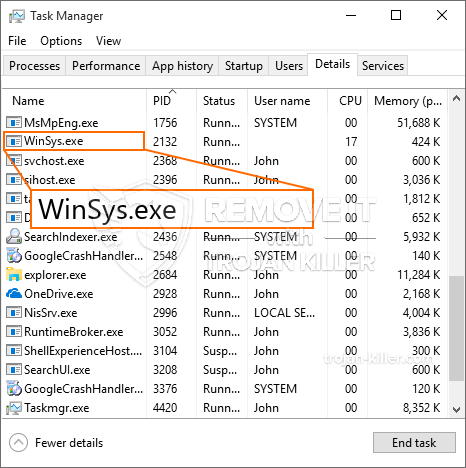
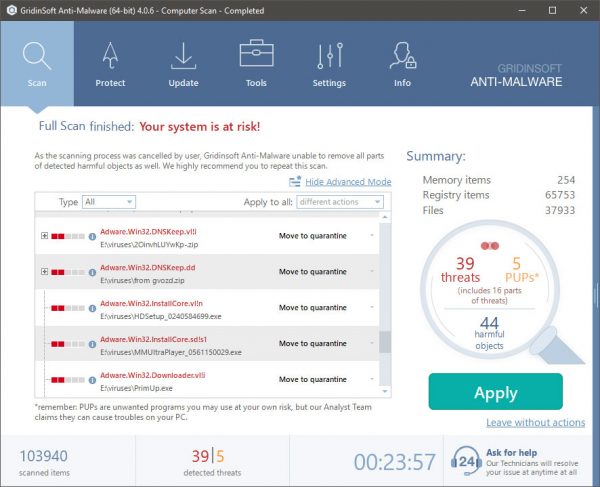
Een gloednieuw, Het extreem onveilige cryptocurrency miner-virus is daadwerkelijk opgemerkt door veiligheidsonderzoekers. de malware, riep WinSys.exe infecteren doel lijders maken van een selectie van middelen. The main point behind the WinSys.exe miner is to employ cryptocurrency miner activities on the computer systems of victims in order to acquire Monero symbols at targets expenditure. The end result of this miner is the elevated electrical power bills and if you leave it for longer periods of time WinSys.exe may even harm your computers elements.
WinSys.exe: distributiemethoden
De WinSys.exe malware toepassingen 2 popular approaches which are utilized to infect computer system targets:
- Payload Levering via Prior Infecties. If an older WinSys.exe malware is released on the victim systems it can automatically upgrade itself or download a newer variation. Dit is mogelijk met behulp van de geïntegreerde upgrade commando dat de lancering verwerft. Dit gebeurt door aan een speciaal vooraf bepaald hacker-gecontroleerde webserver die malware code geeft. De gedownloade infectie krijgt zeker de naam van een Windows-oplossing en wordt ook in de “%systeem% temp” Gebied. Vital residential or commercial properties and running system configuration documents are transformed in order to allow a consistent as well as silent infection.
- Software Application Vulnerability Exploits. The latest version of the WinSys.exe malware have been located to be triggered by the some ventures, widely understood for being made use of in the ransomware assaults. De infecties worden gedaan door zich te richten geopend diensten via de TCP-poort. De aanvallen zijn geautomatiseerd door een hacker gecontroleerd kader die opkijkt als de poort open. If this condition is met it will check the service and fetch information concerning it, including any variation as well as setup information. Exploits en ook de voorkeur gebruikersnaam en wachtwoord mixen zou kunnen worden gedaan. When the make use of is triggered versus the vulnerable code the miner will certainly be deployed along with the backdoor. Dit zal zeker bieden een dubbele infectie.
Besides these approaches various other strategies can be used too. Miners can be distributed by phishing emails that are sent out in bulk in a SPAM-like manner and rely on social design tricks in order to confuse the sufferers into believing that they have actually gotten a message from a legit service or business. The infection data can be either straight attached or inserted in the body materials in multimedia material or message web links.
The bad guys can additionally develop destructive landing web pages that can impersonate vendor download web pages, softwaretoepassing download sites en ook andere veelgebruikte gebieden. When they make use of similar seeming domain to legitimate addresses and safety and security certifications the customers might be persuaded right into interacting with them. In veel gevallen alleen het openen van hen kan verrekenen de mijnwerker infectie.
