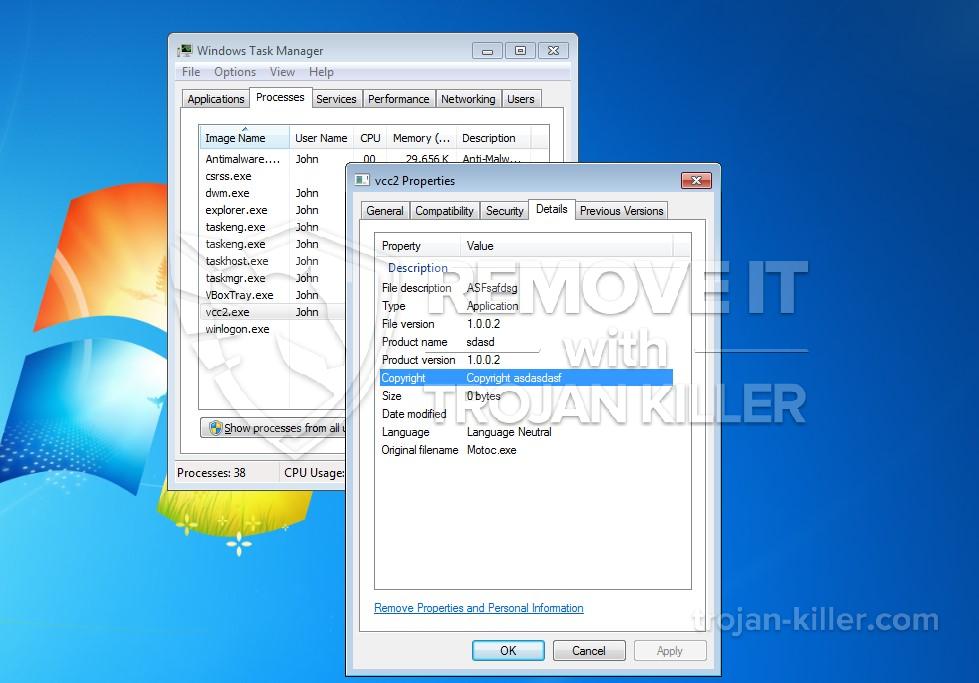
Et helt nyt, ekstremt usikre cryptocurrency minearbejder virus rent faktisk er blevet spottet af sikkerhedsmæssige forskere. den malware, hedder Vcc2.exe kan forurene måloffer ved hjælp af et udvalg af måder. Hovedpunktet bag Vcc2.exe-minearbejderen er at bruge cryptocurrency-minearbejder på computersystemer for mål for at opnå Monero-symboler til ofrets udgift. Resultatet af denne minearbejder er de forhøjede elektriske strømomkostninger såvel som hvis du lader det være i længere perioder. Vcc2.exe kan endda skade dine computerelementer.
Vcc2.exe: distributionssystemer Metoder
Det Vcc2.exe malware anvendelser 2 populære tilgange, der bruges til at inficere computersystemmål:
- Nyttelast Levering ved hjælp af kendte Infektioner. Hvis en ældre Vcc2.exe malware er implementeret på offerets systemer, kan den straks opgradere sig selv eller downloade og installere en nyere variant. Dette er muligt ved hjælp af den integrerede opdatering kommando, som opnår frigivelse. Dette gøres ved at tilknytte en bestemt foruddefineret hacker-styret webserver, der leverer malware-koden. Den downloadede og installerede infektion får helt sikkert navnet på en Windows-tjeneste og placeres også i “%systemet% temp” Beliggenhed. Vigtige beboelsesejendomme og opsætningsdata for operativsystemet ændres for at muliggøre en ubarmhjertig og lydløs infektion.
- Software sårbarhed udnytter. Den seneste variant af Vcc2.exe-malware har faktisk vist sig at være fremkaldt af nogle udnyttelser, populært anerkendt for at blive brugt i ransomware-angrebene. Infektionerne er færdig ved at målrette åbne tjenester ved hjælp af TCP port. Strejkerne er automatiseret af en hacker-kontrolleret struktur, som søger efter hvis porten er åben. Hvis denne betingelse er opfyldt, vil den scanne løsningen og også hente oplysninger om den, inklusive enhver form for version og arrangementdata. Udnyttelser og populært brugernavn samt adgangskodekombinationer kan gøres. Når brugen af er modregnet i forhold til den udsatte kode, udlægges minearbejderen ud over bagdøren. Dette vil præsentere en dobbelt infektion.
Udover disse tilgange kan også andre tilgange anvendes. Minearbejdere kan spredes ved phishing-e-mails, der sendes i bulk på en SPAM-lignende måde og er afhængige af socialtekniske teknikker for at forvirre de syge lige til at tro, at de har fået en besked fra en legitim løsning eller virksomhed. Infektionsfilerne kan enten forbindes direkte eller placeres i kropsindholdet i multimedie-webindhold eller meddelelseslink.
De dårlige fyre kan desuden udvikle skadelige touchdown-websider, der kan udgøre download og installation af websider, softwareprograms downloadwebsteder samt andre steder, der regelmæssigt åbnes. Når de bruger lignende tilsyneladende domæne til velrenommerede adresser og også sikkerheds- og sikkerhedscertifikater, kan brugerne blive skubbet til at oprette forbindelse til dem. Nogle gange kan bare åbning af dem udløse minerinfektionen.
