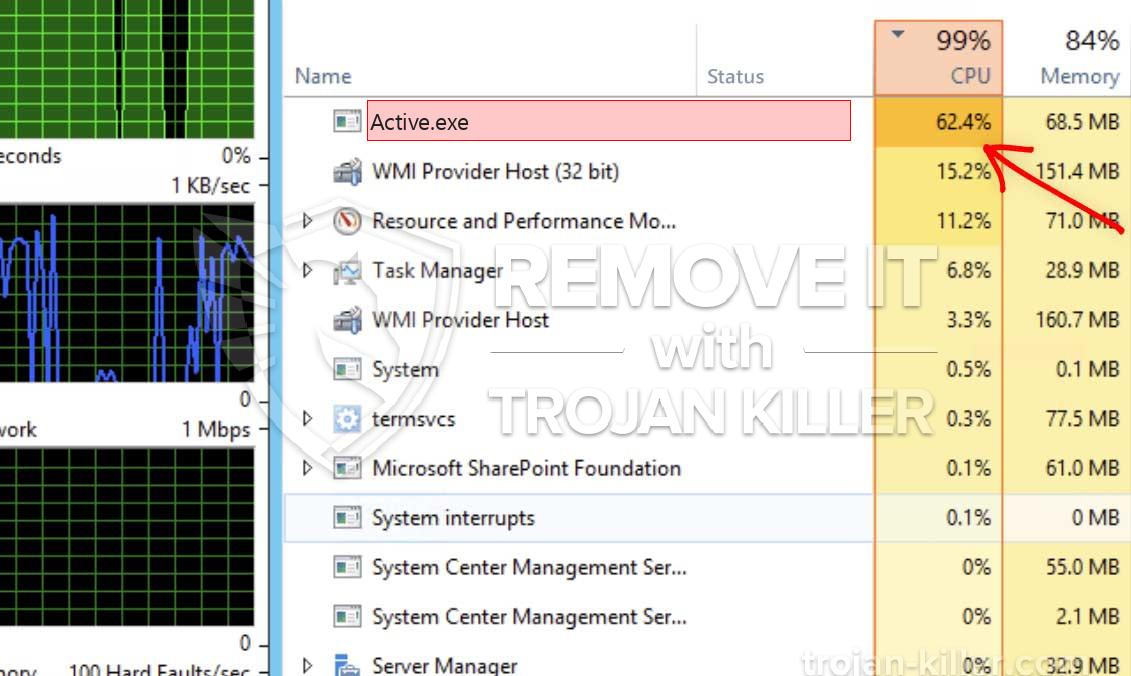
Een nieuw, Er is een zeer gevaarlijke infectie met cryptocurrency-mijnwerkers gevonden door veiligheids- en beveiligingswetenschappers. de malware, riep Active.exe kunnen besmetten doel slachtoffers met behulp van een scala van manieren. De essentie achter de Active.exe-mijnwerker is om cryptocurrency-mijnwerkersactiviteiten op de computersystemen van slachtoffers toe te passen om Monero-tokens bij slachtoffers te krijgen’ kosten. Het resultaat van deze mijnwerker is de verhoogde elektriciteitskosten en als u deze voor langere tijd laat staan, kan Active.exe ook de componenten van uw computersysteem beschadigen.
Active.exe: distributiemethoden
De Active.exe malware maakt gebruik van twee voorkeursbenaderingen die worden gebruikt om computerdoelen te infecteren:
- Payload Delivery gebruik Prior Infecties. Als een oudere Active.exe-malware wordt vrijgegeven op de systemen van het slachtoffer, kan deze zichzelf onmiddellijk upgraden of een recentere versie downloaden. Dit is mogelijk door middel van het ingebouwde update-commando dat de release verwerft. Dit gebeurt door het koppelen van een bepaalde vooraf gedefinieerde hacker gecontroleerde server die de malware code biedt. Het gedownloade virus krijgt zeker de naam van een Windows-service en wordt in de “%systeem% temp” Gebied. Cruciale eigenschappen en actieve systeemconfiguratiebestanden worden gewijzigd om een meedogenloze en ook stille infectie mogelijk te maken.
