알 수없는 침입자는 이상의 누출 일으켰 용기 이미지의 세계 최대의 라이브러리의 데이터에 대한 액세스를 받았다 190 수천 사용자의 자격 증명.
디ocker Hub developers detected that third persons got unauthorized access to one of project databases that stored non-financial users’ details.“목요일에, 4 월 25, 2019, we discovered unauthorized access to a single Hub database storing a subset of non-financial user data,” 말했다 Kent Lamb, Director of Docker Support.
As emphasized, intruders stayed in system for a relatively short time, 하나, according to preliminary research, that was enough to compromise 190 000 계정 that consists nearly 5% of all Docker Hub users’ base.
In the attack were compromised users’ names, passwords’ hashes, and tokens for GitHub and Bitbucket repositories that were used for Docker automatized assemblies.
Mentioned above tokens that are stored in Docker Hub, allow developers to modify codes of their projects and automatically create images on Docker Hub. If intruder will get tokens, it will open him access to private repositories and change it depending on allocated by token permissions. Compromising image and modifying code, hacker will seriously damage supply chain, as Docker Hub images are often used in servers’ and applications configurations.
Docker Hub team notified users and reset passwords of compromised accounts.
“For users with autobuilds that may have been impacted, we have revoked GitHub tokens and access keys, and ask that you reconnect to your repositories and check security logs to see if any unexpected actions have taken place,” Lamb said in the email the company sent customers.
Docker’s team have already withdrawn all compromised tokens and access keys, 하나, all developers that use automatized Docker Hub constructors, are highly recommended to check all projects for unsanctioned access.
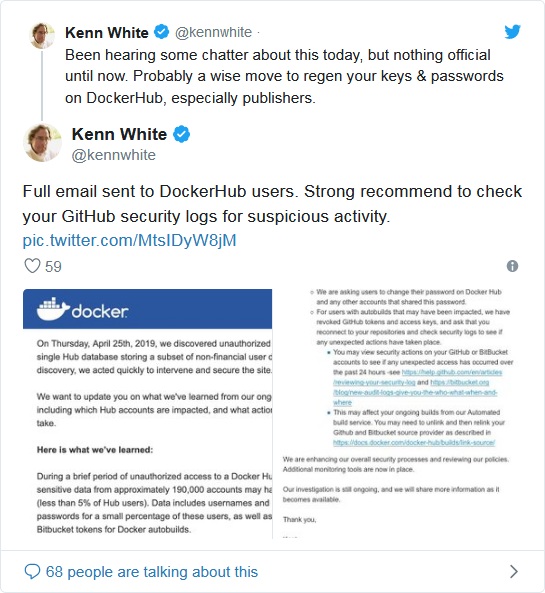
Experts are sharing on the Internet a letter from Docker Hub
Though hacker’s access to 5% of users’ accounts does not seem to be a critical issue, the spectrum of ramifications may be broad. As majority of Docker Hub users are employees of big companies, they could use their accounts for creation of containers that are later applied in real enterprise environments. After attack, hackers may introduce malware code in IT-systems of large companies worldwide.
Investigation of incident and assessment of possible damage continues.
