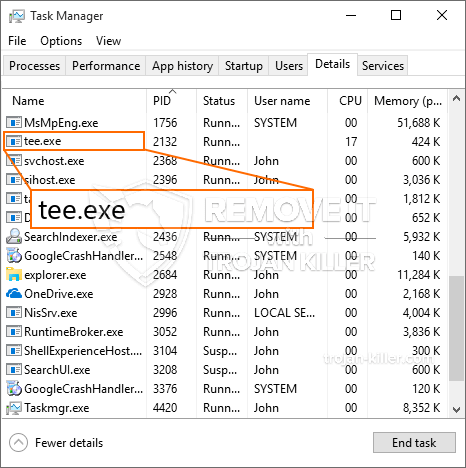
En ny, virkelig farligt cryptocurrency minearbejder infektion rent faktisk er blevet spottet af sikkerhedsmæssige forskere. den malware, hedder Tee.exe kan forurene målofre ved hjælp af en række forskellige måder. Essensen bag Tee.exe-minearbejderen er at udnytte cryptocurrency-minearbejderopgaver på målsystemers computersystemer for at opnå Monero-symboler til syge udgifter. The result of this miner is the elevated electrical energy costs as well as if you leave it for longer time periods Tee.exe may also harm your computers elements.
Tee.exe: distributionssystemer Metoder
Det Tee.exe malware uses two preferred methods which are made use of to contaminate computer system targets:
- Nyttelast Levering ved hjælp af kendte Infektioner. If an older Tee.exe malware is deployed on the victim systems it can automatically update itself or download and install a newer version. This is possible via the built-in upgrade command which obtains the release. Dette gøres ved at forbinde til en bestemt foruddefineret hacker-kontrollerede server, som leverer malware kode. The downloaded and install virus will certainly acquire the name of a Windows solution and be put in the “%systemet% temp” Beliggenhed. Crucial homes as well as operating system configuration documents are altered in order to allow a persistent and also silent infection.
- Software Application sårbarhed udnytter. The latest variation of the Tee.exe malware have been discovered to be brought on by the some ventures, bredt anerkendt for at blive brugt i strejke om ransomware. Infektionerne er færdig ved at målrette åbne tjenester ved hjælp af TCP port. Angrebene er automatiseret af en hacker-kontrollerede rammer, der søger ud af, om porten er åben. If this condition is satisfied it will check the solution and also recover information about it, herunder enhver form for variation og også arrangementdata. Exploits and also preferred username as well as password combinations may be done. When the exploit is triggered against the vulnerable code the miner will certainly be released together with the backdoor. Dette vil give den en dobbelt infektion.
Apart from these techniques other strategies can be used as well. Miners can be distributed by phishing emails that are sent wholesale in a SPAM-like manner and rely on social design tricks in order to perplex the sufferers right into believing that they have received a message from a legit service or company. The infection files can be either straight connected or inserted in the body materials in multimedia web content or text links.
The bad guys can likewise create harmful touchdown pages that can pose supplier download web pages, software application download portals and also other regularly accessed locations. When they make use of comparable seeming domain to reputable addresses and also safety and security certifications the customers might be coerced into engaging with them. Nogle gange blot at åbne dem kan forårsage minearbejder infektion.
Another strategy would be to make use of payload carriers that can be spread out utilizing those techniques or using data sharing networks, BitTorrent er blot en af en af de mest populære dem. It is regularly utilized to disperse both genuine software application as well as documents as well as pirate material. 2 af en af de mest foretrukne haul bærere er følgende:
Other techniques that can be considered by the bad guys include making use of web browser hijackers -harmful plugins which are made suitable with one of the most preferred internet browsers. They are uploaded to the appropriate repositories with fake individual reviews as well as programmer credentials. I mange tilfælde resuméerne kan omfatte skærmbilleder, video clips and sophisticated summaries promising wonderful feature enhancements and performance optimizations. However upon installment the actions of the influenced web browsers will certainly transform- users will certainly discover that they will be rerouted to a hacker-controlled touchdown web page and their setups could be changed – standard startside, søgemaskine på internettet samt nye faner webside.
Tee.exe: Analyse
The Tee.exe malware is a traditional instance of a cryptocurrency miner which depending on its configuration can trigger a wide variety of unsafe actions. Its main objective is to carry out complicated mathematical tasks that will take advantage of the offered system sources: CPU, GPU, hukommelse og også plads på harddisken. The method they operate is by linking to an unique server called mining pool from where the required code is downloaded. Så hurtigt som et af jobene er downloadet, vil det helt sikkert blive startet samtidigt, multiple instances can be gone for when. When an offered task is finished another one will certainly be downloaded in its location as well as the loophole will proceed until the computer system is powered off, the infection is gotten rid of or an additional similar event takes place. Cryptocurrency vil blive belønnet for de kriminelle controllere (hacking gruppe eller en enkelt hacker) direkte til deres tegnebøger.
A hazardous attribute of this category of malware is that samples such as this one can take all system sources and also almost make the sufferer computer pointless till the danger has been entirely gotten rid of. A lot of them feature a relentless setup that makes them really tough to eliminate. Disse kommandoer vil helt sikkert foretage justeringer også alternativer, configuration data and Windows Registry values that will certainly make the Tee.exe malware start automatically once the computer system is powered on. Access to recovery food selections and also options may be obstructed which provides lots of hands-on elimination guides virtually worthless.
