ativsk.exe miner is a kind of malicious software. It aims to steal user’s finance. It haunts such digital currencies as Bitcoin, Monero, DarkNetCoin, and others. You start suffer from this kind of threat in case of computer infection. Thus, particular anti-malware utilities will be in demanding. To keep your money safe, you will have to reconsider your online actions and take care of security level. Meet the most obvious ways of penetration. Let’s make a quick check your computer has an appropriate anti-virus.
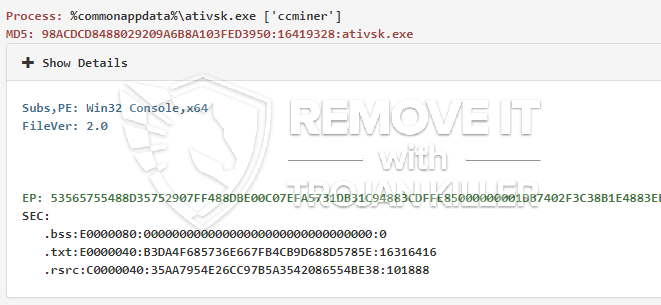 ativsk.exe
ativsk.exeativsk.exe Trojan doesn’t waste time and turns infected computer into the robot for Bitcoin mining. Such activities remain secret for users, but the computer suffers greatly. The main targets are graphic and central processors that loses their power in favor of malicious absorber. That is why CPU usage becomes abnormal, computer freezes too often and the normal online and offline routine becomes impossible.
Keep in mind the fact that ativsk.exe Miner finds pretty well so it’s better to prevent its appearance than find the ways of its removal. You can increase the level of computer’s protection if you pay attention to own online behavior. Do not click on suspicious links, delete messages from unknown users unread, mind the installation process. Especially, be careful with download as most Trojans, viruses, adware and others come inside the system as bundled tool to free software. That is a possible way how ativsk.exe Miner could appear on your computer. However, we do not exclude the penetration due to leaks in the defense such as outdated databases. That is why attackers managed to inject Trojan inside the system.
If you are still not sure that ativsk.exe infected your system, check next symptoms:
- CPU and graphic cards lose efficiency.
- A great number of pop-ups appear on the screen.
- Your sensitive information takes place in weird places.
- PC upsets you with its work.
ativsk.exe automatic removal tool:
Viruses, trojans and other malicious software are widespread nowadays. Gridinsoft company offers a great solution for all problems, which can be caused by malware, including the free scanner, virus remover and Reset Browser Settings tool to clean all popular browsers from ads, pop-ups, and redirects. In this guide, we will explain how to use GridinSoft Anti-Malware to clean your system and keep it safe from threats in future.
ativsk.exe removal steps:
- Download GridinSoft Anti-Malware and scan your computer with it.
- Click on “Fix Now” to remove all infections found after the scan is completed:
- Shut down all your available browsers.
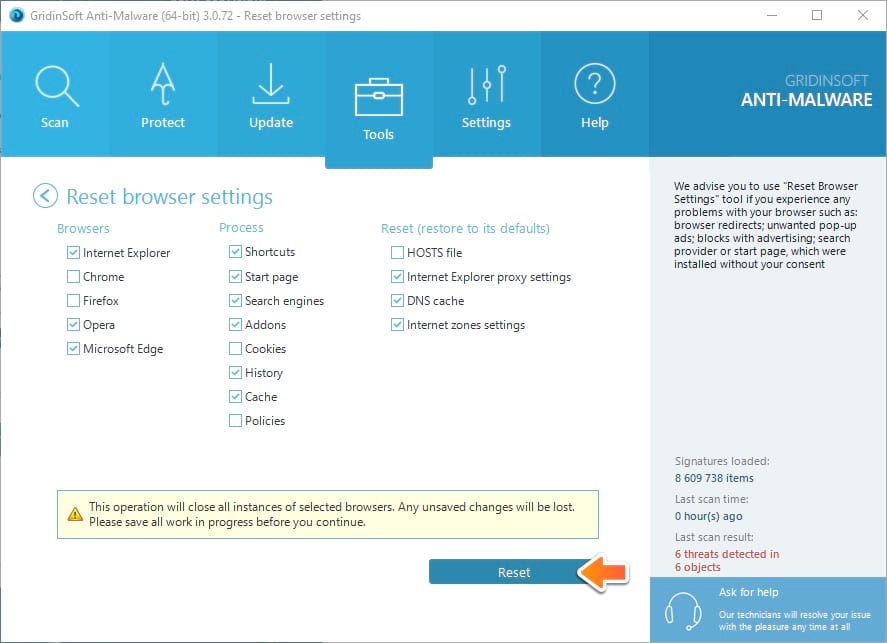
- In GridinSoft Anti-Malware click on “Tools” and then on “Reset browser settings“:
- Follow the instructions, select browsers you need to be reset, and click on “Reset” button. Finally, restart your computer to apply all made changes.
