Et helt nyt, meget farlig kryptovaluta minearbejder er faktisk blevet opdaget af sikkerhedsforskere. den malware, hedder Deftesrg.exe kan forurene målpatienter ved hjælp af forskellige metoder. The main idea behind the Deftesrg.exe miner is to utilize cryptocurrency miner tasks on the computers of victims in order to acquire Monero symbols at victims cost. The end result of this miner is the elevated electrical energy expenses and also if you leave it for longer time periods Deftesrg.exe might also harm your computers components.
Deftesrg.exe: distributionssystemer Metoder
Det Deftesrg.exe malware makes use of two prominent methods which are utilized to infect computer targets:
- Payload Levering gennem Prior Infektioner. If an older Deftesrg.exe malware is released on the sufferer systems it can automatically upgrade itself or download and install a newer version. Dette er muligt ved hjælp af den integrerede opdatering kommando, som opnår lanceringen. Dette gøres ved at tilknytte en bestemt foruddefineret hacker-styret server, der giver malware-koden. The downloaded and install virus will obtain the name of a Windows service as well as be placed in the “%systemet% temp” areal. Essential buildings and running system configuration data are changed in order to allow a persistent and silent infection.
- Software sårbarhed udnytter. The newest version of the Deftesrg.exe malware have been found to be brought on by the some ventures, berømt anerkendt for at blive gjort brug af i de ransomware overfald. Infektionerne er færdig ved at målrette åbne løsninger ved hjælp af TCP port. De overgreb er automatiseret af en hacker-kontrollerede rammer, som ser op, hvis porten er åben. If this problem is fulfilled it will check the solution as well as get details about it, including any type of version and setup data. Ventures og foretrukne brugernavne og også adgangskodekombinationer kan udføres. When the make use of is triggered against the susceptible code the miner will certainly be deployed in addition to the backdoor. Dette vil præsentere en dobbelt infektion.
Ud over disse tilgange kan andre metoder også anvendes. Miners can be distributed by phishing emails that are sent in bulk in a SPAM-like way as well as depend upon social engineering tricks in order to confuse the victims into believing that they have obtained a message from a legit service or company. The infection documents can be either directly affixed or inserted in the body components in multimedia web content or message links.
The bad guys can also develop malicious landing pages that can impersonate supplier download and install web pages, software download sites and also other regularly accessed areas. When they utilize similar appearing domain names to reputable addresses and also protection certifications the users might be persuaded right into engaging with them. Sometimes just opening them can cause the miner infection.
One more technique would certainly be to make use of haul carriers that can be spread out using the above-mentioned approaches or via documents sharing networks, BitTorrent er blandt de mest foretrukne dem. It is regularly utilized to distribute both legitimate software as well as documents and also pirate material. 2 af en af de mest populære nyttelastbærere er følgende:
Other techniques that can be considered by the crooks include the use of internet browser hijackers -hazardous plugins which are made compatible with one of the most popular web browsers. They are posted to the pertinent databases with phony customer testimonials and also programmer credentials. I mange tilfælde beskrivelserne kan bestå af skærmbilleder, videos as well as sophisticated summaries encouraging great feature improvements as well as performance optimizations. Nonetheless upon setup the behavior of the affected internet browsers will change- brugere vil opdage, at de helt sikkert vil blive omdirigeret til en hacker-styret touchdown-webside, og deres indstillinger kan også ændres – standard webside, søgemaskine samt helt nye faner webside.
Deftesrg.exe: Analyse
The Deftesrg.exe malware is a timeless case of a cryptocurrency miner which relying on its arrangement can cause a wide variety of hazardous activities. Its main goal is to do complex mathematical tasks that will make use of the readily available system resources: CPU, GPU, hukommelse og harddisk område. The method they work is by linking to an unique server called mining pool where the needed code is downloaded and install. As quickly as one of the jobs is downloaded it will certainly be started at the same time, flere forekomster kan køre på, så snart. When a provided task is completed one more one will be downloaded and install in its place and the loophole will continue until the computer system is powered off, infektionen fået fjernet eller en mere sammenlignelige begivenhed finder sted. Cryptocurrency vil blive kompenseret for de kriminelle controllere (hacking team eller en enkelt hacker) direkte til deres tegnebøger.
