What is Xmr.exe virus?
Xmr.exe can properly be determined as coin miner. It is a virus that enters your computer and uses its hardware to get cryptocurrencies. Although this virus generates undesirable impacts on your system productivity, it also can cause various hardware breakdowns. But first things first, let’s find out all the details regarding the Xmr.exe miner, and after that see how to remove it from your computer. You must know your enemy’s face!
Xmr.exe coin miner effects
The common sign for all coin miners is system slowdown, and Xmr.exe is not an exclusion. This type of malware squeezes out the max capacity of your PC capacity, leaving you just 5-10% of max power. You can spectate it in the Task Manager: a single process consumes at least 80% of both CPU and GPU capability. It is not possible to say about the amount of revenue these fraudsters have, because the low hashrate is compensated by a massive amount of PCs that are used in this operation.
*variative-pic-NAME-miner-in-taskmgr*
Sure, the general sluggishness of your personal computer is not a 100% sign. In some cases, the CPU is loaded due to read/write operations failure. In those instances, the CPU is trying to perform the writing procedure, for example, for several times, until succeeded. Nevertheless, the disk problems additionally produce a load on the disk, which is not usual for coin miners. It is much better to arrange the processes by their CPU/GPU utilization, and after that check the appeared checklist for possible unknown processes.
Malware summary
| Type | Trojan Coin Miner |
| Name | Xmr.exe |
| Effects | Extremely high CPU/GPU load; possibly, the hardware failure |
| Spreading | Malvertising, applications from untrustworthy websites |
| Danger level | High |
| Removal tool | GridinSoft Anti-Malware |
How did I get the Xmr.exe virus?
Coin miners are one of the most wide-spread kinds of trojans. While spyware, stealers and also backdoors are typically spread as a part of a malware pack – together with one of the aforementioned types, or with ransomware, for example – coin miners are normally solitary. For this reason, their distribution ways are also different from ones used by various other trojan viruses.
Among the most widespread tactics for the Xmr.exe coin miner is malvertising on the internet. The precise way of how the malicious banner is shown is not strict – it can be displayed by adware as well as presented on the untrustworthy site. However, most of these banners make an effort to bait you to click it. Those promotions can offer you to install a helpful program on your computer – for example, to enhance your computer efficiency, or to secure the system from malware. Actually, you will not even get the exact app (which is likely unwanted). This malware will likely run in the background and just utilize your CPU and graphic card to calculate the hash of a new block.
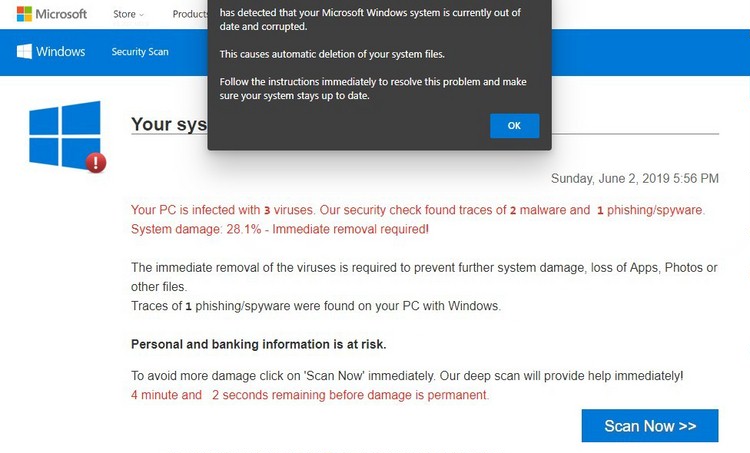
In some cases, your computer may be infected with the Xmr.exe miner after installing the program from unreliable websites. Torrent trackers, like eMule or ThePirateBay, are the referent examples of such websites. Sure, all seedings there are controlled, but prior to the reports concerning the virus in the certain seeding are seen and the specific seeding is investigated, a lot of people can receive the malware on their computers. It is better to use certified apps that does not give you so much risk.
