JavaScript Loader Dispensing RATs


JavaScript RATs Trojans
Not long ago researchers from HP Threat Research Blog reported on newly discovered in the wild RATDispenser. This elusive JavaScript loader distributes information stealers and remote access Trojans (RATs). It successfully avoids security controls while delivering malware.
This RATs Dispenser may operate as a malware-as-a-service business model
The variety of malware families this RATs Dispenser distributes makes one think that here attackers apply malware-as-a-service business model. Many of the distributed malware families potential attackers can buy or download freely from underground marketplaces. And all those payloads were RATs that allowed attackers to gain control over victims’ devices and steal information. In total, researchers identified eight malware families distributed by this RATs Dispenser.

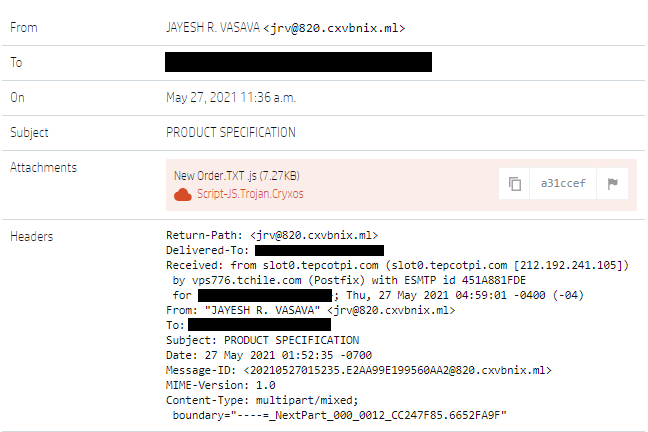
Usually attackers use JavaScript malware to gain an initial foothold on a system before it launches secondary malware that sets up control over the compromised device. In their report researchers discussed the malware families distributed by this particular RATs Dispenser. They analyzed the infection chain of RATs Dispenser and proposed a variant of detection opportunities to detect and block its work. In addition researchers shared a YARA rule and a Python extraction script for network defenders to be able to detect and analyze this malware.
The team analyzed the 155 malware samples
Of all the 155 malware sample using their script they found:
The infection chain begins with an email that contains malicious attachment. For example one may receive some letter about an order just to check what the order goes about the user clicks on it. And that is when the execution of a file begins. The research team advises network defenders to block executable email attachment file types with a VBScript or JavaScript, for example. The interruption of malware execution can be done by disabling Windows Script Host (WSH) or changing the default file handler for JavaScript files and only allowing digitally signed scripts to run.
Researchers identified eight distributed malware
To identify which types of malware this RATs Dispenser distributes the researchers wrote a signature to track its sightings. Among the various malware it delivered Formbook, information stealer and a keylogger. Other types included Remcos,STRRAT, WSHRAT, Panda Stealer, AdWind, GuLoader and Ratty. From them the most frequently observed were STRRAT and WSHRAT accounting for 81% of the samples analyzed. In contrast the least frequently observed researchers name Ratty and GuLoader.
Some malware RATs Dispenser only downloaded like Formbook and Panda Stealer while others mostly it dropped. Additionally researchers provided a few words on some of the distributed malware. They wrote that STRRAT is a Java RAT that has remote access, keylogging and credential stealing features and specialists detected it for the first time in mid-2020. WSHRAT, which also goes by the name Houdini, is a VBS RAT first detected in 2013. Both have typical RAT capabilities. To them the most interesting is Panda Stealer. This new malware family appeared in April 2021 and targets cryptocurrency wallets. GuLoader downloads and runs various RATs and Ratty is an open-source RAT written in Java.
At the end researchers added that although JavaScript is a less common malware file format than Microsoft Office archives and documents, antivirus software poorly detects it. Indeed they analyzed its detection rate and got the results of 11% by antivirus engines, or eight engines.
Recent Posts
Remove Phish.sms Pop-up Ads
About Phish.sms Phish.sms pop-ups can not launch out of the blue. If you have actually…
Remove Hotbvipuro.today Pop-up Ads
About Hotbvipuro.today Hotbvipuro.today pop-ups can not expose out of nowhere. If you have clicked on…
Remove Vfirewall.pro Pop-up Ads
About Vfirewall.pro Vfirewall.pro pop-ups can not launch out of nowhere. If you have actually clicked…
Remove Hotbguxihu.today Pop-up Ads
About Hotbguxihu.today Hotbguxihu.today pop-ups can not introduce out of the blue. If you have actually…
Remove Irlitathal.com Pop-up Ads
About Irlitathal.com Irlitathal.com pop-ups can not launch out of nowhere. If you have actually clicked…
Remove Hotbvukupa.today Pop-up Ads
About Hotbvukupa.today Hotbvukupa.today pop-ups can not introduce out of the blue. If you have clicked…