- Software Application Vulnerability Exploits. Er is ontdekt dat de nieuwste variant van de Active.exe-malware wordt geactiveerd door enkele ondernemingen, staat bekend om het gebruik van de ransomware-aanvallen. De infecties worden gedaan door zich te richten geopend oplossingen via de TCP-poort. De aanvallen zijn geautomatiseerd door een hacker gecontroleerd kader die opkijkt als de poort open. Als aan deze voorwaarde is voldaan, zal het zeker de oplossing controleren en er ook informatie over ophalen, waaronder elk type variatie alsook configuratiedata. Ventures evenals prominente gebruikersnaam en wachtwoord mixen kan worden gedaan. Wanneer de exploit wordt veroorzaakt tegen de vatbare code, zal de miner zeker samen met de achterdeur worden vrijgegeven. Dit zal zeker over een duale infectie.
Naast deze methoden kunnen ook andere technieken worden gebruikt. Mijnwerkers kunnen worden verspreid via phishing-e-mails die op een SPAM-achtige manier in bulk worden verzonden en die ook afhankelijk zijn van sociale ontwerpmethoden om de slachtoffers te laten geloven dat ze een bericht hebben ontvangen van een legitieme oplossing of bedrijf. De infectiegegevens kunnen direct worden verbonden of in de lichaamscomponenten worden geplaatst in multimediawebinhoud of berichtweblinks.
De oplichters kunnen ook schadelijke bestemmingspagina's ontwikkelen die zich kunnen voordoen als download- en installatiepagina's van leveranciers, websites voor het downloaden van software en ook diverse andere vaak bezochte plaatsen. Wanneer ze een vergelijkbaar lijkend domein gebruiken voor legitieme adressen en ook beveiligingscertificaten, kunnen de klanten ertoe worden aangezet om met hen te communiceren. Soms zijn ze gewoon te openen kan de mijnwerker infectie activeren.
Een extra methode zou zijn om payload-serviceproviders te gebruiken die kunnen worden verspreid door gebruik te maken van die benaderingen of via netwerken voor het delen van documenten, BitTorrent is slechts een van een van de meest geprefereerde. Het wordt vaak gebruikt om zowel gerenommeerde software als documenten en piratenmateriaal te verspreiden. Twee van één van de meest geprefereerde haul providers zijn de volgende::
Verschillende andere benaderingen die door de slechteriken kunnen worden overwogen, zijn onder meer het gebruik van internetbrowserkapers - gevaarlijke plug-ins die geschikt zijn gemaakt met een van de meest geprefereerde webbrowsers. Ze worden ingediend bij de juiste opslagplaatsen met valse klantevaluaties en ook ontwerperkwalificaties. In de meeste gevallen kunnen de samenvattingen screenshots bevatten, videoclips en ook uitgebreide samenvattingen die geweldige attribuutverbeteringen en prestatie-optimalisaties beloven. Na installatie zullen de acties van de getroffen internetbrowsers echter zeker veranderen- klanten zullen ontdekken dat ze worden omgeleid naar een door een hacker gecontroleerde bestemmingswebpagina en dat hun instellingen kunnen worden gewijzigd – de standaard startpagina, zoekmachine en nieuwe tabbladen webpagina.

Active.exe: Analyse
De Active.exe-malware is een traditionele situatie van een cryptocurrency-mijnwerker die, afhankelijk van de installatie ervan, een breed scala aan onveilige activiteiten kan veroorzaken. Het belangrijkste doel is om complexe wiskundige taken uit te voeren die zullen profiteren van de direct beschikbare systeembronnen: processor, GPU, geheugen en ruimte op de harde schijf. De manier waarop ze werken is door verbinding te maken met een speciale server genaamd mining pool waar de benodigde code wordt gedownload en geïnstalleerd. Zo snel als een van de taken is gedownload zal worden begonnen in een keer, talrijke gevallen kan worden uitgevoerd in een keer. Wanneer een bepaalde taak is voltooid, zal er zeker nog een worden gedownload op zijn locatie en de lus zal zeker doorgaan totdat het computersysteem wordt uitgeschakeld, de infectie wordt verwijderd of er vindt een soortgelijke gebeurtenis plaats. Cryptogeld zal worden gecompenseerd voor de criminele controllers (hacken groep of een eenzame cyberpunk) rechtstreeks naar hun portemonnee.
Een schadelijk kenmerk van deze categorie malware is dat voorbeelden die vergelijkbaar zijn met deze alle systeembronnen kunnen gebruiken en het doelcomputersysteem praktisch zinloos kunnen maken totdat het gevaar volledig is weggenomen. De meeste van hen bevatten een permanente installatie waardoor ze erg moeilijk te verwijderen zijn. Deze commando's zullen veranderingen op te starten opties maken, arrangementdocumenten en ook Windows Register-waarden die ervoor zorgen dat de Active.exe-malware onmiddellijk begint wanneer de computer wordt ingeschakeld. Toegang tot herstelmenu's en -opties kan worden belemmerd, waardoor veel handmatige verwijderingsoverzichten bijna nutteloos zijn.
