En ny, meget usikker kryptokurrency-minearbejder er faktisk blevet set af sikkerhedsforskere. den malware, hedder Acnom.exe kan forurene målsyge ved brug af en række midler. Essensen bag Acnom.exe-minearbejderen er at udnytte cryptocurrency-minearbejderopgaver på ofrenes computere for at opnå Monero-tokens til måludgifter. The outcome of this miner is the elevated electricity expenses and also if you leave it for longer time periods Acnom.exe might even harm your computers components.
Acnom.exe: distributionssystemer Metoder
Det Acnom.exe malware udnytter 2 popular approaches which are used to infect computer system targets:
- Nyttelast Levering ved hjælp af kendte Infektioner. If an older Acnom.exe malware is deployed on the victim systems it can instantly upgrade itself or download and install a newer variation. Dette er muligt ved hjælp af den indbyggede opgraderingskommando, der får lanceringen. Dette gøres ved at forbinde til en bestemt foruddefineret hacker-kontrollerede server, der tilvejebringer den Malwarekoden. The downloaded and install infection will acquire the name of a Windows service and be positioned in the “%systemet% temp” Beliggenhed. Crucial buildings and operating system setup files are altered in order to allow a persistent and silent infection.
- Software Application sårbarhed udnytter. The most recent variation of the Acnom.exe malware have been discovered to be brought on by the some exploits, berømt anerkendt for at blive brugt i ransomware-angreb. Infektionerne er færdig ved at målrette åbne løsninger gennem TCP port. Angrebene er automatiseret af en hacker-kontrollerede rammer, der søger ud af, om porten er åben. If this condition is satisfied it will certainly scan the solution as well as retrieve info regarding it, consisting of any kind of version and configuration data. Exploits and popular username and also password mixes might be done. Når exploit aktiveres versus tilbøjelige kode minearbejderen vil bestemt frigives sammen med bagdør. Dette vil helt sikkert præsentere en dobbelt infektion.
Aside from these techniques various other techniques can be used too. Miners can be dispersed by phishing e-mails that are sent out in bulk in a SPAM-like fashion and also depend upon social engineering methods in order to perplex the victims right into thinking that they have actually obtained a message from a reputable solution or business. The infection data can be either directly affixed or inserted in the body contents in multimedia web content or message web links.
The bad guys can additionally create malicious touchdown web pages that can pose supplier download and install web pages, software application download sites as well as other frequently accessed places. When they make use of comparable appearing domain to legit addresses as well as security certifications the individuals might be coerced right into engaging with them. I mange tilfælde kan bare åbning af dem udløse minerinfektionen.
An additional strategy would be to use haul carriers that can be spread utilizing those techniques or via file sharing networks, BitTorrent er blot en af de mest populære. It is often used to distribute both legitimate software program and also files as well as pirate material. To af en af de mest populære distancer udbydere er følgende:
Other approaches that can be thought about by the criminals consist of making use of web browser hijackers -dangerous plugins which are made suitable with the most preferred internet browsers. They are submitted to the appropriate repositories with phony user evaluations and also developer credentials. Oftentimes oversigter kan omfatte skærmbilleder, video clips and elaborate descriptions appealing fantastic feature improvements as well as efficiency optimizations. Nonetheless upon installment the behavior of the impacted browsers will certainly transform- users will discover that they will be redirected to a hacker-controlled touchdown web page and also their setups could be altered – standard webside, internetsøgemaskine samt ny faneblad.
Acnom.exe: Analyse
The Acnom.exe malware is a classic instance of a cryptocurrency miner which relying on its arrangement can trigger a wide range of unsafe actions. Its main goal is to do complicated mathematical tasks that will benefit from the offered system sources: CPU, GPU, hukommelse og også harddiskplads. The method they work is by attaching to an unique web server called mining pool where the needed code is downloaded and install. Så hurtigt som en af opgaverne er hentet det vil helt sikkert blive startet samtidigt, flere tilfælde kan være væk for hvornår. When a provided task is completed an additional one will be downloaded and install in its place and also the loop will proceed up until the computer system is powered off, the infection is removed or another similar occasion happens. Cryptocurrency vil blive belønnet for de kriminelle controllere (hacking gruppe eller en enkelt cyberpunk) direkte til deres tegnebøger.
A hazardous characteristic of this classification of malware is that samples similar to this one can take all system resources as well as practically make the sufferer computer unusable until the danger has been totally gotten rid of. A lot of them feature a consistent installation which makes them actually hard to get rid of. Disse kommandoer vil helt sikkert foretage ændringer også alternativer, arrangement files and also Windows Registry values that will make the Acnom.exe malware start immediately when the computer system is powered on. Accessibility to recuperation food selections and choices may be obstructed which provides lots of manual elimination overviews practically useless.