More dangerous and more powerful versions
Several of the coin miners that are active nowadays turned into rather severe globalized malware variants. These versions are the combination of miners and worms, that are able both to mine cryptocurrencies and damage the files/programs you have on your PC. The peculiar element of these viruses is the fact that they focus mostly on Linux and Linux-based web servers. The spreading tactics those miner worms use are following:
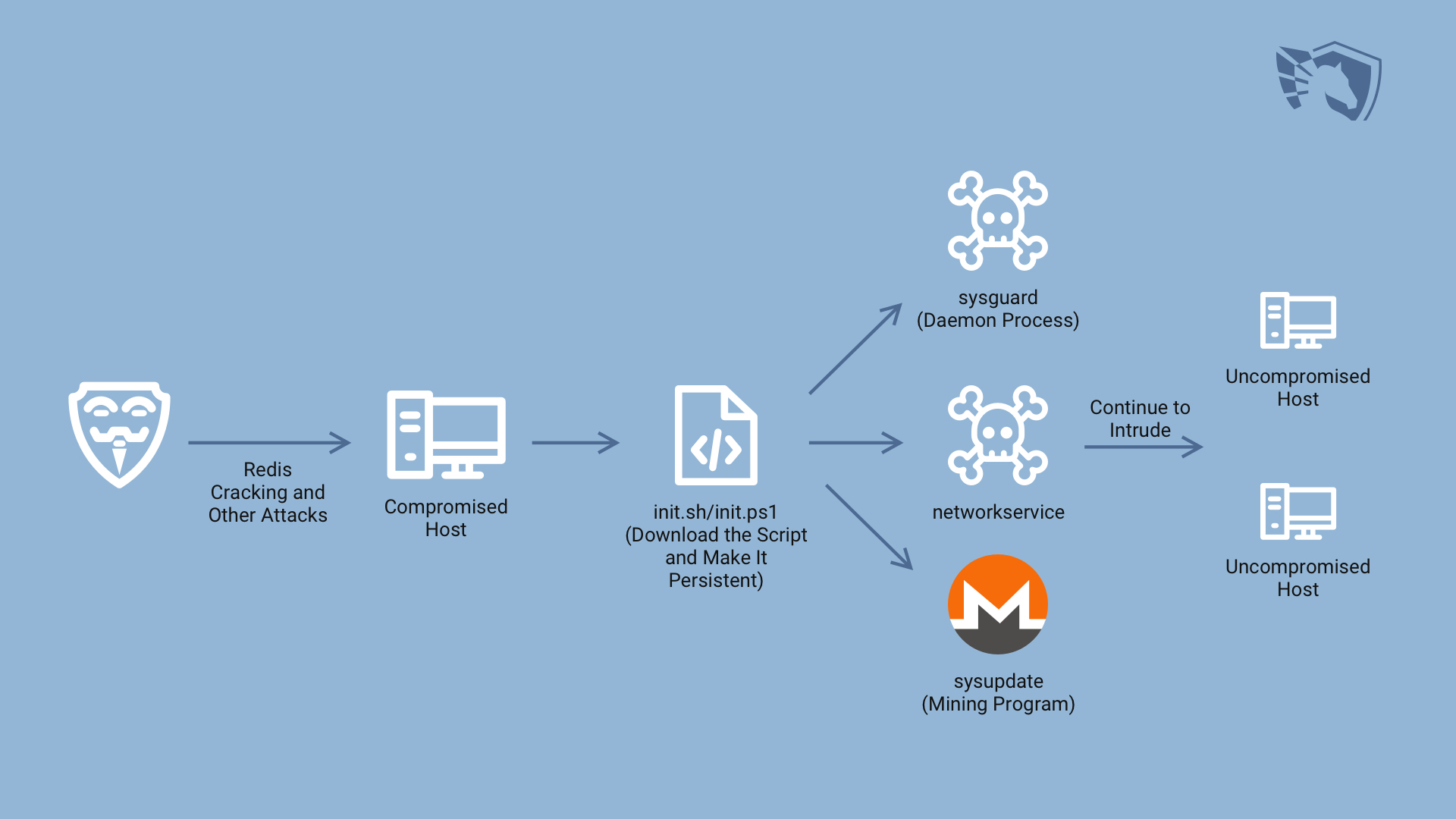
Among the most known, only 3 “renewed” miners are aimed at Windows. Kworkerds, Bulehero and MinerGuard make their profit by attacking not individual computers – they attack networks. This move was most likely spied on ransomware, which transformed their sight on organizations in the same year when those miner worms showed up. But it is much better to stop talking about the minor points and focus on the stuff which is actually important.
| Miner Worm | Injection way |
| CryptoSink | Command execution vulnerability (CVE-2014-3120) on Elasticsearch |
| Bulehero | WannaCrypt vulnerability, Inter-process Communication shares cracking, other web services vulnerabilities |
| 8220 Miner | Web service vulnerabilities that allow unauthorized access |
Short reference
“Cryptocurrency mining” is a term that is used to describe the process of hash calculation. Exactly, hash is calculated for a new transaction block of a certain cryptocurrency. Most of the coin miners prefer to mine Ethereum, DarkCoin, Monero, Solana, or other altcoins. Such a choice is done to speed up the hash calculation: even when the network of infected computers is bigger than several thousand machines, calculating the hash of Bitcoin will take a lot of time. Anyway, this process requires a lot of calculation power, and GPUs fit much better for this target. That’s why the “professional” miners create huge crypto farms that consist of tens and hundreds of graphic cards.
