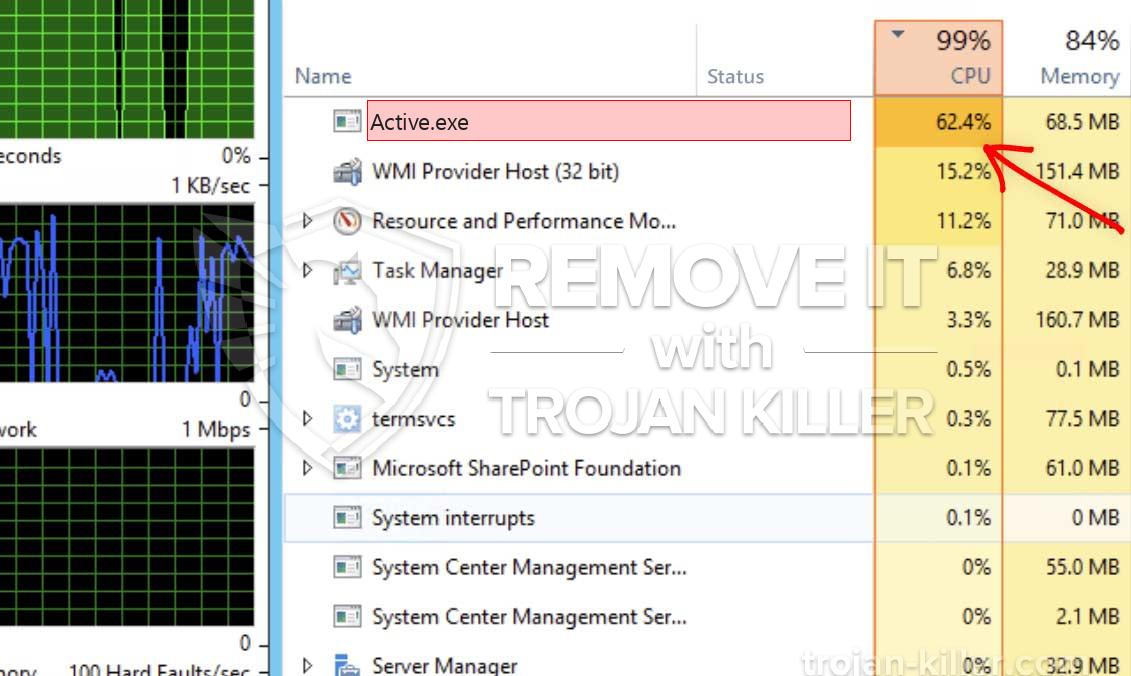
En ny, meget farlig kryptokurrency minearbejder er fundet af sikkerheds- og sikkerhedsforskere. den malware, hedder Active.exe kan forurene ofre mål udnytte en række måder. Essensen bag Active.exe-minearbejderen er at anvende cryptocurrency-minearbejde på ofrenes computersystemer for at få Monero-tokens til ofrene’ bekostning. Resultatet af denne minearbejder er de øgede strømomkostninger, og hvis du forlader den i længere tid, kan Active.exe også beskadige dit computersystems komponenter.
Active.exe: distributionssystemer Metoder
Det Active.exe malware gør brug af to foretrukne tilgange, som bruges til at inficere computermål:
- Payload Levering hjælp Prior Infektioner. Hvis en ældre Active.exe-malware frigives på offerets systemer, kan den øjeblikkeligt opgradere sig selv eller downloade en nyere version. Dette er muligt ved hjælp af den indbyggede opdateringskommando, som henter udgivelsen. Dette gøres ved at linke til en bestemt foruddefineret hacker-kontrollerede server, som tilbyder den malware kode. Den downloadede virus vil helt sikkert få navnet på en Windows-tjeneste og blive placeret i “%systemet% temp” areal. Vigtige egenskaber såvel som kørende systemkonfigurationsfiler ændres for at tillade en ubarmhjertig og også tavs infektion.
- Software Application sårbarhed udnytter. Den seneste variant af Active.exe-malwaren er blevet opdaget at være udløst af nogle ventures, berømt kendt for at blive gjort brug af i de ransomware strikes. Infektionerne er færdig ved at målrette åbne løsninger via TCP port. De overgreb er automatiseret af en hacker-kontrollerede rammer, som ser op, hvis porten er åben. Hvis denne betingelse er opfyldt, vil den helt sikkert kontrollere løsningen og også hente oplysninger om den, herunder enhver form for variation og også konfigurationsdata. Ventures samt fremtrædende brugernavn samt password blandinger kan gøres. Når udnyttelsen er forårsaget af den modtagelige kode, vil minearbejderen helt sikkert blive frigivet sammen med bagdøren. Dette vil helt sikkert give en dobbelt infektion.
Ud over disse metoder kan andre teknikker også bruges. Minearbejdere kan distribueres ved hjælp af phishing-e-mails, der sendes ud i bulk på en SPAM-lignende måde såvel som afhængige af sociale designmetoder for at forvirre ofrene til at tro, at de har fået en besked fra en lovlig løsning eller virksomhed. Infektionsdataene kan enten forbindes direkte eller placeres i kropskomponenterne i multimediewebindhold eller meddelelsesweblinks.
Svindlerne kan også udvikle skadelige landingssider, der kan efterligne leverandørens download- og installationssider, websteder til download af software og også forskellige andre ofte tilgåede steder. Når de bruger et domæne, der kan sammenlignes med legitime adresser og også beskyttelsescertifikater, kan kunderne blive skubbet direkte til at kommunikere med dem. Nogle gange blot at åbne dem kan aktivere minearbejder infektion.
