연구팀은 Windows에서 이상한 행동을 지적 10 사용자가 Microsoft 가장자리에 악성 코드 파일을 연 후 그 침입자는 원격으로 하드 디스크에 저장된 파일을 도용 할 수 있습니다.
에프or the first time problem was reported when cybersecurity researcher John Page published information about vulnerability in Microsoft Internet Explorer 11 즉, 마이크로 소프트 OS의 파일에 개방 액세스 할 수 있습니다. Page also published PoC-code for this bug after Microsoft refused developing a patch.하나, 에 따르면 Mitja Kolsek, ACROS Security specialist, technological giant underestimated threat of this vulnerability as it manifests not only with outdated IE, but also in modern Edge. 그 위에, published by Page exploit can be processed to a version that opens with Edge.
It may be strange, but firstly specialist could not repeat an attack with the use of IE in Windows 7 and could not upload malware MHT-file as Page described it. Though process manager showed that system.ini file that could be stolen was read by script in MHT-file, it was not sent to remote server.
“This looked like a classic “mark-of-the-Web” situation. When a file is obtained from the Internet, well-behaved Windows applications like Web browsers and email clients add a mark to such [에이] file in [그만큼] form of an alternate data stream named Zone.Identifier, containing a line ZoneId=3. This allows other applications to know that the file has come from an untrusted source—and should thus be opened in a sandbox or an otherwise limited environment.”, – Kolsek wrote.
According to Kolsek, IE really put a mark on uploaded MHT-file. When investigator tried to upload same file with Edge and open in in IE, exploit worked. After precise analysis expert established that Edge added two notes in access control list that adds right to read a file to some system service.
같이 조언 Google Project Zero specialist James Foreshaw, added by Edge identifiers are group security identifiers for Microsoft.MicrosoftEdge_8wekyb3d8bbwe PACKET. After removing second line SID S-1-15-2 -* from the list of access control exploit did not work again. 이런 식으로, permission that added Edge allowed missing IE sandbox.
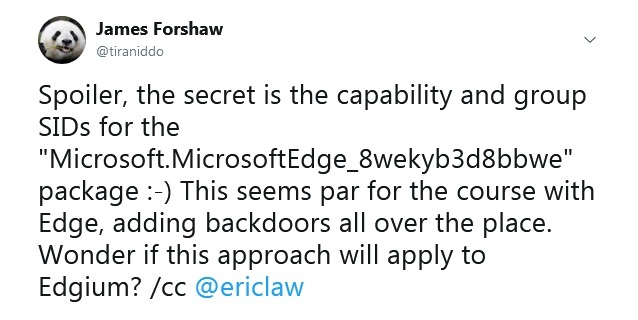
James Forshaw tweet
More detailed analysis demonstrated that established by Edge permission did not allow Win Api GetZoneFromAlternateDataStreamEx function to read Zone.Indetifier flow and returned an error. 최종적으로, IE considered that file does not have mark-of-the-Web mark and sent it to remote server.
Despite additional details about vulnerability, it is unlikely that Microsoft will fix it soon.
“We determined that a fix for this issue will be considered in a future version of this product or service. At this time, we will not be providing ongoing updates of the status of the fix for this issue, and we have closed this case.”, — stated in Microsoft .
In this connection, ACROS Security has released a vulnerability patch, available on the 0Patch platform.