A harmful feature of this classification of malware is that examples similar to this one can take all system resources and practically make the target computer system unusable up until the hazard has actually been totally removed. De fleste af dem inkluderer en vedvarende installation, som gør dem faktisk udfordrende at slippe af med. Disse kommandoer vil foretage ændringer også valg, setup documents and also Windows Registry values that will certainly make the Deftesrg.exe malware begin automatically when the computer system is powered on. Access to healing food selections and options may be blocked which provides several hand-operated removal overviews virtually useless.
Denne bestemte infektion vil bestemt arrangere en Windows-tjeneste for sig selv, complying with the conducted safety analysis ther adhering to activities have actually been observed:
. During the miner procedures the associated malware can link to already running Windows services as well as third-party mounted applications. By doing so the system managers might not discover that the resource load comes from a separate procedure.
| Navn | Deftesrg.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove Deftesrg.exe |
id =”81135″ align =”aligncenter” width =”600″] Deftesrg.exe
Deftesrg.exe
Denne type malwareinfektioner er særligt effektiv til at udføre innovative kommandoer, hvis konfigureret således. De er baseret på en modulær struktur gør det muligt for de kriminelle controllere at orkestrere alle slags farlig adfærd. Blandt de populære eksempler er ændringen af registreringsdatabasen i Windows – modifikationer strenge forbundet af OS kan forårsage alvorlige forstyrrelser ydeevne samt den manglende adgang til Windows-løsninger. Afhængig af omfanget af tilpasninger, som den kan også gøre computeren helt ubrugelig. På den anden side kontrol af Registry worths kommer fra enhver form for tredjepart monteret programmer kan underminere dem. Nogle programmer kan falde kort at introducere helt, mens andre uventet kan stoppe med at arbejde.
Denne vis minearbejder i sin nuværende variation er fokuseret på minedrift Monero cryptocurrency har en modificeret variant af XMRig CPU minedrift motor. If the campaigns verify effective then future variations of the Deftesrg.exe can be introduced in the future. Da malware bruger sårbarheder i software til at inficere target værter, det kan være en del af en usikker co-infektion med ransomware og trojanske heste.
Removal of Deftesrg.exe is highly advised, betragtning af, at du risikerer ikke bare en enorm elektrisk strøm regningen, hvis det fungerer på din pc, endnu minearbejder kan ligeledes udføre andre uønskede opgaver på det såvel som endda skade din computer permanent.
Deftesrg.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
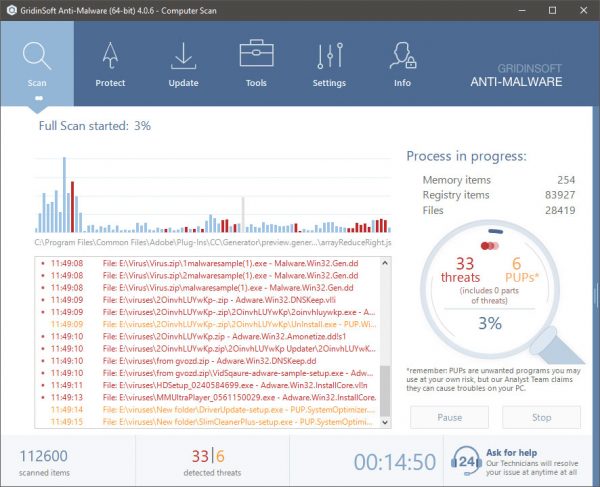
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
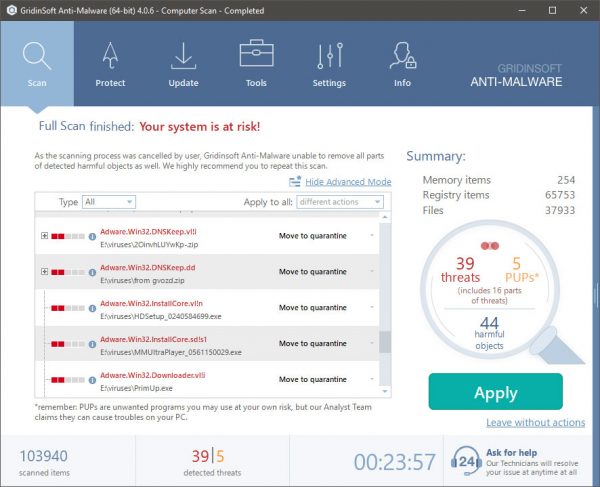
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove Deftesrg.exe
TRIN 5. Deftesrg.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove Deftesrg.exe
Hvordan undgår din pc fra at blive inficeret med “Deftesrg.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Deftesrg.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Deftesrg.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Deftesrg.exe”.