En yderligere metode ville være at bruge payload-tjenesteudbydere, der kan spredes ud ved at bruge disse tilgange eller via netværk til deling af dokumenter, BitTorrent er blot en af en af de mest foretrukne dem. Det bruges ofte til at sprede både velrenommeret software samt dokumenter og piratmateriale. To af en af de mest foretrukne haul udbydere er følgende:
Forskellige andre tilgange, der kan overvejes af de onde, inkluderer brug af internetbrowser hijackers - farlige plugins, som er gjort egnede med en af de mest foretrukne webbrowsere. De indsendes til de relevante depoter med falske kundeevalueringer og også designerkvalifikationer. I de fleste tilfælde kan resuméerne indeholde skærmbilleder, videoklip og også omfattende resuméer, der lover store egenskabsforbedringer og ydeevneoptimeringer. Men efter installationen vil handlingerne af de berørte internetbrowsere helt sikkert ændre sig- kunder vil opdage, at de vil blive omdirigeret til en hackerkontrolleret landingswebside, og deres opsætninger kan blive ændret – standard startside, søgemaskine og nye faner webside.

Active.exe: Analyse
Active.exe-malwaren er en traditionel situation for en cryptocurrency-minearbejder, som afhængig af dens opsætning kan forårsage en lang række usikre aktiviteter. Dens hovedmål er at udføre komplekse matematiske opgaver, der vil drage fordel af de let tilgængelige systemressourcer: CPU, GPU, hukommelse og harddiskplads. Den måde, de fungerer, er ved at binde sig til en særlig server kaldet minedrift swimmingpool, hvor den nødvendige kode er downloadet og installere. Så hurtigt som blandt opgaverne bliver downloadet det vil blive påbegyndt på en gang, talrige tilfælde kan køres på en gang. Når en given opgave er færdig, vil en mere helt sikkert blive downloadet på dens placering, ligesom løkken vil fortsætte indtil computersystemet slukkes, infektionen fået fjernet eller sker en anden lignende arrangement. Cryptocurrency vil blive kompenseret for de kriminelle controllere (hacking gruppe eller en ensom cyberpunk) direkte til deres punge.
En skadelig egenskab ved denne kategori af malware er, at prøver svarende til denne kan tage alle systemressourcer samt praktisk talt gøre målcomputersystemet meningsløst, indtil faren er fuldstændig fjernet. De fleste af dem inkluderer en vedvarende opsætning, der gør dem virkelig svære at fjerne. Disse kommandoer foretager ændringer i startindstillinger, arrangementsdokumenter og også Windows Registry-værdier, der vil få Active.exe-malwaren til at starte øjeblikkeligt, når computeren tændes. Adgang til gendannelsesmenuer og muligheder kan være blokeret, hvilket giver mange manuelle fjernelsesoversigter næsten ubrugelige.
Denne særlige infektion konfigurerer en Windows-løsning for sig selv, i overensstemmelse med den udførte beskyttelsesevaluering, er følgende aktiviteter faktisk blevet observeret:
. Under minedriftsprocedurerne kan den tilsluttede malware oprette forbindelse til aktuelt kørende Windows-tjenester og tredjepartsmonterede applikationer. Ved at gøre det kan systemadministratorerne muligvis ikke observere, at kildetons stammer fra en separat procedure.
| Navn | Active.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware for at finde og fjerne Active.exe |
Denne form for malware-infektioner er især pålidelige til at udføre sofistikerede kommandoer, hvis de er konfigureret sådan. De er baseret på en modulær ramme, der gør det muligt for de kriminelle kontroller at koordinere al slags usikker adfærd. Et af de fremtrædende eksempler er ændringen af Windows-registreringsdatabasen – justeringsstrenge forbundet med operativsystemet kan skabe alvorlige effektivitetsforstyrrelser såvel som manglende tilgængelighed til Windows-løsninger. Baseret på omfanget af ændringer kan det desuden gøre computersystemet fuldstændig ubrugeligt. På den anden side kan kontrol af registreringsværdier, der tilhører enhver tredjeparts opsætningsapplikationer, sabotere dem. Nogle programmer holder muligvis op med at fungere for at frigive helt, mens andre pludselig kan holde op med at arbejde.
Denne bestemte minearbejder i sin eksisterende variation er koncentreret om at udvinde Monero-kryptovalutaen, herunder en tilpasset variation af XMRig CPU-minemotoren. Hvis projekterne viser sig effektive, kan fremtidige versioner af Active.exe introduceres i fremtiden. Da malware bruger softwarefølsomhed til at inficere målværter, det kan være en del af en skadelig co-infektion med ransomware og også trojanske heste.
Eliminering af Active.exe anbefales kraftigt, fordi du risikerer ikke kun en stor el-energiudgift, hvis den arbejder på din COMPUTER, dog kan minearbejderen også udføre forskellige andre uønskede opgaver på den samt endda beskadige din COMPUTER permanent.
Active.exe fjernelsesproces
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” knappen for at fjerne Active.exe
TRIN 5. Active.exe er fjernet!
Video guide: Sådan bruger du GridinSoft Anti-Malware til at fjerne Active.exe
Hvordan undgår din pc fra at blive inficeret med “Active.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Active.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Active.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Active.exe”.







