
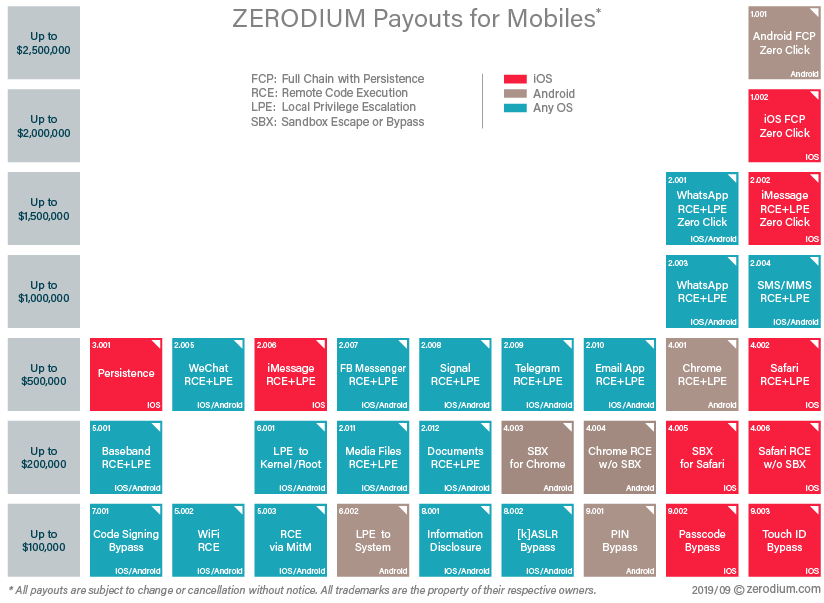
잘 알려진 취약점 브로커, Zerodium, 그 가격리스트를 업데이트했습니다, 지금은 안드로이드에 대한 역사 공격에서 처음으로 iOS 용 공격보다 더 비싸다.
나는S 연구자들은 안드로이드에 대한 0 일 버그에 벌 수있는 기회를 가질 수, 의 동작은 사용자의 상호 작용을 필요로하지 않습니다, 까지 $2,500,000. 아이폰 OS 비용 비슷한 공격 $2,000,000.그러므로, Zerodium 거의 안드로이드에 대한 이러한 공격에 대한 보상을 제기 12 전년 대비 배 (불러 오기, 구글 운영 체제의 이전 문제는 더 이상 가지고 있지 않았다 $200,000). 작은 구경의 취약점에 대한, 비용은 증가했다 이상 100 타임스. 발표는 확실히 안드로이드의 공식 출시에 맞춰 시간이 초과되었습니다 10, 또한 어제 일어난, 구월 3, 2019.
또한, 취약점 브로커는 메신저에 대한 공격의 비용을 상승, 에 관계없이 OS에 그들은 실행. 이제 WhatsApp에와 iMessage를의 RCE 및 LPE 문제는 추정된다 $1,500,000, 심지어는 다시 부팅 한 후 시스템의 존재를 유지하는 것을 허용하지 않습니다 악용하는 경우.
문제는 사용자 상호 작용이 필요한 경우, 익스플로잇 체인의 가격은 감소 $1,000,000 WhatsApp에와 최대 버그 $500,000 iMessage를 버그에 대한. 작년, 이러한 취약점은 더 이상의 연구원을 가져다하지 않을 것이다 $500,000.
Zerodium의 머리, Chauki Bekrar, 이야기 ZDNet의 기자가 모금 가격, 그의 회사는 시장 동향에 응답.
사실은 그 Zerodium 비즈니스 모델 (때문에 어느 회사가 반복적으로 가혹한 비판 하였다) 회사가 0 일에 대한 정보가 독립적으로 발견하고 비밀을 제 3 자로부터 구입 한 유지하도록이다, 대기업에 재판매 동안, 정부 기관 및 법 집행 기관 구조. 예를 들면, 국가 안보국이나 군사. 그러므로, 가격 인상은 Zerodium 클라이언트 그 관심에 의해 설명 될 수있다 (그건, 세계의 법 집행 기관 및 정부 기관) 안드로이드 문제를 보여주고있다.
Bekrar 그 때문에 안드로이드 기기 시장의 큰 조각을 말한다, 이 회사는 주로 장치 구글에 버그에 관심이있다, 삼성, 화웨이와 소니, 다른 브랜드도 무시되지 않습니다 있지만,.
"지난 몇 개월 동안, 우리는 iOS 용 공격의 증가를 보았다, 주로 사파리와 iMessage를위한, 생성 및 세계 각국의 연구자들에 의해 판매되는. iOS 용 공격으로 포화 0 일 시장은 최근 것을 우리는 심지어 그 중 일부를 포기하기 시작. 다른 한편으로는, 구글과 삼성의 보안 팀에 감사, 안드로이드의 보안은 각 새 릴리스로 개선, 전체 개발 있도록 안드로이드에 대한 체인이 복잡하고 시간이 많이 걸리는 작업이되었다 악용, "심지어 사용자 상호 작용을 필요로하지 않는 제로 클릭 악용을 만드는 능가, Bekrar 말한다, 가격 인상을 설명.
노트 Beckrar 안드로이드 익스플로잇은 애플이 아이폰 OS의 보안을 강화하고 약점을 강화 할 때까지 아이폰 OS가 악용보다 높은 평가됩니다, iMessage를 사파리 등 (웹킷 및 샌드 박스).