En anden tilgang ville helt sikkert være at bruge trækbærere, der kan spredes ved hjælp af ovennævnte metoder eller ved hjælp af datadelingsnetværk, BitTorrent er en af en af de mest foretrukne dem. Det bruges regelmæssigt til at distribuere både ægte softwareprogram og dokumenter og også piratindhold. 2 af de mest fremtrædende trækudbydere er følgende:
Andre metoder, der kan tages i betragtning af de kriminelle, består i at bruge webbrowser-kaprere - farlige plugins, der er velegnede til en af de mest populære webbrowsere. De uploades til de relevante arkiver med falske individuelle anmeldelser og også programmørkvalifikationer. Oftentimes oversigter kan omfatte skærmbilleder, videoer samt smarte resuméer, der lover fremragende attributforbedringer og også ydeevneoptimeringer. Ikke desto mindre ved installationen vil vanerne hos de påvirkede internetbrowsere helt sikkert ændre sig- brugerne vil helt sikkert opdage, at de omdirigeres til en hackerstyret touchdown-side, og også deres opsætninger kan blive ændret – standard startside, online søgemaskine og nye faner webside.

Vcc2.exe: Analyse
Vcc2.exe-malware er et tidløst tilfælde af en cryptocurrency minearbejder, som afhængigt af dens konfiguration kan udløse en bred vifte af usikre aktiviteter. Dets hovedmål er at udføre komplicerede matematiske opgaver, der gør brug af de let tilgængelige systemkilder: CPU, GPU, hukommelse og også harddisk område. Den måde, de fungerer på, er ved at oprette forbindelse til en unik server kaldet minedrift, hvor den opfordrede kode downloades og installeres. Så snart et af jobene er downloadet, startes det helt sikkert samtidigt, talrige tilfælde kan være væk, når. Når en given opgave er færdig, vil en helt sikkert blive downloadet på dens placering, og sløjfen fortsætter også, indtil computeren er slukket, infektionen fået fjernet eller en ekstra sammenlignelig lejlighed opstår. Cryptocurrency vil blive tildelt de kriminelle controllere (hacking gruppe eller en ensom cyberpunk) direkte til deres punge.
En usikker attribut for denne kategori af malware er, at eksempler som denne kan tage alle systemkilder og også praktisk talt gøre den lidende computersystem ubrugeligt, indtil faren er helt fjernet. De fleste af dem inkluderer en ensartet rate, der gør dem virkelig svære at slippe af med. Disse kommandoer vil helt sikkert foretage ændringer også alternativer, arrangementsdokumenter og Windows-registreringsværdier, der helt sikkert vil få Vcc2.exe-malware til at starte med det samme, når computersystemet er tændt. Adgang til helbredende menuer og også alternativer kan være blokeret, hvilket giver flere praktiske eliminationsvejledninger praktisk talt ineffektive.
Denne særlige infektion vil bestemt oprette en Windows-løsning til sig selv, overholdelse af den udførte sikkerhedsanalyse, hvor der er observeret overholdelse af aktiviteter:
. Under minearbejderprocedurerne kan den tilknyttede malware oprette forbindelse til allerede kørende Windows-tjenester såvel som tredjepartsmonterede applikationer. Ved at gøre dette bemærker systemadministratorerne muligvis ikke, at ressourcebelastningen kommer fra en anden proces.
| Navn | Vcc2.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware for at opdage og fjerne Vcc2.exe |

Denne form for malware-infektioner er specifikt effektive til at udføre avancerede kommandoer, hvis de er konfigureret således. De er baseret på en modulær struktur, der tillader de kriminelle kontrollere at styre alle former for farlige vaner. Blandt de populære eksempler er ændringen af Windows-registreringsdatabasen – justeringsstrenge forbundet med operativsystemet kan skabe betydelige effektivitetsforstyrrelser og også manglende tilgængelighed Windows-løsninger. Afhængigt af omfanget af ændringer kan det ligeledes gøre computeren helt meningsløs. På den anden side kan manipulation af registreringsværdier, der hører til tredjeparts opsatte applikationer, sabotere dem. Nogle applikationer kan komme til kort at starte helt, mens andre uventet kan stoppe med at arbejde.
Denne specifikke minearbejder i sin nuværende version er koncentreret om minedrift af Monero-kryptovalutaen, der indeholder en tilpasset version af XMRig CPU-minedriftmotoren. Hvis kampagnerne viser sig effektive, kan fremtidige versioner af Vcc2.exe frigives i fremtiden. Da malware bruger software ansøgning susceptabilities at forurene mål værter, det kan være bestanddel af en usikker co-infektion med ransomware og trojanske heste.
Fjernelse af Vcc2.exe anbefales kraftigt, fordi du ikke kun risikerer en enorm elektrisk energiudgift, hvis den fungerer på din pc, men minearbejderen kan desuden udføre andre uønskede opgaver på den såvel som endda skade din pc fuldstændigt.
Vcc2.exe fjernelsesproces
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” knap for at fjerne Vcc2.exe
TRIN 5. Vcc2.exe fjernet!
Video guide: Sådan bruges GridinSoft Anti-Malware til at fjerne Vcc2.exe
Hvordan undgår din pc fra at blive inficeret med “Vcc2.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Vcc2.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Vcc2.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Vcc2.exe”.