One more strategy would be to make use of haul service providers that can be spread using those techniques or using data sharing networks, BitTorrent is een van de meest prominente. It is regularly used to disperse both genuine software application and also documents and pirate web content. 2 van de meest prominente vervoerders zijn de volgende::
Other methods that can be thought about by the wrongdoers consist of using web browser hijackers -harmful plugins which are made suitable with one of the most popular internet browsers. They are published to the pertinent repositories with phony customer reviews and developer credentials. In de meeste gevallen kunnen de samenvattingen screenshots bevatten, videos and also fancy descriptions encouraging excellent feature enhancements as well as performance optimizations. Nonetheless upon installation the habits of the impacted internet browsers will certainly change- customers will find that they will certainly be rerouted to a hacker-controlled landing web page and their settings could be modified – de standaard webpagina, zoekmachine en nieuwe tabbladen pagina.
WinSys.exe: Analyse
The WinSys.exe malware is a timeless instance of a cryptocurrency miner which relying on its setup can cause a wide array of dangerous actions. Its primary objective is to carry out complicated mathematical tasks that will certainly make the most of the available system resources: processor, GPU, geheugen evenals harde schijf ruimte. The method they operate is by connecting to a special web server called mining swimming pool from where the called for code is downloaded and install. Zodra één van de taken is gedownload zal het zeker worden gelijktijdig begonnen, multiple circumstances can be gone for when. When a given job is completed one more one will certainly be downloaded and install in its area and also the loop will proceed up until the computer system is powered off, de infectie wordt weggedaan of één meer vergelijkbare gebeurtenis. Cryptogeld zal zeker beloond worden naar de correctionele controllers (hacken team of een eenzame hacker) direct naar hun begrotingen.
A dangerous quality of this group of malware is that examples like this one can take all system sources and also almost make the sufferer computer pointless until the threat has been totally eliminated. The majority of them include a consistent installation that makes them truly tough to get rid of. Deze opdrachten zullen wijzigingen ook alternatieven, arrangement files as well as Windows Registry values that will make the WinSys.exe malware begin immediately as soon as the computer system is powered on. Access to recuperation food selections as well as alternatives may be obstructed which renders several manual elimination guides practically useless.
Deze specifieke infectie zal zeker arrangement een Windows-service voor zichzelf, complying with the conducted safety analysis ther adhering to activities have actually been observed:
. During the miner procedures the associated malware can connect to currently running Windows solutions and third-party mounted applications. By doing so the system managers may not observe that the source load comes from a separate process.
| Naam | WinSys.exe |
|---|---|
| Categorie | Trojaans |
| Sub-categorie | cryptogeld Miner |
| gevaren | Hoog CPU-gebruik, Internet snelheidsreductie, PC crashes en bevriest en etc. |
| Hoofddoel | Om geld te verdienen voor cybercriminelen |
| Distributie | torrents, Gratis spellen, Cracked Apps, E-mail, dubieuze websites, exploits |
| Verwijdering | Installeren GridinSoft Anti-Malware to detect and remove WinSys.exe |
id =”82931″ align =”aligncenter” width =”600″]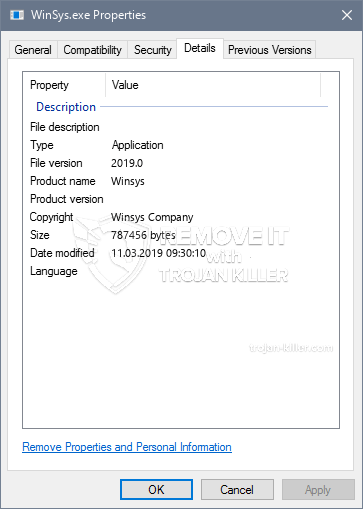 WinSys.exe
WinSys.exe
These type of malware infections are specifically effective at executing advanced commands if set up so. They are based upon a modular framework enabling the criminal controllers to orchestrate all kinds of hazardous behavior. Onder de prominente gevallen is de aanpassing van het Windows-register – alterations strings connected by the os can create significant performance disturbances as well as the lack of ability to accessibility Windows services. Depending upon the range of changes it can additionally make the computer system totally pointless. On the various other hand manipulation of Registry worths coming from any type of third-party mounted applications can sabotage them. Some applications may fall short to launch completely while others can suddenly quit working.