How dangerous is the NAME coin miner?
The primary (and the most noticeable) damages is the inability to use your system in an usual way. Your web browsers struggle to start, animations are lagged, even the Notepad is pretty slow. Making use of such a PC becomes a problem. But the productivity plummence is not the only point that you have to think about.
Considering that your hardware suffers a substantial load, all issues that can possibly appear in such an operation form will likely show up. Initially, hardware is developed to handle their peak performance for a very long time, without any further consequences. However, there are several circumstances where even a brand-new piece of hardware can be damaged by a Xmr.exe miner.
First thing that can harm your PC is heat level. If you have not planned the cooling scheme of your system thoroughly, it is possible to make the parts boiling hot. Definitely, all contemporary CPUs and GPUs have the ability to downclock themselves as the heat level goes too high. However, you have a lot of other elements plugged into your motherboard, that will not like the 80 ° C+ temperature.
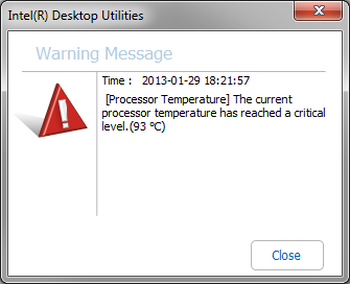
The use of calculation power of the GPU can also develop into a trouble. In comparison to games or other graphic tasks, mining utilizes all cores of your GPU at the same time. Such a load escalates the GPU wearout pretty much. The productivity losses may reach 25-30% in only several months. Sure, when you realise the issue quickly, the chances of severe hardware harm is pretty low. But the greatest strategy is to eliminate the hazard immediately.
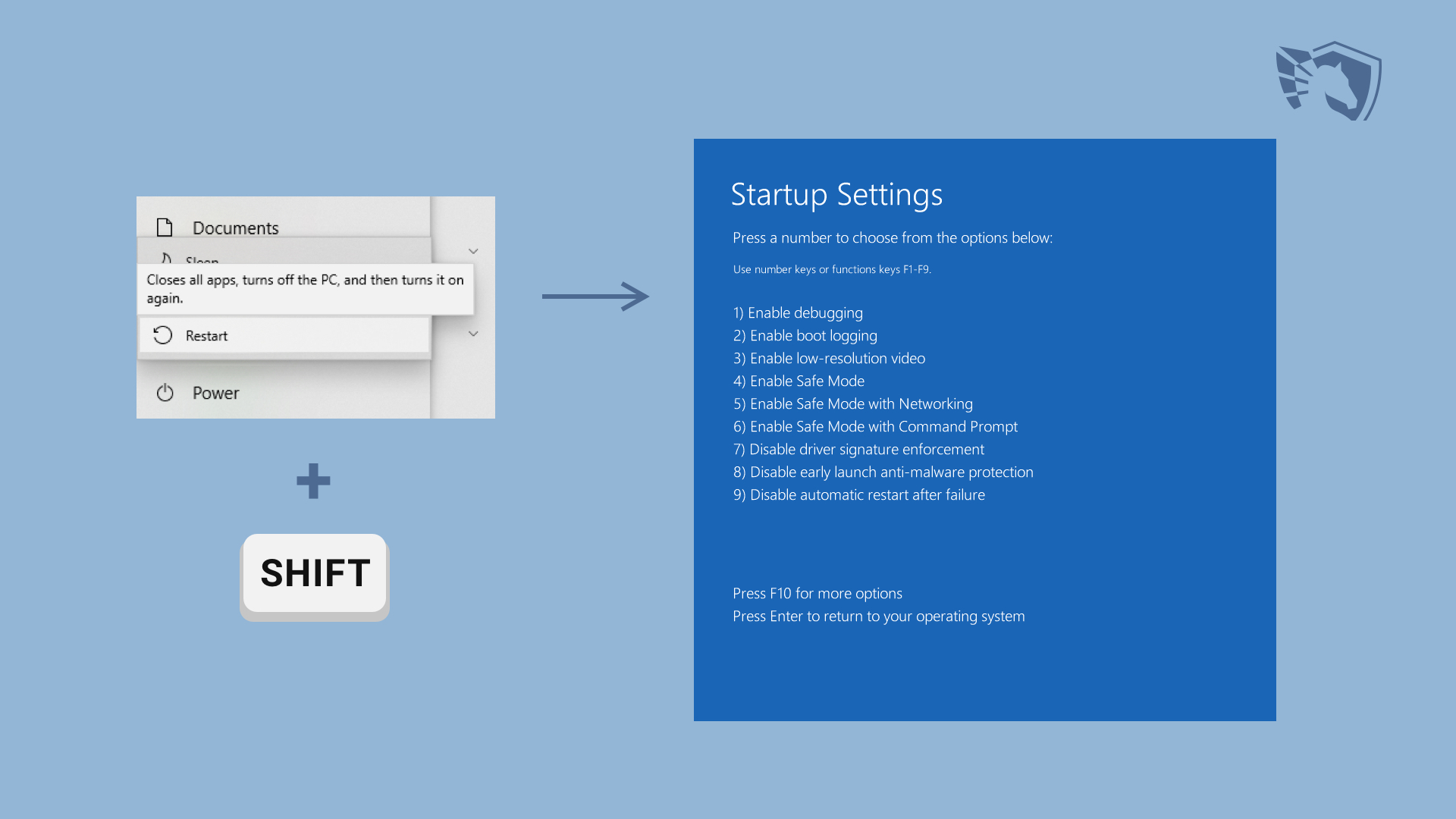
How to remove the Xmr.exe virus?
Trojan-miners, just like any trojan viruses, can simulate a certain program. Xmr.exe attempts to resemble a piece of usual app that runs in the background, expecting that low-skilled PC users will believe that this task comes from system ones. However, before starting its activities, it makes numerous changes to your system – primarily to perform all its actions accurately. Those adjustments are concentrated in the Registry, Group Policies, and also system configuration files. Returning all of these alterations by hand can barely be done without the possibilities of damaging something or missing a couple of the Xmr.exe components.