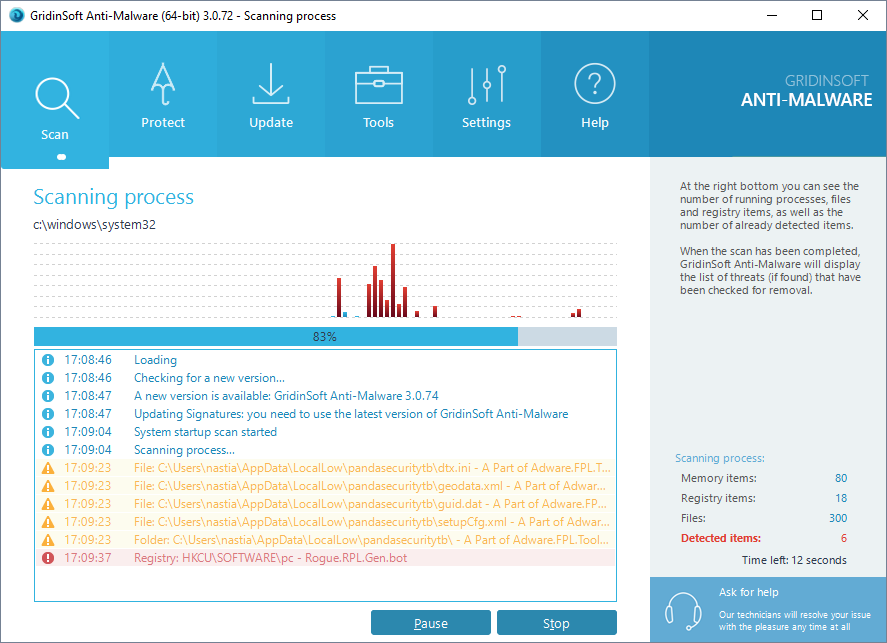
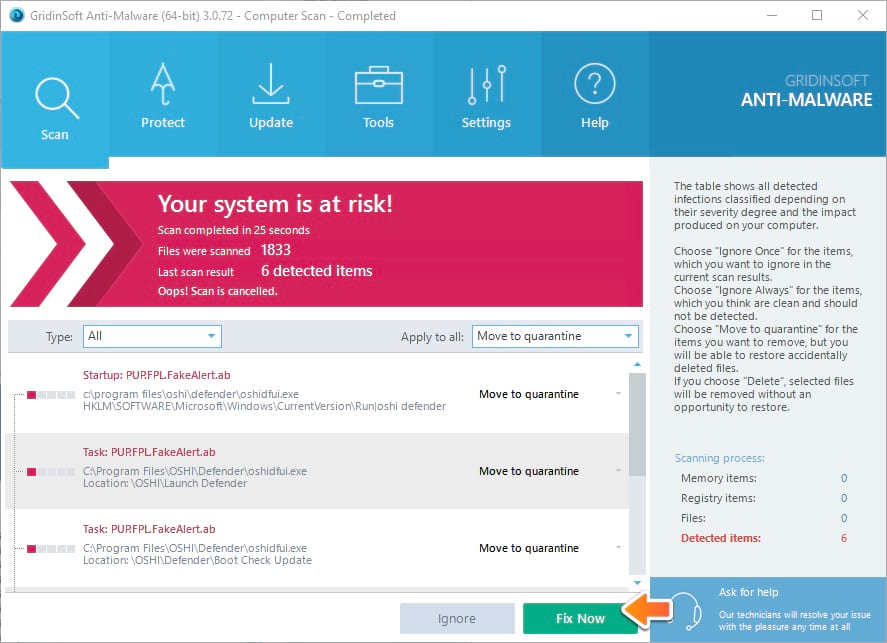 GridinSoft Anti-Malware Scan Results
GridinSoft Anti-Malware Scan Results
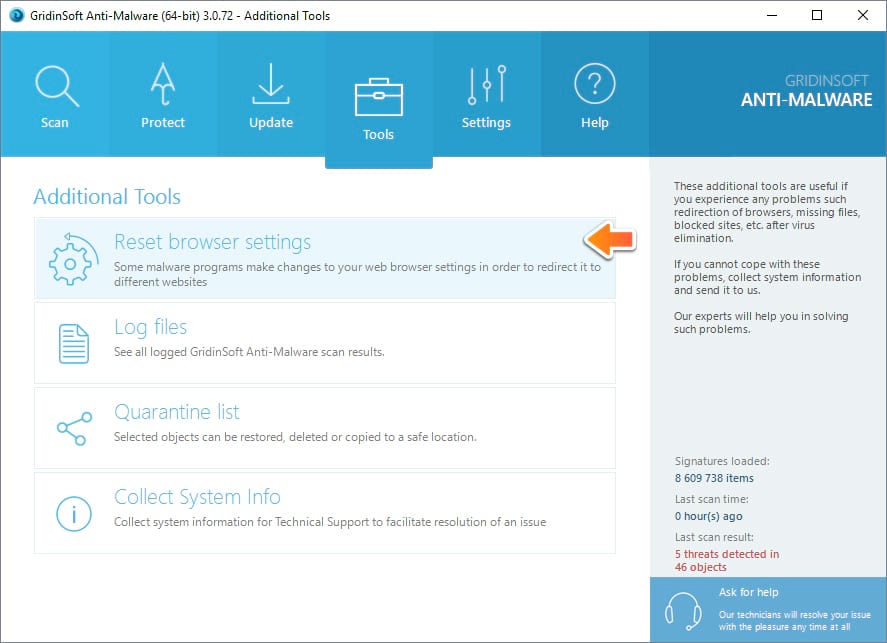 GridinSoft Anti-Malware tools tab
GridinSoft Anti-Malware tools tab
Prevent your system from being reinfected with ativsk.exe in the future
GridinSoft Anti-Malware offers excellent solution which may help to prevent your system from being contaminated with malware ahead of time. This feature is referred to as “Real-Time Protection”. By default, it is disabled once you install the software. To enable it, please click on “Protect” button and then “Start“:
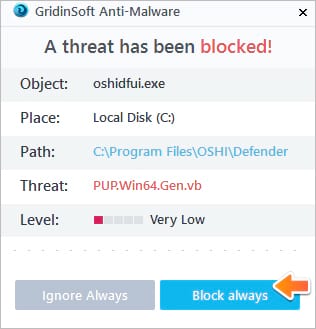
This options helps you to prevent execution of malicious programs and to avoid their installation ahead of time. When certain malware tries to install itself into your system, GridinSoft Anti-Malware and its Real-Time Protection module will terminate this installation attempt ahead of time. You may click on “Confirm” button to continue blocking this malicious program, or to select “Ignore this file” and allow the malicious application to be installed (at your own risk):