Deze specifieke infectie zal een Windows-oplossing voor zichzelf configureren, voldoen aan de uitgevoerde beschermingsevaluatie zijn de volgende activiteiten daadwerkelijk waargenomen:
. Tijdens de miner-procedures kan de verbonden malware verbinding maken met momenteel draaiende Windows-services en aangekoppelde applicaties van derden. Door dit te doen, merken de systeembeheerders mogelijk niet op dat de brontonen afkomstig zijn uit een afzonderlijke procedure.
| Naam | Active.exe |
|---|---|
| Categorie | Trojaans |
| Sub-categorie | cryptogeld Miner |
| gevaren | Hoog CPU-gebruik, Internet snelheidsreductie, PC crashes en bevriest en etc. |
| Hoofddoel | Om geld te verdienen voor cybercriminelen |
| Distributie | torrents, Gratis spellen, Cracked Apps, E-mail, dubieuze websites, exploits |
| Verwijdering | Installeren GridinSoft Anti-Malware om Active.exe te detecteren en te verwijderen |
Dit soort malware-infecties zijn bijzonder betrouwbaar bij het uitvoeren van geavanceerde opdrachten, indien zo geconfigureerd. Ze zijn gebaseerd op een modulair raamwerk waardoor de opsporingsambtenaren allerlei onveilig gedrag kunnen coördineren. Een van de belangrijkste voorbeelden is de wijziging van het Windows-register – aanpassingsreeksen die door het besturingssysteem worden geassocieerd, kunnen ernstige verstoringen van de efficiëntie veroorzaken, evenals de onmogelijkheid om Windows-oplossingen toegankelijk te maken. Afhankelijk van de omvang van de wijzigingen kan het bovendien het computersysteem totaal onbruikbaar maken. Aan de andere kant kan de controle van registerwaarden die toebehoren aan door derden ingestelde applicaties deze saboteren. Sommige toepassingen werken mogelijk niet meer om volledig te worden vrijgegeven, terwijl andere plotseling kunnen stoppen met werken.
Deze bepaalde mijnwerker in zijn bestaande variatie is geconcentreerd op het delven van de Monero-cryptocurrency, inclusief een aangepaste variant van de XMRig CPU-mijnengine. Als de projecten effectief blijken te zijn, kunnen toekomstige versies van Active.exe in de toekomst worden geïntroduceerd. Als de malware maakt gebruik van software susceptabilities tot doel hosts te infecteren, het kan deel uitmaken van een schadelijke co-infectie met ransomware en ook Trojaanse paarden.
Eliminatie van Active.exe wordt sterk aanbevolen, omdat u niet alleen grote kosten voor elektrische energie riskeert als deze aan uw COMPUTER werkt, de mijnwerker kan er echter ook verschillende andere ongewenste taken op uitvoeren en zelfs uw COMPUTER permanent beschadigen.
Active.exe-verwijderingsproces
STAP 1. Allereerst, je moet downloaden en te installeren GridinSoft Anti-Malware.
STAP 2. Dan moet je kiezen “Snelle scan” of “Volledige scan”.
STAP 3. Ren naar uw computer te scannen
STAP 4. Nadat de scan is voltooid, je nodig hebt om te klikken op “Van toepassing zijn” knop om Active.exe te verwijderen
STAP 5. Active.exe verwijderd!
video Guide: Hoe GridinSoft Anti-Malware te gebruiken voor het verwijderen van Active.exe
Hoe te voorkomen dat uw pc wordt geïnfecteerd met “Active.exe” in de toekomst.
Een krachtige antivirus oplossing die kan detecteren en blokkeren fileless malware is wat je nodig hebt! Traditionele oplossingen voor het detecteren van malware op basis van virusdefinities, en vandaar dat zij vaak niet kunnen detecteren “Active.exe”. GridinSoft Anti-Malware biedt bescherming tegen alle vormen van malware, waaronder fileless malware zoals “Active.exe”. GridinSoft Anti-Malware biedt cloud-gebaseerde gedrag analyzer om alle onbekende bestanden met inbegrip van zero-day malware te blokkeren. Deze technologie kan detecteren en volledig te verwijderen “Active.exe”.