This certain miner in its present version is concentrated on mining the Monero cryptocurrency including a modified variation of XMRig CPU mining engine. If the campaigns prove successful after that future variations of the WinSys.exe can be introduced in the future. Als de malware maakt gebruik van software susceptabilities tot doel gastheren besmetten, het kan zijn onderdeel van een gevaarlijke co-infectie met ransomware en Trojaanse paarden.
Elimination of WinSys.exe is highly advised, given that you risk not just a large electrical energy expense if it is operating on your PC, yet the miner might additionally perform other unwanted tasks on it as well as even damage your PC permanently.
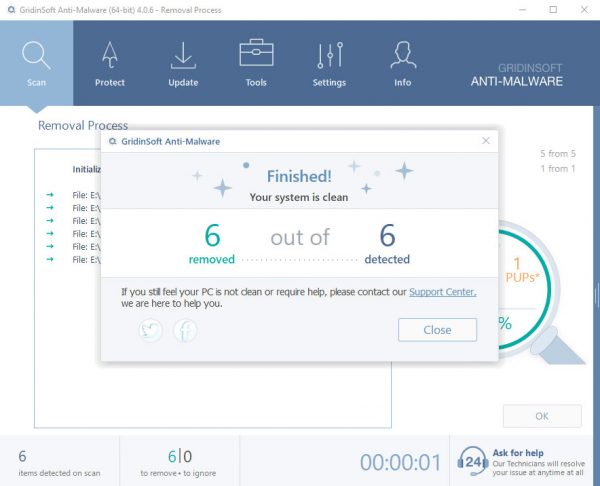
WinSys.exe removal process
STAP 1. Allereerst, je moet downloaden en te installeren GridinSoft Anti-Malware.
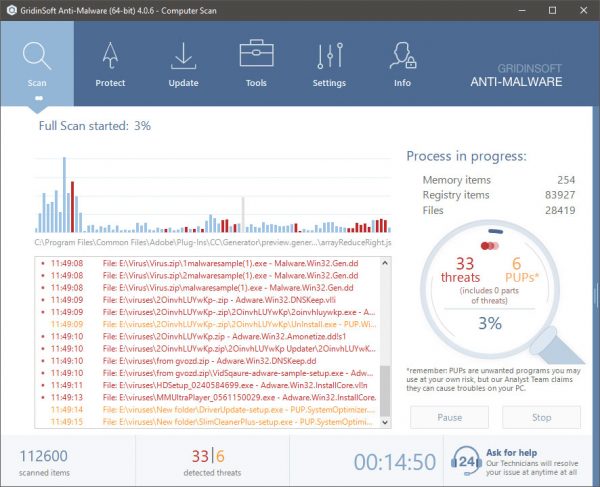
STAP 2. Dan moet je kiezen “Snelle scan” of “Volledige scan”.
STAP 3. Ren naar uw computer te scannen
STAP 4. Nadat de scan is voltooid, je nodig hebt om te klikken op “Van toepassing zijn” button to remove WinSys.exe
STAP 5. WinSys.exe Removed!
video Guide: How to use GridinSoft Anti-Malware for remove WinSys.exe
Hoe te voorkomen dat uw pc wordt geïnfecteerd met “WinSys.exe” in de toekomst.
Een krachtige antivirus oplossing die kan detecteren en blokkeren fileless malware is wat je nodig hebt! Traditionele oplossingen voor het detecteren van malware op basis van virusdefinities, en vandaar dat zij vaak niet kunnen detecteren “WinSys.exe”. GridinSoft Anti-Malware biedt bescherming tegen alle vormen van malware, waaronder fileless malware zoals “WinSys.exe”. GridinSoft Anti-Malware biedt cloud-gebaseerde gedrag analyzer om alle onbekende bestanden met inbegrip van zero-day malware te blokkeren. Deze technologie kan detecteren en volledig te verwijderen “WinSys.exe”.