
Experten der chinesischen Unternehmen KnownSec 404 dass die entwickelten IoT-searching Motor ZoomEye, entdeckt gefährliche Schwachstelle in Oracle WebLogic.
EINnach ZoomEye, im Internet kann mehr als gefunden werden 36 000 verfügbar WebLogic Server, die hinter dem neuen Problem anfällig sind. Die meisten von ihnen sind in den USA und China.Die Forscher erklären,Dieser Fehler ist für alle Server von Oracle WebLogic gefährlich, auf denen die Komponenten WLS9_ASYNC und WLS-WSAT ausgeführt werden. Die erste Komponente ist für asynchrone Operationen erforderlich, während die zweite eine Schutzlösung ist. Da noch keine Korrekturen verfügbar sind, Experten geben keine technischen Details preis, schreiben aber, dass die Schwachstelle mit Deserialisierung verbunden ist und es Hackern ermöglicht, aus der Ferne beliebige Befehle ohne Autorisierung auszuführen (mit der Verwendung einer speziellen HTTP-Anfrage).
Als vorbeugende Maßnahme wird empfohlen, problematische Komponenten entweder vollständig zu beseitigen, indem Sie sie löschen und den WebLogic-Server neu starten, oder Regeln erstellen, die Anfragen an /_async/* und /wls-wsat/* verbieten.
Internet-Sicherheitsexperten anderer Unternehmen bestätigen dies, diese Schwachstelle wird wirklich angegriffen (Hacker sind sich dessen bereits bewusst) Hacker untersuchen jedoch nur, da ihre Angriffe darauf beschränkt sind, anfällige Teile von WebLogic-Servern zu scannen und Versuche zu testen, den Fehler auszunutzen. Eindringlinge versuchen nicht, Malware auf ihren Servern zu platzieren oder sie für andere böswillige Operationen zu verwenden.
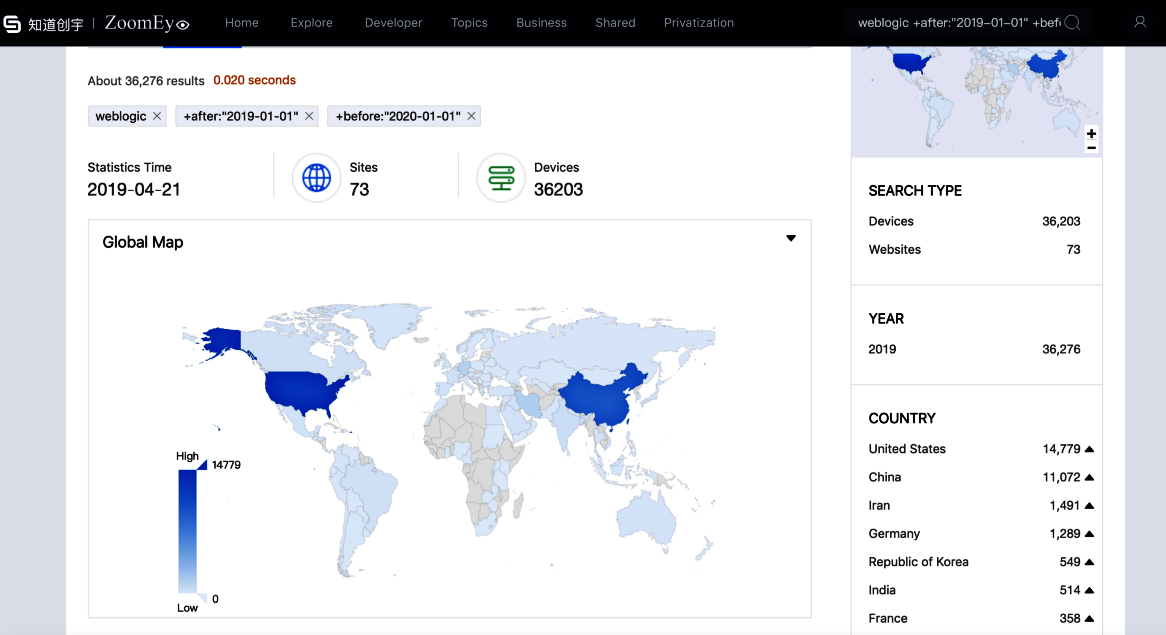
36 000 verfügbar WebLogic Server, die hinter dem neuen Problem anfällig sind, Nach ZoomEye.
Unglücklicherweise, dieser Zustand wird nicht lange anhalten, Die leistungsstarken und äußerst beliebten Oracle WebLogic-Server in Unternehmensumgebungen sind seit langem ein beliebtes Ziel für Eindringlinge. Zum Beispiel, Im Dezember 2018 wurden Fälle behoben, in denen verstecktes Schürfen auf Oracle WebLogic-Servern Internet-Betrüger um mehr als bereicherte $226 000.
Obwohl die Hersteller die Kunden über die Schwachstelle informiert haben, Oracle hat sein vierteljährliches Patch-Set erst letzte Woche auf den Markt gebracht, So, Patch für einen neuen Fehler, der erst in einigen Monaten eintreffen wird.
Zum Zeitpunkt der Ausgabe dieser Warnung, der Beamte hat den entsprechenden Fix immer noch nicht veröffentlicht, Dabei handelt es sich um eine „0day“-Schwachstelle. Ein Angreifer könnte diese Schwachstelle ausnutzen, um Befehle ohne Autorisierung aus der Ferne auszuführen, — berichtete KnownSec 404 Spezialisten.
Der Fehler hat die Kennung CNVD-C-2019-48814 erhalten.