Denne vis infektion vil helt sikkert arrangement en Windows løsning for sig selv, complying with the performed safety analysis ther adhering to actions have actually been observed:
. During the miner procedures the associated malware can attach to already running Windows services and also third-party mounted applications. By doing so the system managers may not notice that the source lots comes from a separate procedure.
| Navn | Acnom.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove Acnom.exe |
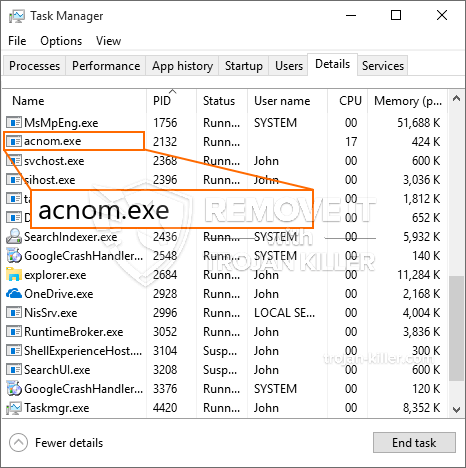
id =”83276″ align =”aligncenter” width =”600″]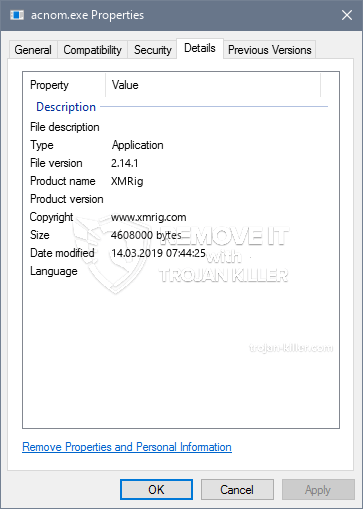 Acnom.exe
Acnom.exe
Denne type malware-infektioner er specifikt pålidelige til at udføre innovative kommandoer, hvis de er konfigureret sådan. They are based upon a modular structure permitting the criminal controllers to orchestrate all kinds of hazardous habits. Blandt de foretrukne tilfælde er justeringen af Windows-registreringsdatabasen – modifications strings connected by the operating system can cause significant efficiency disruptions and also the failure to accessibility Windows solutions. Depending upon the extent of modifications it can also make the computer system completely unusable. På den anden side kan manipulation af registreringsværdier, der tilhører enhver form for tredjeparts installerede applikationer, sabotere dem. Some applications might stop working to launch entirely while others can suddenly quit working.
This specific miner in its current variation is concentrated on mining the Monero cryptocurrency consisting of a changed variation of XMRig CPU mining engine. If the campaigns show effective after that future versions of the Acnom.exe can be launched in the future. Da malware bruger softwaresårbarheder til at inficere målværter, det kan være en del af en skadelig co-infektion med ransomware og trojanere.
Elimination of Acnom.exe is strongly recommended, since you take the chance of not just a big electricity bill if it is working on your COMPUTER, however the miner might likewise execute other unwanted tasks on it as well as even harm your PC completely.
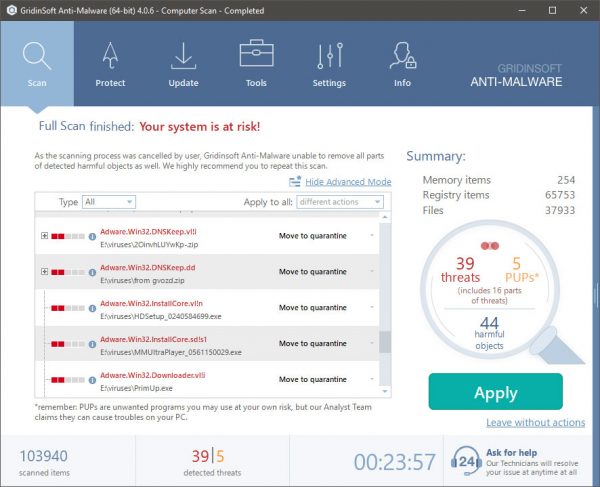
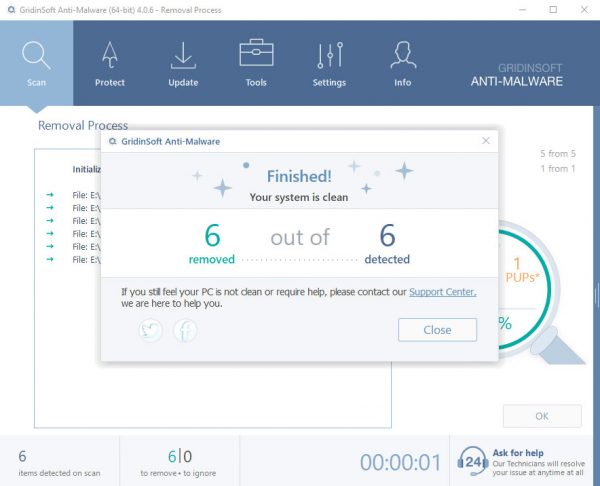
Acnom.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove Acnom.exe
TRIN 5. Acnom.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove Acnom.exe
Hvordan undgår din pc fra at blive inficeret med “Acnom.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Acnom.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Acnom.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Acnom.exe”.