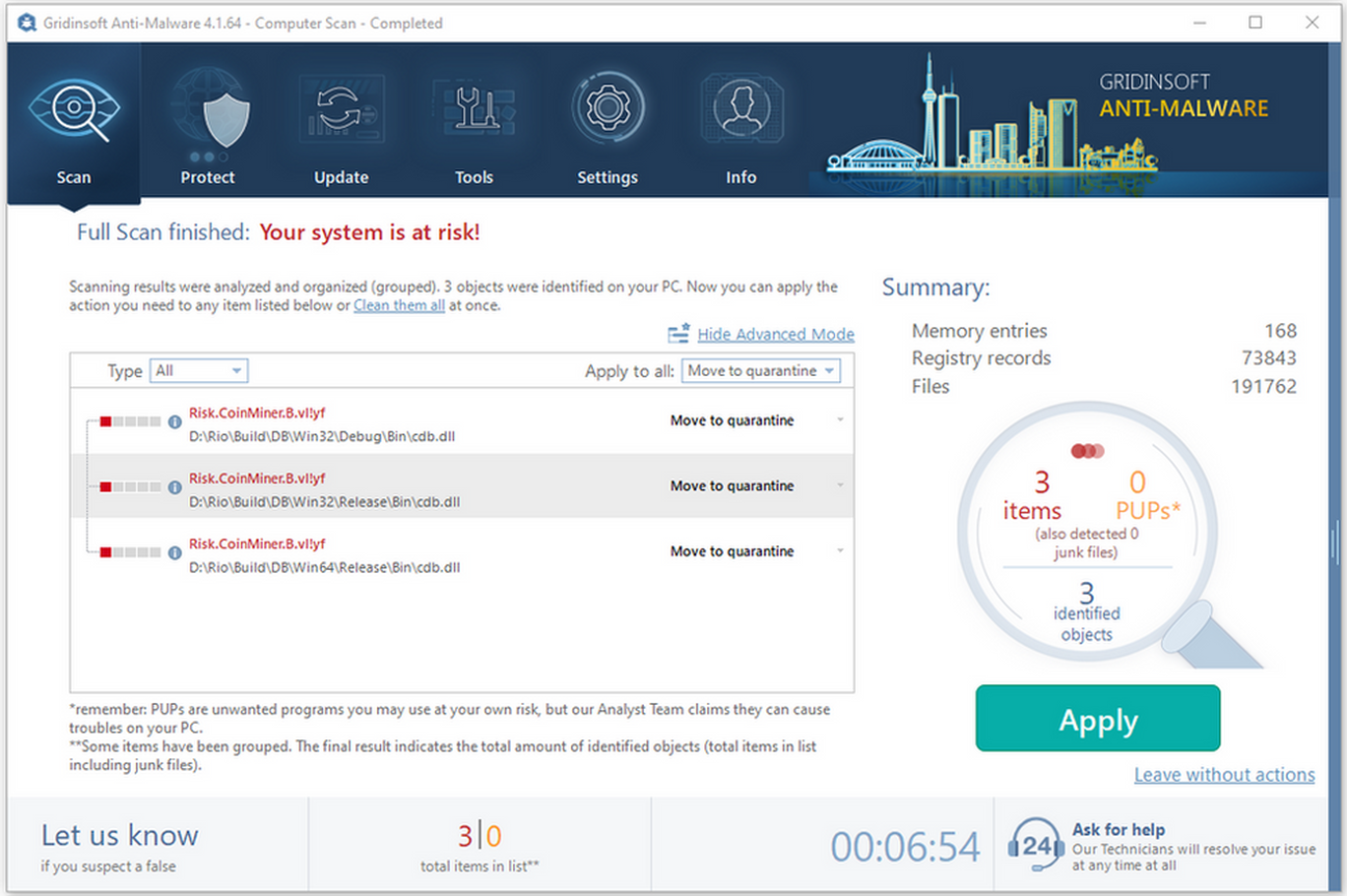
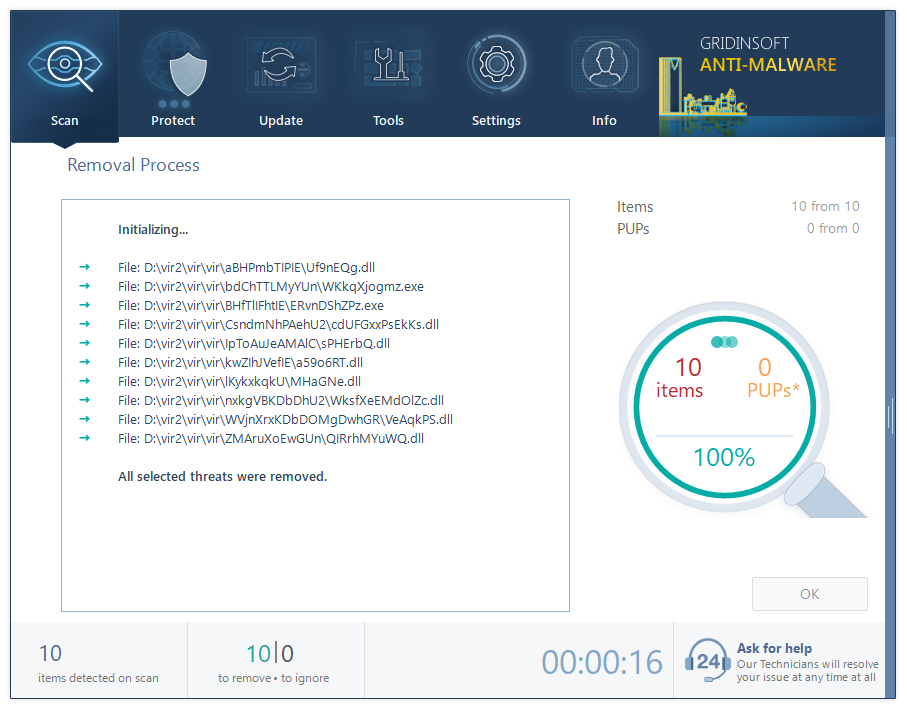
The best way to eliminate the Xmr.exe coin miner is to make use of anti-malware program. Well-designed programs can both get rid of the malware and correct the system components that were damaged. However, not each antivirus will fit. Microsoft Defender, that is present in the system by default and chosen by a lot of people will likely struggle to clear away the Xmr.exe virus. Main explanation for such a complication is the fact that Xmr.exe, similar to most of coin miners, disables the Defender via one of its exposures even before being launched. That’s why I ‘d recommend you to use GridinSoft Anti-Malware. This security solution is not vulnerable to malware intrusions, and can both remove the virus and also revert all adjustments done by it.

GridinSoft Anti-Malware Review, How to get free trial?, EULA, and Privacy Policy.
Removing the Xmr.exe virus with GridinSoft Anti-Malware