Denne vis infektion vil konfigurationshåndtering en Windows løsning for sig selv, adhering to the performed security evaluation ther adhering to actions have been observed:
. During the miner procedures the connected malware can hook up to already running Windows solutions and third-party set up applications. By doing so the system managers might not observe that the resource lots originates from a different procedure.
| Navn | Tee.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove Tee.exe |
id =”82224″ align =”aligncenter” width =”600″] Tee.exe
Tee.exe
Denne type malware-infektioner er specifikt pålidelige til at udføre innovative kommandoer, hvis de er konfigureret sådan. De er baseret på en modulopbygget struktur, der tillader de kriminelle kontrollører at orkestrere alle typer af farlige vaner. Et af de fremtrædende tilfælde er ændringen af Windows-registreringsdatabasen – ændringer strenge relateret til operativsystemet kan forårsage alvorlige forstyrrelser i effektiviteten og også manglen på tilgængelighed Windows-tjenester. At stole på omfanget af justeringer kan det også gøre computersystemet helt ubrugeligt. På den anden side kan kontrol af registerværdier, der kommer fra alle tredjepartsmonterede applikationer, undergrave dem. Nogle applikationer kan muligvis ikke frigive helt, mens andre uventet kan stoppe med at arbejde.
Denne særlige miner i sin nuværende version er fokuseret på at udvinde Monero cryptocurrency med en ændret variation af XMRig CPU-minedriftmotor. If the campaigns prove effective after that future variations of the Tee.exe can be released in the future. Da de malware gør brug af software program sårbarheder til at inficere target værter, det kan være en del af en usikker co-infektion med ransomware samt trojanske heste.
Removal of Tee.exe is highly recommended, i betragtning af at du tager chancen for ikke kun en stor el-udgift, hvis den kører på din pc, endnu kan miner også gøre forskellige andre uønskede aktiviteter på den samt skade din pc fuldstændigt.
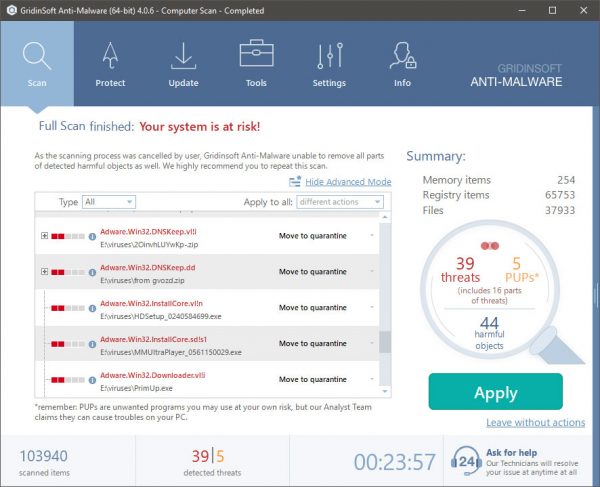
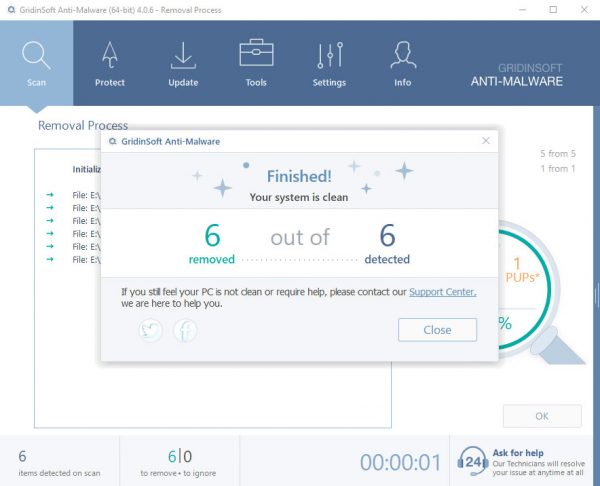
Tee.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
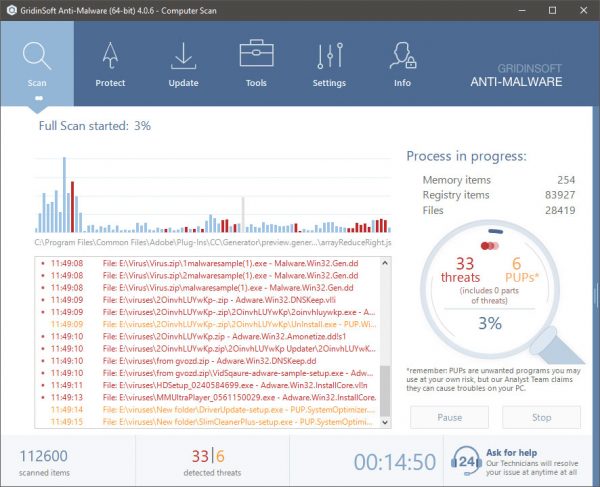
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove Tee.exe
TRIN 5. Tee.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove Tee.exe
Hvordan undgår din pc fra at blive inficeret med “Tee.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Tee.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Tee.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Tee.exe”.