Secureworks found that the operators of the TrickBot Trojan seem to have decided to tackle SIM swap attacks. To do this, the TrickBot operators steals users’ PINs and their accounts on the networks of large mobile operators, including Sprint, T-Mobile and Verizon Wireless.
It is emphasized that TrickBot with its functionality is not a separate strain; all active versions of this Trojan received such updates.Recalling that the issue of SIM swap in recent years has been talked more and more often. The essence of such a fraudulent scheme is that the offender takes control of the SIM card and the number of his victim (as a rule, contacting the representatives of the mobile operator and applying social engineering, but other scenarios are possible).
As a result, the attacker gains full control over the victim’s number and all the services to which it is attached (including bank accounts, e-mail, and much more), as well as one-time passwords, two-factor authentication codes, and so on.
“The situation is deteriorating significantly due to the fact that TrickBot works according to the access-as-a-service model, that is, the trojan’s operators allow other hack groups to place the malware on computers infected with TrickBot. Thanks to this, TrickBot authors have already established contacts with other criminal groups, and this can be used to quickly exchange or sell collected data about mobile users”, – say Secureworks researchers.
According to researchers, TrickBot began to intercept traffic for the Verizon Wireless login page on August 5, 2019, while it began adding two new PIN fields to the Verizon standard login form. This modification is easily overlooked, as Verizon usually does not request a PIN for its website.
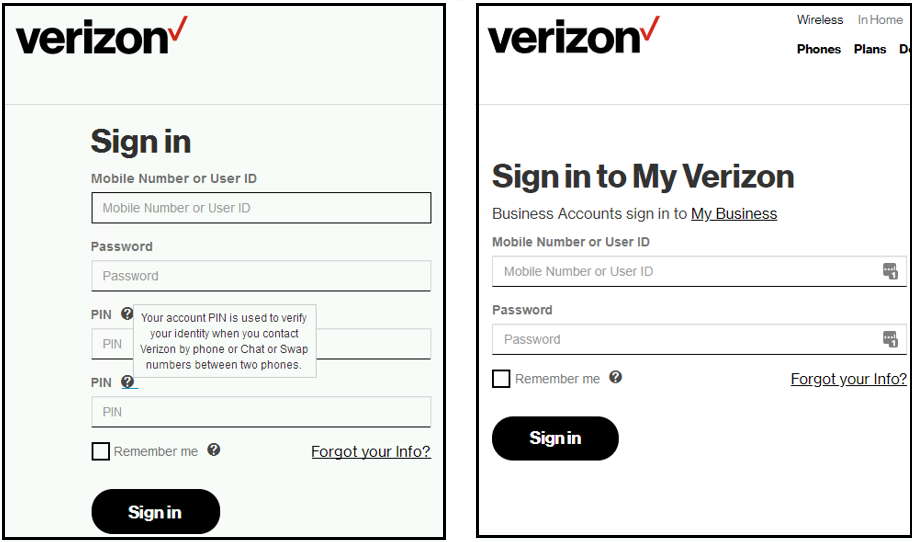
For T-Mobile and Sprint, for which TrickBot began to intercept traffic from August 12 and August 19, everything looks a little different. Instead of adding a separate fake field for entering a PIN code, the Trojan adds this field as a separate page that appears after a successful login, as shown below.
Read also: The new version of the banking Trojan TrickBot “kicks off” Windows Defender
Even worse, today TrickBot is one of the most active threats. Therefore, even if the user does not become a victim of a SIM swap attack, he may soon be infected with something else, for example, a miner, malware, stealing passwords from a browser, or ransomware.
Mitigation:
Secureworks researchers recommend that organizations use time-based one-time password (TOTP) multi-factor authentication (MFA) rather than SMS MFA when feasible. Similarly, telephone numbers should not be used as password reset options on important accounts. Enabling a PIN on mobile accounts remains a prudent anti-fraud measure that requires an attacker to possess an additional piece of information about their intended victim.
