Password-stealing malware LokiBot started hiding its code in pictures


The famous LokiBot malware now uses steganography as an extra layer of obfuscation.
Researchers at Trend Micro have recorded a new variant of the malware and conducted its analysis. Apparently, the authors are now actively finalizing and improving LokiBot.“Our analysis of a new LokiBot variant shows that it has improved its capabilities for staying undetected within a system via an updated persistence mechanism and the use of steganography to hide its code”, — reported Trend Micro researchers.
A malicious program has been adopted by some cybercriminal groups, including Nigerian attackers SilverTerrier.
Read also: The new version of the banking Trojan TrickBot “kicks off” Windows Defender
LokiBot can steal information from 25 different browsers, check the availability of tools for remote administration (SSH, VNC, RDP), and retrieve credentials from email clients.
In the latest versions of malware, the authors taught him to hide code in images.
“One characteristic of the image file that we found interesting is that it can actually be opened as an image. However, it also contains data that LokiBot references in its unpacking routine”, — explained Trend Micro specialists.

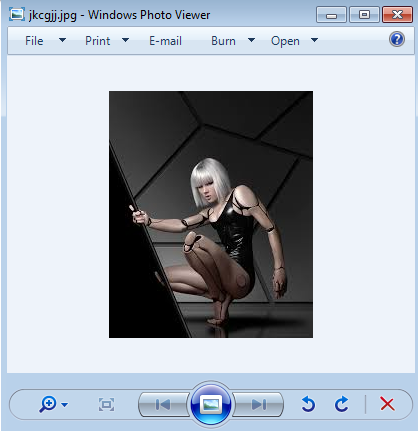
This code is used at one stage of the attack to unpack. An analysis of experts showed that the image contains an encrypted binary, which the malware uses to decrypt LokiBot in the RAM of the infected device.
“One likely reason for this particular variant’s reliance on steganography is that it adds another layer of obfuscation — wscript (the VBS file interpreter) is used to execute the malware instead of the actual malware executing itself. Since the autostart mechanism uses a script, future variants can choose to”, — Trend Micro specialists write.
Researchers note that this approach, that LokiBot malware uses steganography, not only allows the malware to bypass detection, but also to become stronger in the attacked system.
Recent Posts
Remove Rengine.click Pop-up Ads
About Rengine.click Rengine.click pop-ups can not expose out of the blue. If you have actually…
Remove Xzcczxxx.xyz Pop-up Ads
About Xzcczxxx.xyz Xzcczxxx.xyz pop-ups can not introduce out of nowhere. If you have clicked on…
Remove Xefkqo.info Pop-up Ads
About Xefkqo.info Xefkqo.info pop-ups can not open out of nowhere. If you have actually clicked…
Remove Rt9.lol Pop-up Ads
About Rt9.lol Rt9.lol pop-ups can not introduce out of the blue. If you have actually…
Remove Sex-hd.xxx Pop-up Ads
About Sex-hd.xxx Sex-hd.xxx pop-ups can not launch out of the blue. If you have actually…
Remove Curestin.co.in Pop-up Ads
About Curestin.co.in Curestin.co.in pop-ups can not introduce out of nowhere. If you have actually clicked…


